
 Data Structure
Data Structure Networking
Networking RDBMS
RDBMS Operating System
Operating System Java
Java MS Excel
MS Excel iOS
iOS HTML
HTML CSS
CSS Android
Android Python
Python C Programming
C Programming C++
C++ C#
C# MongoDB
MongoDB MySQL
MySQL Javascript
Javascript PHP
PHP
- Selected Reading
- UPSC IAS Exams Notes
- Developer's Best Practices
- Questions and Answers
- Effective Resume Writing
- HR Interview Questions
- Computer Glossary
- Who is Who
What is Spoofing and what are its types?
Technically, the term "spoofing" means an attempt or attack in your network security without your knowledge pretending to be someone else.They are not to steal your data, gain access to your system, and invade your privacy.
A prevalent example of spoofing is sending mail from a false sender’s address pretending to be someone and asking them for their sensitive data or giving a link to some malicious website or app.
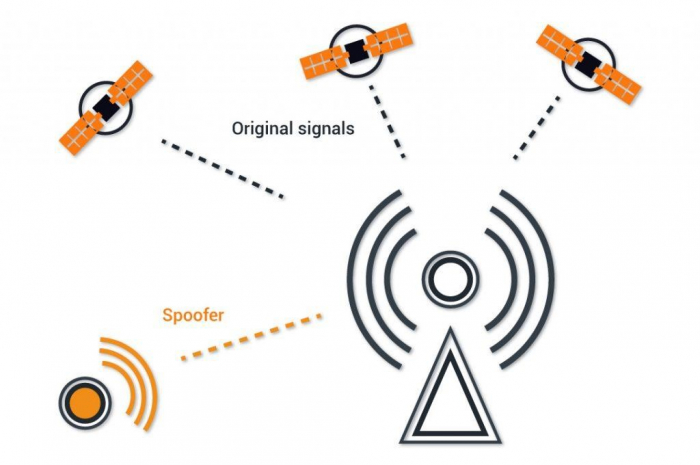
There are so many types of spoofing, but these days, these ten are the most commonly used, and hence having awareness about them might save you from the trouble −
ARP Spoofing
Here, cyber attackers use LAN with false Address Resolution Protocol (ARP) packets to make changes with the usual traffic routing process. The primary purpose here is to bind the adversary’s MAC address with the IP address of the user’s default LAN gateway, after which; all traffic is
MAC Spoofing
Here, the attacker uses the vulnerabilities of hardware drivers to modify its MAC address. In this way, the attacker pretends its device to be the one enrolled in a network. It then gains access, and from there, he makes all frauds like business email compromise (BEC), steals data, or deposit malware in the original mac id device.
IP Spoofing
As the name suggests, the user sends Internet Protocol packets, also referred to as IP packets with a falsified source address, to impersonate another system. It is primarily used to set DDoS attacks. The logic behind this is that it’s challenging for the digital infrastructure to filter such rogue packets. It can mainly be used to enter into networks that use a device’s IP address as a critical identifier.
DNS Cache Poisoning (DNS Spoofing)
Since we all know that every IP address is given some domain name and in this spoofing, hackers contort this mapping by piggybacking on known DNS servers caching their flaws. Due to which the user might go to the malicious replica of the intended domain from where hackers might gain access to the user’s system.
Email Spoofing
Here the hackers modify the email head so that the sender address appears to match a legitimate one when in reality, it is coming from an entirely different source. And in this way, the victim gives the green light to a fraudulent wire transfer without giving it a second thought.
Website Spoofing
As the name suggests here, the hackers try to copy the layout, branding, and sign-in forms of original web pages and Pair them with the DNS spoofing trick to hack the data. Sometimes backdoor tactic is also combined with this which may also lead to identity theft.
Caller ID Spoofing
Here hackers exploit loopholes in telecommunications, which show caller details you see on your phone’s screen. The attackers here try to offer a reputable brand’s logo and physical address on the incoming calls to increase your answering the phone. Here the main aim is disclosing personal info or paying non-existent bills of the hackers by the users.
Text Message Spoofing
A typical example of a text message spoofing attack is when a hacker replaces the SMS sender ID with a brand name the recipient trusts. This impersonation is done for spear phishing, data theft, etc. getting a link stating you won a lottery in the text message is also an example of text message spoofing.
Extension Spoofing
Now every operating system keeps file extensions out of sight by default, and hackers use this fact to disguise a harmful binary as a benign object with the help of a double extension.
For example, "abcd.docx.exe" will look just like a regular Word document ("abcd.docx") which will even get executed but would be malicious.Hence, this spoofing with modification in extension is known as extension spoofing.
GPS Spoofing
Here, cybercriminals may try to manipulate a user’s device’s GPS receiver into signalling inaccurate pop-ups. The logic behind it is pretty different from regular spoofing, and it is mainly done to give long-term losses to the target. For example, a CEO who is in a hurry for an important meeting with a potential business partner may take a wrong turn, only to get stuck in traffic and be late for the conference, leading to the deal getting cancelled.

