
- Amazon RDS - Home
- Amazon RDS - Overview
- Amazon RDS - Environment
- Amazon RDS - Interfaces
- Amazon RDS - DB Instances
- Amazon RDS - DB Storages
- Amazon RDS - MS SQL features
- Amazon RDS - MS SQL creating DB
- Amazon RDS - MS SQL Connecting to DB
- Amazon RDS - MS SQL DB Export Import
- Amazon RDS - MS SQL DB with SSL
- Amazon RDS - MS SQL DBA Tasks
- Amazon RDS - Oracle Features
- Amazon RDS - Oracle Creating DB
- Amazon RDS - Oracle Connecting to DB
- Amazon RDS - Oracle DB Data Import
- Amazon RDS - Oracle DBA Tasks
- Amazon RDS - MariaDB Features
- Amazon RDS - MariaDB Creating DB
- Amazon RDS - MariaDB Connecting to DB
- Amazon RDS - MariaDB Data Import
- Amazon RDS - PostgreSQL Features
- Amazon RDS - PostgreSQL creating DB
- Amazon RDS - PostgreSQL Connecting to DB
- Amazon RDS - PostgreSQL Data Import
- Amazon RDS - MySQL Features
- Amazon RDS - MySQL Creating DB
- Amazon RDS - MySQL Connecting to DB
- Amazon RDS - MySQL DB Export Import
- Amazon RDS - MySQL DBA Tasks
- Amazon RDS - Multi-AZ Deployments
- Amazon RDS - DB Snapshots
- Amazon RDS - DB Monitoring
- Amazon RDS - Event Notifications
- Amazon RDS - DB Access Control
Amazon RDS - MS SQL DB with SSL
To protect data from being viewed by unintended parties, we can use connection encryption between the client application and the RDS DB instance. Encryption is available in all AWS regions and for all the DB types supported by AWS RDS. In this chapter we will see how encryption is enabled for MSSQL Server.
There are two ways to enable encryption.
Force SSL for all connections this happens transparently to the client, and the client doesn't have to do any work to use SSL.
Encrypt specific connections this sets up an SSL connection from a specific client computer, and you must do work on the client to encrypt connections.
Force SSL
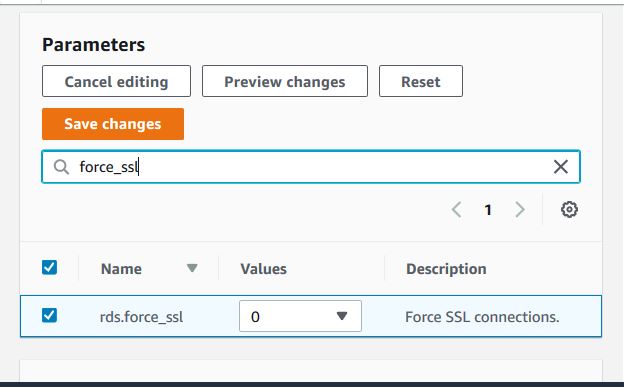
In this approach we force all the connections form the DB client to use SSL. This is done by using the rds.force_ssl parameter. Set the rds.force_ssl parameter to true to force connections to use SSL. As it is a static parameter, we must reboot your DB instance for the change to take effect. The below diagram shows how to reset the value by visiting the DB parameters settings page to set the value for rds.force_ssl parameter.
Encrypting Specific Connections
We can encrypt connections from specific client computers only to the RDS DB Instance. In order to do this, we need to install certificate on the client computer. Below are the steps to install the certificate.
Step-1
Download the certificate to the client computer from here .
Step-2
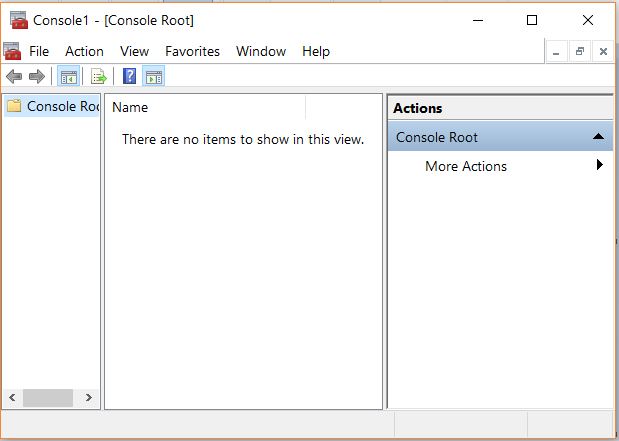
Follow the path Windows -> Run -> type MMC and enter. It opens the following window.
Step-3
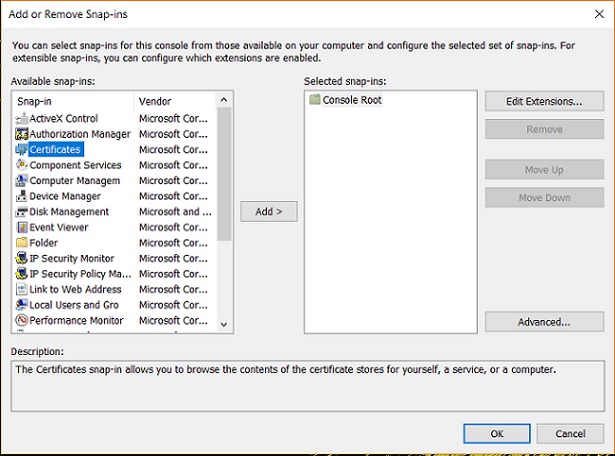
In the Add or Remove Snap-ins dialog box, for Available snap-ins, select Certificates, and then choose Add.
Step-4
Follow the Path Computer Account -> Local Computer -> Finish.
Step-5
In the MMC console, expand Certificates, open the context (right-click) menu for Trusted Root Certification Authorities, choose All Tasks, and then choose Import.

Step-6
Select the .pem file downloaded in the previous step and finish the import wizard by choosing the default values and clicking next.
Step-7
We can see the certificate installed as below.

Step-8
When connecting to AWS RDS MSSQL Db instance using SSMS, expand the options tab and choose Encrypt connection.

Now the client connection to RDS from this computer will be encrypted.