
- Security Testing - Home
- Security Testing - Overview
- Security Testing - Process
- Security Testing - Malicious Software
- HTTP Protocol Basics
- HTTPS Protocol Basics
- Encoding and Decoding
- Security Testing - Cryptography
- Security Testing - Same Origin Policy
- Security Testing - Cookies
- Hacking Web Applications
- Security Testing - Injection
- Testing Broken Authentication
- Testing Cross Site Scripting
- Insecure Direct Object Reference
- Testing Security Misconfiguration
- Testing Sensitive Data Exposure
- Missing Function Level Access Control
- Cross Site Request Forgery
- Components with Vulnerabilities
- Unvalidated Redirects and Forwards
- Security Testing - Ajax Security
- Testing Security - Web Service
- Security Testing - Buffer Overflows
- Security Testing - Denial of Service
- Testing Malicious File Execution
- Security Testing - Automation Tools
Security Testing - Web Service Security
In mordern web based applications the usage of webservices is inevitable and they are prone for attacks as well. Since the web services request fetch from multiple websites developers have to take few additional measures inorder to avoid any kind of penetration by hackers.
Hands ON
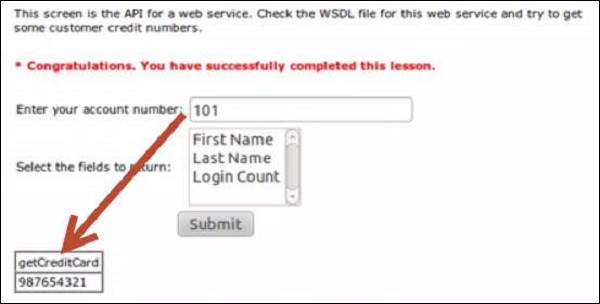
1 .Navigate to web services area of Webgoat and goto WSDL Scanning. We need to now get credit card details of some other account number. Snapshot of the scenario is as mentioned below.
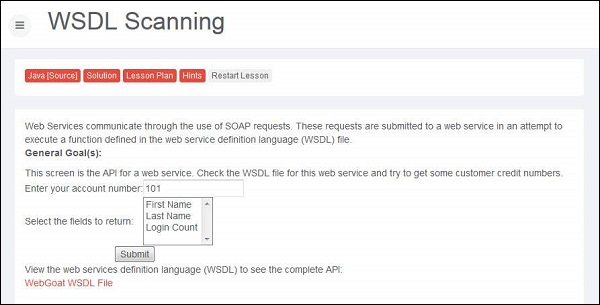
2 .If we select the first name, the 'getFirstName' function call is made through SOAP request xml.
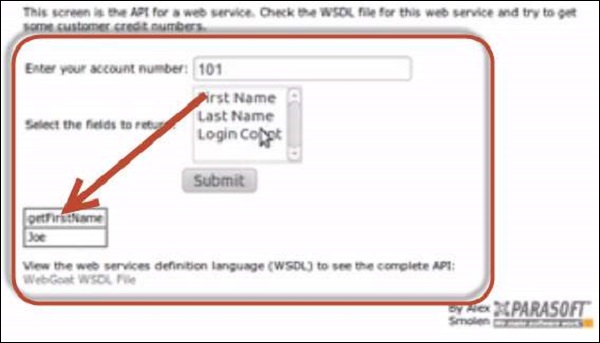
3 .By opening the WSDL, we are able to see that there is a method to retrieve credit card information as well 'getCreditCard'. Now let us tamper the inputs using Burp suite as shown below
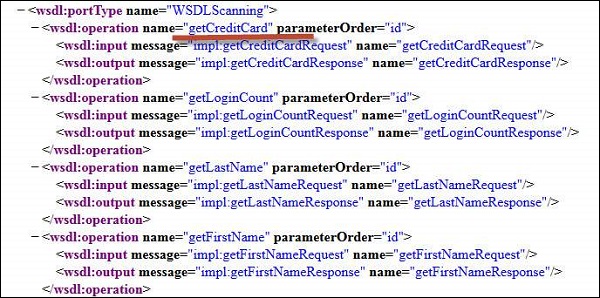
4. Now let us tamper the inputs using Burp suite as shown below
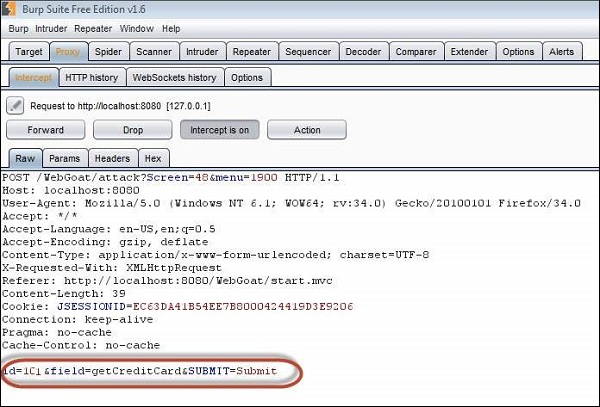
5 .We are able to get the credit card information of other users.
Preventing Mechanisms
Since SOAP messages are XML-based, all passed credentials have to be converted to text format. Hence one has to be very careful in passing the sensitive information which has to be always encrypted.
Protecting message integrity by implementing the mechanisms like checksum applied to ensure packet's integrity.
protecting message confidentiality - Asymmetric encryption is applied to protect the symmetric session keys, which, in many implementations, are valid for one communication only and are subsequently discarded.
Dev can use the following resources as a guide to prevent this flaw during development process