- Wireless Security - Concepts
- Wireless Security - Access Point
- Wireless Security - Network
- Wireless Security - Standards
- Wi-Fi Authentication Modes
- Wireless Security - Encryption
- Wireless Security Break an Encryption
- Wireless Threats
- Wireless - Access Control Attacks
- Wireless Security - Integrity Attacks
- Wireless - Confidentiality Attacks
- Wireless Security - DoS Attack
- Wireless Security - Layer 1 DoS
- Wireless Security - Layer 2 DoS
- Wireless Security - Layer 3 DoS
- Authentication Attacks
- Rogue Access Point Attacks
- Client Misassociation
- Misconfigured Access Point Attack
- Ad-Hoc Connection Attack
- Wireless Hacking Methodology
- Wireless Traffic Analysis(Sniffing)
- Launch Wireless Attacks
- Crack Wireless Attacks
- Wireless Security Tools
- Wireless Security RF Monitoring Tools
- Wireless Security - Bluetooth Hacking
- Wireless Security - Bluetooth Stack
- Wireless Security - Bluetooth Threats
- Wireless - Bluetooth Hacking Tools
- Wireless Security - Bluejack a Victim
- Wireless Security - Tools
- Wireless Security Pen Testing
- Wi-Fi Pen Testing
- Pentesting Unencrypted WLAN
- WEP Encrypted WLAN
- Pentesting WPA/WPA2 Encrypted
- Pentesting LEAP Encrypted WLAN
- Wireless Security Useful Resources
- Wireless Security - Quick Guide
- Wireless Security - Useful Resources
- Wireless Security - Discussion
Wireless Security - Traffic Analysis
A process of wireless traffic analysis may be very helpful in forensic investigations or during troubleshooting and of course this is a great way of self-study (just to learn how applications and protocols inter communicate with each other). In order to the traffic analysis to be possible, first, this traffic needs to be somehow collected and this process is known as traffic sniffing. The most commonly used tools for traffic sniffing are Kismet and Wireshark. Both these programs provide a version for Windows as well as Linux environments.
For the purpose of penetration testing and hacking of wireless networks, the type of data, that is valuable to collect are BSSID, WEP IV, TKIP IV, CCMP IV, EAP 4-way handshake exchange, wireless beacon frames, MAC addresses of communicating parties, etc. A lot more is available to you in the dump of the wireless traffic. Most of the information you would get, would be used in all the attacks presented in the last chapter. They could be (for example) used as the input to offline brute-force attacks, in order to break encryption and authentication models used in the WLAN deployment.
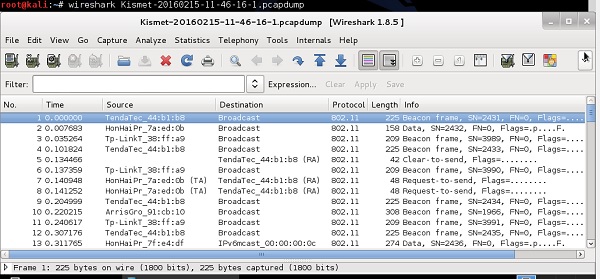
Usage of Wireshark in both Windows and Linux are very intuitive - both environments provide a GUI that looks the same for both systems. When the program starts, you only need to indicate the physical interface, that would be used for traffic sniffing (you can select any interface, either wired one or wireless one), and then proceed with traffic sniffing. Example of wireless packets collected by a wireless card is shown in the following screenshot.
The layout of the output is always the same - going from the top, you have −
Filter Field − Wireshark is equipped with a very good filtering tool that allows limiting the real-time traffic output. It is extremely useful, when you need to extract particular flows (between a particular MAC addresses or between particular IP addresses) out of hundreds of packs coming every second from all the wireless clients in the surrounding.
Traffic Output − In this section, you can see all the packets showing up, that were sniffed on the wireless interface, one by one. In this part of the output, you can see only a basic summary of the traffic characteristics like SRC/DST MAC Addresses, Protocol (Wi-Fi 802.11 in this case) and a brief info about a packet.
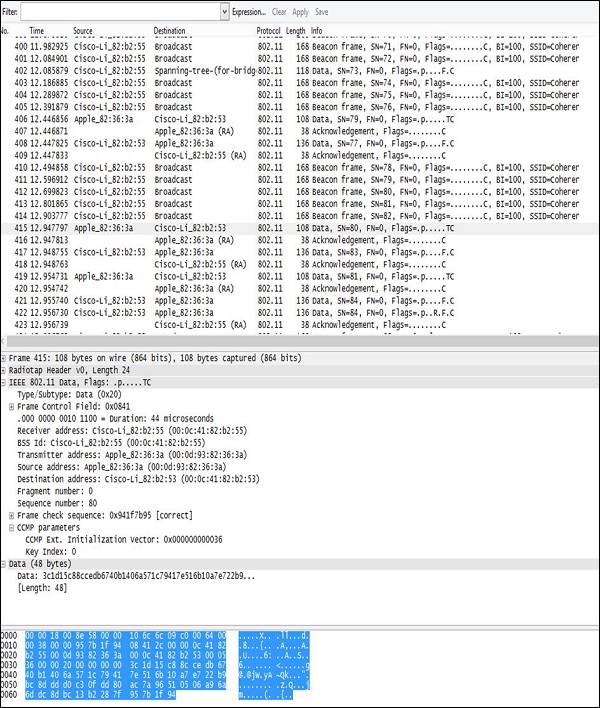
Decoded Parameters of the Data − This section lists all the fields existing in a frame (all the headers + data). Using an example dump, we can see, that some set of information is in the form of unreadable data (probably encrypted), and in 802.11 header you can find CCMP information (it confirms that traffic is AES encrypted), so it must be WPA2 Wi-Fi network.
Hex Dump − The Hex Dump is exactly the same information you have above in "decoded parameters of the data" but in a hexadecimal format. The reason for that is that, hexadecimal representation is the original way the packet looks like, but Wireshark has thousands of "traffic templates", which are used to map specific HEX values to a known protocol field. For example, in a 802.11 header the bytes from 5 to 11 are always the source of a MAC address of the wireless frame, using the same pattern mapping, Wireshark (and other sniffers) can re-construct and decode static (and well known) protocol fields.
You may save all your traffic dumps using the common .pcap format that could be later used as the input to, for example, python scripts which perform some advanced operations on the collected traffic (for example cracking the encryption models).
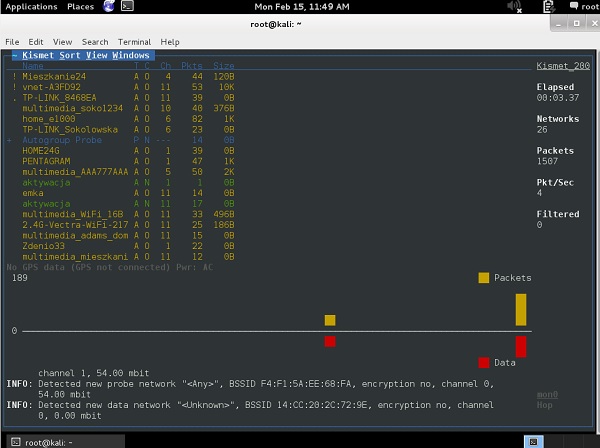
The other tool, that you should aware of, is Kismet. As soon as you start your Kismet tool and specify the mon0 interface, it will list all the SSID detected in your environment.
During the time Kismet is running, all the wireless packets are collected and stored in the .pcap files. When you quit a program, you get a message, that all the wireless packet dumps have been saved and you can access them afterwards.
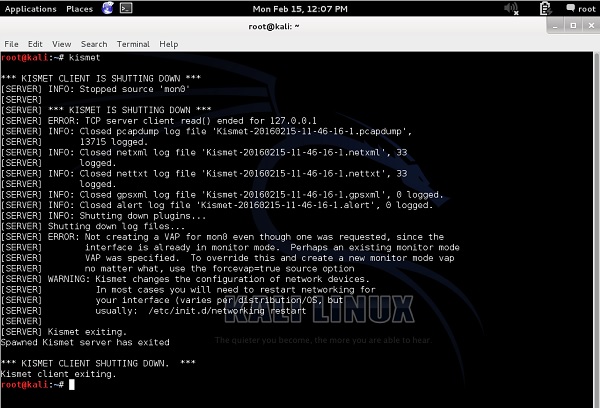
In the example presented above, all the packet dumps have been stored in the binary files (they are not in a readable format, when you open those files with "more" or "vi" or "nano", etc..).
To open them correctly, you have to use Wireshark (again!).