
- Wireless Security - Concepts
- Wireless Security - Access Point
- Wireless Security - Network
- Wireless Security - Standards
- Wi-Fi Authentication Modes
- Wireless Security - Encryption
- Wireless Security Break an Encryption
- Wireless Threats
- Wireless - Access Control Attacks
- Wireless Security - Integrity Attacks
- Wireless - Confidentiality Attacks
- Wireless Security - DoS Attack
- Wireless Security - Layer 1 DoS
- Wireless Security - Layer 2 DoS
- Wireless Security - Layer 3 DoS
- Authentication Attacks
- Rogue Access Point Attacks
- Client Misassociation
- Misconfigured Access Point Attack
- Ad-Hoc Connection Attack
- Wireless Hacking Methodology
- Wireless Traffic Analysis(Sniffing)
- Launch Wireless Attacks
- Crack Wireless Attacks
- Wireless Security Tools
- Wireless Security RF Monitoring Tools
- Wireless Security - Bluetooth Hacking
- Wireless Security - Bluetooth Stack
- Wireless Security - Bluetooth Threats
- Wireless - Bluetooth Hacking Tools
- Wireless Security - Bluejack a Victim
- Wireless Security - Tools
- Wireless Security Pen Testing
- Wi-Fi Pen Testing
- Pentesting Unencrypted WLAN
- WEP Encrypted WLAN
- Pentesting WPA/WPA2 Encrypted
- Pentesting LEAP Encrypted WLAN
- Wireless Security Useful Resources
- Wireless Security - Quick Guide
- Wireless Security - Useful Resources
- Wireless Security - Discussion
Wireless Security - Access Control Attacks
It is not a secret that wireless networks are much more vulnerable than their wired equivalents. In addition to protocol vulnerabilities itself, it is a "wireless" shared medium that opens those kind of networks to completely new set of attack surfaces. In the consecutive sub-chapters, I will try to introduce many of the aspects (or rather threats) of wireless communications, that may be exploited by the malicious 3rd party.
Access Control Attacks
The concept of access control is all about controlling, who have access to the network, and who does not. It prevents malicious 3rd parties (unauthorized) from associating to the wireless network. The idea of access control is very similar to an authentication process; however, those two concepts are complementary. Authentication is most often based on a set of credentials (username & password) and access control may go beyond that and verify other characteristics of the client user or client user's device.
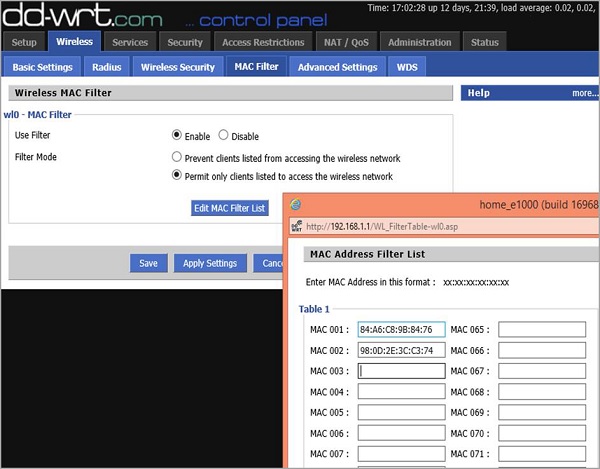
Very well-known access control mechanism used in wireless networks is based on MAC address whitelisting. The AP stores a list of authorized MAC addresses that are eligible to access the wireless network. With tools available nowadays, this security mechanism is not a very strong one, since MAC address (hardware address of the wireless client's chipset) may be spoofed very simply.
The only challenge is to find out what MAC addresses are allowed by AP to authenticate to the network. But since wireless medium is a shared one, anyone can sniff the traffic flowing through the air and see the MAC addresses in the frames with valid data traffic (they are visible in the header that is not encrypted).
As you can see in the following image, on my home router, I have set two devices to be able to communicate with the AP, by specifying its MAC addresses.
This is the information that the attacker does not have in the beginning. However, since wireless medium is "open" for sniffing, he may use Wireshark to listen to those devices that are connected and talking to the AP at a particular time. When you start a Wireshark to sniff over the air, you will most likely get hundreds of packets per second, therefore, it is wise to make use of efficient filtering rules in Wireshark. The type of filter I have implemented is −
(wlan.fc.type_subtype == 0x28) && (wlan.addr == 58:6D:8F:18:DE:C8)
The first part of this filter says to Wireshark that it should only look at data packets (not beacon frames or other management frames). It is a subtype 0x28 AND ("&&") one of the parties should be my AP (it has MAC address of 58:6D:8F:18:DE:C8 on the radio interface).
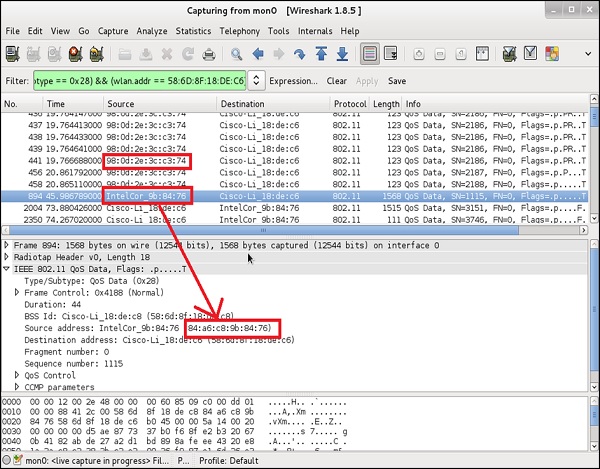
You can notice that there are two devices that are exchanging data packets with AP are the ones that I as an administrator specifically allowed on the MAC filtering earlier. Having those two, the only piece of configuration you as an attacker have to do is to locally change the MAC address of your wireless card. In this example, I will use a Linux based tool (but there are tons of other ones for all possible Operating Systems) −
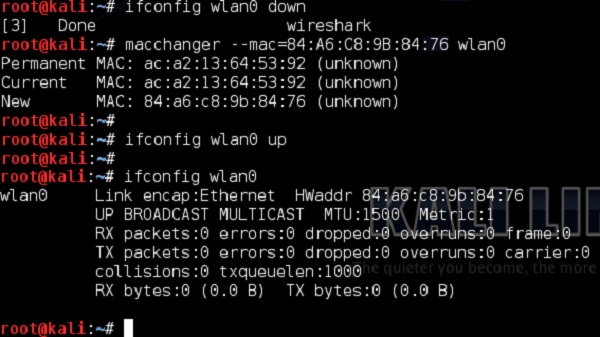
This was a simple approach to bypass the MAC filtering based access control. Nowadays, the methods to perform access control are much more advanced.
Specialized authentication servers can differentiate whether a particular client is a PC produced by HP, IPhone from Apple (what kind of IPhone) or some other wireless clients, only by looking at the way how wireless frames from a particular client looks like and comparing them to the set of "baselines", known for particular vendors. However, this is not something you may see on the home networks. Those solutions are quite expensive, and require more complex infrastructure integrating multiple types of servers - most likely met in some of the corporate environments.