
- Wireless Security - Concepts
- Wireless Security - Access Point
- Wireless Security - Network
- Wireless Security - Standards
- Wi-Fi Authentication Modes
- Wireless Security - Encryption
- Wireless Security Break an Encryption
- Wireless Threats
- Wireless - Access Control Attacks
- Wireless Security - Integrity Attacks
- Wireless - Confidentiality Attacks
- Wireless Security - DoS Attack
- Wireless Security - Layer 1 DoS
- Wireless Security - Layer 2 DoS
- Wireless Security - Layer 3 DoS
- Authentication Attacks
- Rogue Access Point Attacks
- Client Misassociation
- Misconfigured Access Point Attack
- Ad-Hoc Connection Attack
- Wireless Hacking Methodology
- Wireless Traffic Analysis(Sniffing)
- Launch Wireless Attacks
- Crack Wireless Attacks
- Wireless Security Tools
- Wireless Security RF Monitoring Tools
- Wireless Security - Bluetooth Hacking
- Wireless Security - Bluetooth Stack
- Wireless Security - Bluetooth Threats
- Wireless - Bluetooth Hacking Tools
- Wireless Security - Bluejack a Victim
- Wireless Security - Tools
- Wireless Security Pen Testing
- Wi-Fi Pen Testing
- Pentesting Unencrypted WLAN
- WEP Encrypted WLAN
- Pentesting WPA/WPA2 Encrypted
- Pentesting LEAP Encrypted WLAN
- Wireless Security Useful Resources
- Wireless Security - Quick Guide
- Wireless Security - Useful Resources
- Wireless Security - Discussion
Wireless Security - Crack Wireless Attacks
Whenever you might need to "crack" a wireless network, the task is about cracking the encryption, authentication or hash algorithm to derive some kind of secret password.
There is a bunch of ways you may achieve it −
You can try to break the encryption algorithm with the weaker ones. It might be doable, but to be very honest with you, now-a-days no one would use the algorithm that may be breakable, therefore, unless you are a high-class crypto analyst that would not be the way forward.
Most of the approaches would concentrate on using some kind of dictionary or brute-force attack.
Just to give you a simple idea of how this attack may be performed, imagine we have some password that "we don't know" - "MySecretPassword". In some way, we got into possession of MD5 and SHA1 signatures as shown in the following screenshot −
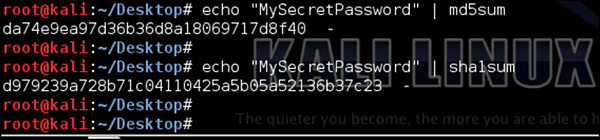
As an attacker, our goal would be to break those hash algorithms and derive the original password. There are many ready tools that might be used for this purpose; we can create our own tools as well.
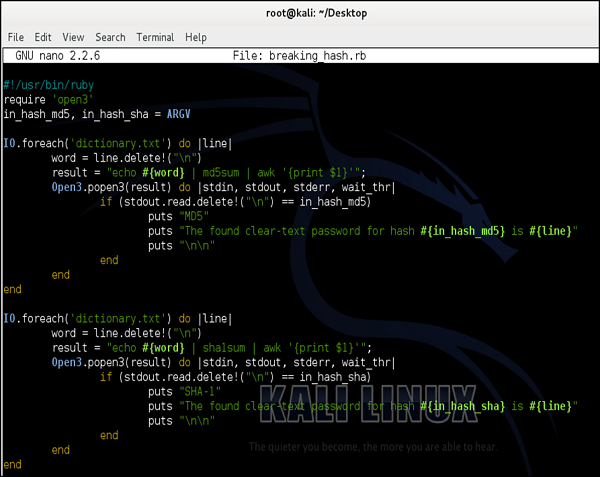
Following is a simple script (written in ruby) that could be used for dictionary (type brute-force) attack −
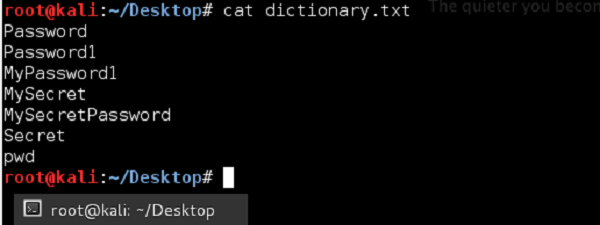
We will use a simplified dictionary file (the one I have created in few seconds) as shown in the following screenshot. Normally in real life you would use a dictionary file with hundreds of thousands of entries (it is popular to download a prepared dictionary file from the internet, you can try to find one).
The idea behind this script would be to go through each and every password, and if the match between calculated hash matches the signature, we "would sniff" from the network, it means we have found a password.
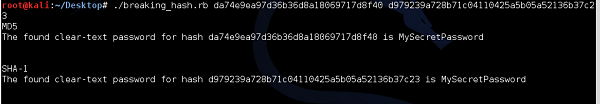
I have to state it was a simplified example, however it showed perfectly the concept itself.
During a wireless network cracking, you will most likely use a tool called aircrack-ng. It is specifically designed for cracking WEP/WPA/WPA2. In case of WPA/WPA2 cracking, it will use a dictionary attack (similar to a simplified one we presented above) with two possible dictionary types. The first type is the one that you can prepare by yourself (or download from the internet) and just reference it inside the script. The other approach is to rely on the internal airolib-ng dictionary that is the kind of internal dictionary database installed with the tool by default.
Without making any real cracking at that point, I will show how to use aircrack-ng. I will use my very small dictionary which I have created in the example above (with only 7 phrases inside, opposite to millions you would find in real dictionary file). Additionally, I will not monitor any traffic in real-time, but I will use a .pcap file with the wireless traffic I have sniffed before using the Kismet tool.
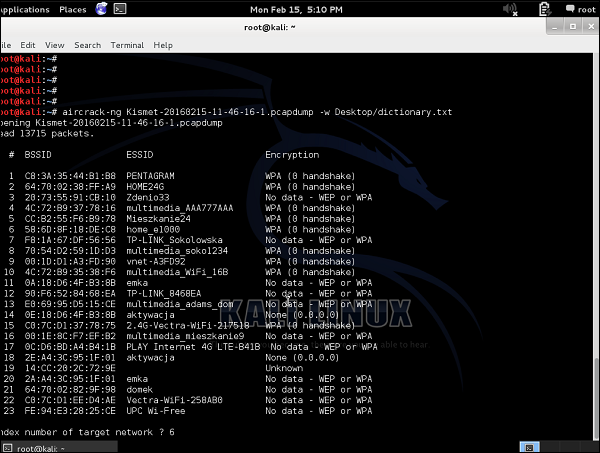
As you can see, there is a bunch of WLANs, some of them with WEP encryption, and most with WPA/WPA2. I can already say that any kind of cracking would fail in this situation because −
As for the WEP encrypted SSIDs, we don't have any traffic collected ("No data").
As for the WPA/WPA2 encrypted SSID's, we don't have any handshakes sniffed. As you remember, data from the initial 4-way handshake is the only information that can lead to cracking the network. Data packets themselves are well encrypted and resistant to our attacks.
But, imagine we want to try, I will target my own home wireless network - "Home_e1000" with index 6.
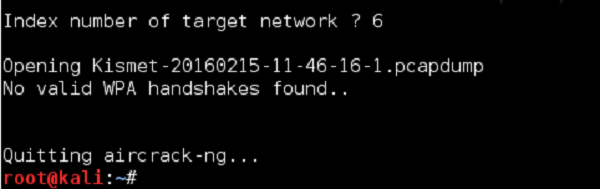
As I predicted, we have failed. Next time, I will make sure that we will not fail, and you will be able to learn how it is to win and crack the wireless network - I can tell you it's a good feeling.