Article Categories
- All Categories
-
 Data Structure
Data Structure
-
 Networking
Networking
-
 RDBMS
RDBMS
-
 Operating System
Operating System
-
 Java
Java
-
 MS Excel
MS Excel
-
 iOS
iOS
-
 HTML
HTML
-
 CSS
CSS
-
 Android
Android
-
 Python
Python
-
 C Programming
C Programming
-
 C++
C++
-
 C#
C#
-
 MongoDB
MongoDB
-
 MySQL
MySQL
-
 Javascript
Javascript
-
 PHP
PHP
Token Passing in Bit-Map Protocol
Bit-map protocol is a collision free protocol that operates in the Medium Access Control (MAC) layer of the OSI model. It resolves any possibility of collisions while multiple stations are contending for acquiring a shared channel for transmission. In this protocol, if a station wishes to transmit, it broadcasts itself before the actual transmission. Every station gets its turn for transmission in a predefined order. A method to accomplish this is to use the method of token passing.
Token Passing Mechanism
A token is a small message that circulates among the stations of a computer network providing permission to the stations for transmission. If a station has a frame to transmit when it receives a token, it sends the frame and then passes the token to the next station; otherwise it simply passes the token to the next station.
For token passing mechanism to operate, the stations should be connected in a single ring as shown in the following diagram −
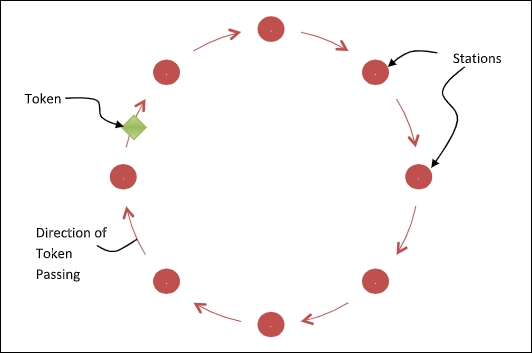
In the above configuration, passing the token comprise of receiving the token from the preceding station and transmitting to the successor station. The data flow is unidirectional in the direction of the token passing. The token may be generated by the station that wants to send the frame or the station that wants to receive the frame. In order that tokens are not circulated infinitely, they are removed from the network once their purpose is completed.
Performance Analysis
The performance is similar to conventional bit map protocol. If N number of stations are in the token ring, the waiting time of each station is (N – 1). The advantage of this protocol over bit map protocol is that all the stations have equal priority for transmission.


