
 Data Structure
Data Structure Networking
Networking RDBMS
RDBMS Operating System
Operating System Java
Java MS Excel
MS Excel iOS
iOS HTML
HTML CSS
CSS Android
Android Python
Python C Programming
C Programming C++
C++ C#
C# MongoDB
MongoDB MySQL
MySQL Javascript
Javascript PHP
PHP
- Selected Reading
- UPSC IAS Exams Notes
- Developer's Best Practices
- Questions and Answers
- Effective Resume Writing
- HR Interview Questions
- Computer Glossary
- Who is Who
Biometric Identification Techniques
The word “Biometrics” means “life measurement” which is usually related to the use of distinctive physiological characteristics to identify an individual. A biometric system is a pattern recognition system which makes a personal identification by determining the authenticity of a specific physiological or behavioral characteristic possessed by the user.
Biometric technologies are defined as the “automated method of identifying or authenticating the identity of a human based on physiological or behavioral characteristics”. A number of biometric technologies have developed and are used to authenticate the person’s identity.
Common examples are
- Fingerprint scanning
- Retinal scanning
- Facial recognition and
- Voice analysis
Why only Biometrics!!!
Biometrics offers unique benefits for identifying human beings. Tokens, Photo ID cards can be lost, stolen, duplicated or left at home, Passwords can be forgotten shared or observed but Biometrics holds the promise of fast, easy-to-use, accurate, reliable, and less expensive authentication for a variety of applications.
The biometric identification techniques replaces the token recognition system where a person is verified using his license or passcodes and preferred over traditional passwords and PIN-based methods.
Some of the known Biometric identification techniques are mentioned below
Fingerprint Recognition
It is one of the oldest technologies of biometric recognition in which the ridges and the furrows in the finger are used as the identifying trait since it is immutable.

It uses the fingerprint scanner to get an image of user’s finger. The user simply places the finger on a glass plate and a CCD (charged couple device) camera takes a picture. Before matching the print to pre-scanned images, the scanner processor makes sure the CCD has captured a clear image. It examines the average pixel darkness and rejects the scan if the overall image is too dark or too light.
If the image is rejected, the scanner adjusts the exposure time to let in more or less light and then tries the scan again. If the processor finds that the image is crisp and properly exposed, it proceeds to compare the captured fingerprint with fingerprints on file.
There are a number of different ways to get an image of user’s finger. The most common methods today are optical scanning and capacitance scanning.
Advantages
- High accuracy.
- Highly Economical.
Disadvantages
- Users involved in heavy manual labor can have the ridges and furrows in the finger changed.
- Dirty and marked fingers have a bad impact which might increase the rate of rejection.
Voice or Sound Recognition
Voice of a human is one more attribute which is unique.
In this technique, the user speaks into the microphone, and an analog-to-digital converter (ADC) creates digital sound files for the VR program to work with. Then the VR programs accept the digital recording and parse it into small, recognizable speech bits called phonemes.

Once the program has identified the phonemes, it begins a complex process of identification and analysis, comparing each string of recorded phonemes against the one recorded in its memory. It then accesses its internal database and pairs up the recorded phonemes with the most equivalent texts.
Finally, the VR program provides the output on the screen.
Advantages
- Since only the voice is taken as input, the person’s hand is free (helps disabled).
- Flexible.
- Can also be used to control the simulation.
Disadvantages
- An intruder can use a recorded voice.
- It is less accurate when there is a lot of noise in the background.
Palm Vein Recognition
In this, a vein in the palm is used as an identification trait. In this technique, the user simply put his hand above the sensor for less than a second. The sensor then records and examines the vein pattern of the user, which stays unique over time, to provide a positive ID.
It gives each test taker a single record that is virtually impossible to fake and prevents people from testing under assumed identities.
Advantages
- Quick and simple.
- Fast and highly accurate.
- No obstruction involved between the palm and sensor.
Disadvantages
- The response time might be a complex issue.
IRIS Recognition
The iris is unique to a human being. No two humans can have the same iris pattern even identical twins have different iris patterns. The iris pattern of right eye differs from the left eye. Usually, the left eye is used.
It uses camera technology in which the iris is exposed to subtle infrared rays. The image of the eye is captured and iris scanner analyzes the features in the iris which have more than 200 points that can be used for comparison, including rings, furrows and freckles. Patterns are drawn and then matched with that of the user.
It is extensively used in airports as a substitute for the passport, computer login, ATMs, access to buildings and database access.
Advantages
Iris is flat which makes it easily predictable. The false match rate is very low
- Most accurate and robust biometric technology.
- Iris has a fine texture which remains stable always.
Disadvantages
- The amount of light in the scanner should be taken care of.
- The distance between the scanner and the person’s eye can be bothersome.
- There are intruders who have used the high-quality image instead of the real iris.
Retina Scan Recognition
It is similar to iris recognition but more stable than iris recognition as it is less exposed to external environment.

It uses a low-intensity light source and a delicate sensor to scan the pattern of blood vessels at the back of the retina, a pattern unique to each individual. This pattern is then matched against the one existing in the database.
During a retinal scan, the user must remove glasses, stare at a specific point, and hold their head still for the 10-15 seconds it takes to complete the scan.
Advantages
- Highly reliable.
- Speedy results as it verified very quickly
Disadvantages
- Expensive and not very user-friendly.
- Difficult to place the eye in front of the scanner.
Hand Geometry
In this technique, the geometric shape of the hand – size of the palm, length and width of the fingers, the distance between the knuckles, etc are used.
It uses the geometry scanner, the user simply puts his or her hand onto a platen which consists of 5 pegs that help the user to position their fingers properly.
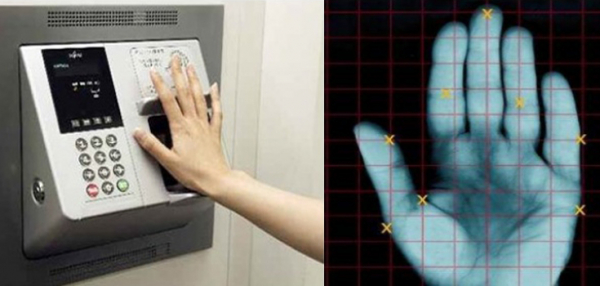
Two basic types of pictures of the hand are captured:
- An image of the top of the hand; and
- An image of the side of the hand.
The verification template is compared against the one existing in the database, in the exact same fashion as fingerprint recognition. The verification phase can be accomplished in just under one second.
It is used by different companies for their buildings and even government agencies to verify who is entering.
Advantages
- Relatively easy to use and inexpensive.
- Good performance system with complex background.
Disadvantages
- The irrelevant object might overlap with the hand.
- Not ideal for growing children.

