Article Categories
- All Categories
-
 Data Structure
Data Structure
-
 Networking
Networking
-
 RDBMS
RDBMS
-
 Operating System
Operating System
-
 Java
Java
-
 MS Excel
MS Excel
-
 iOS
iOS
-
 HTML
HTML
-
 CSS
CSS
-
 Android
Android
-
 Python
Python
-
 C Programming
C Programming
-
 C++
C++
-
 C#
C#
-
 MongoDB
MongoDB
-
 MySQL
MySQL
-
 Javascript
Javascript
-
 PHP
PHP
EPC Gen 2 Tag Identification Layer
Tag identification layer of Electronic Product Code (EPC) Gen 2 lays down the method by which the readers can receive the identifiers from the tags. EPC Gen 2 (second generation) RFID (Radio Frequency Identification) network has two main components, tags and readers. RFID tags are affixed on objects with EPC encoded on them for identification. EPC helps to check identities of objects like inventory, assets and people, and track them. Readers are the intelligent part of the system that tracks the tags. The tag identification layer addresses the multiple access problem of getting messages from unknown number of tags.
Working Principle
In an EPC Gen 2 RFID network, readers are installed at fixed points that track the tags on mobile objects when they are within range. For tracking and identification, the tags send messages carrying their embedded EPC to the reader.
The reader broadcasts a query message to all the tags for initiating the process. If more than one tag start to send their EPC identifiers simultaneously, collision will occur. This is called the multiple access problem. The problem is more pronounced since the tags are unable to hear other transmissions and the number of available tags is not known by the reader beforehand.
The method used to solve the problem is similar to slotted ALOHA. The time is divided into discrete intervals called slots. A reader or tag can send their message only at the start of a slot.
In slot 0, the reader broadcasts a Query message to initiate the process. It then sends a QRepeat message at each subsequent slot. On receiving the QRepeat message, the tags pick up a random slot to send its message. At first it sends a short 16 – bit number in an RN16 message. If collision doesn’t occur, the reader sends an acknowledgement (ACK) message. The tag then acquires the next slot and sends its EPC identifier.
The process is shown in the following diagram −
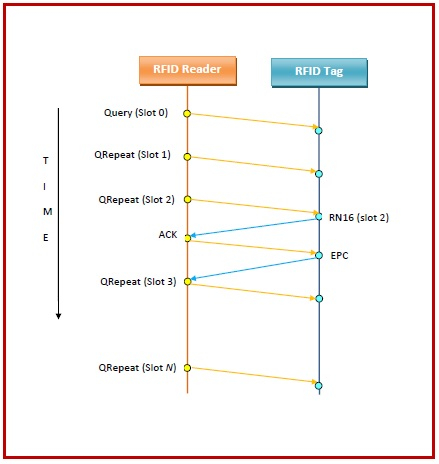
A main issue in the above method is to adjust the number of slots so as to keep good performance while avoiding collisions. Depending upon the number of slots without response or the number of slots with collisions, the reader can adjust the range of slots by issuing a QAdjust message.
Apart from identifying the tags, the reader can perform other tasks like −
- Write data to the tags
- Group tags according to their types and acquire collective information
- Sort out tags that are not authorized


