
- Security Testing - Home
- Security Testing - Overview
- Security Testing - Process
- Security Testing - Malicious Software
- HTTP Protocol Basics
- HTTPS Protocol Basics
- Encoding and Decoding
- Security Testing - Cryptography
- Security Testing - Same Origin Policy
- Security Testing - Cookies
- Hacking Web Applications
- Security Testing - Injection
- Testing Broken Authentication
- Testing Cross Site Scripting
- Insecure Direct Object Reference
- Testing Security Misconfiguration
- Testing Sensitive Data Exposure
- Missing Function Level Access Control
- Cross Site Request Forgery
- Components with Vulnerabilities
- Unvalidated Redirects and Forwards
- Security Testing - Ajax Security
- Testing Security - Web Service
- Security Testing - Buffer Overflows
- Security Testing - Denial of Service
- Testing Malicious File Execution
- Security Testing - Automation Tools
Security Testing - Using Components with Known Vulnerabilities
This kind of threat occurs when the Components such as libraries, frameworks used within the app almost always executes with full privileges. If a vulnerable component is exploited it makes hackers job easier to cause a serious data loss or server takeover.
Let us understand Threat Agents, Attack Vectors, Security Weakness, Technical Impact and Business Impacts of this flaw with the help of simple diagram.
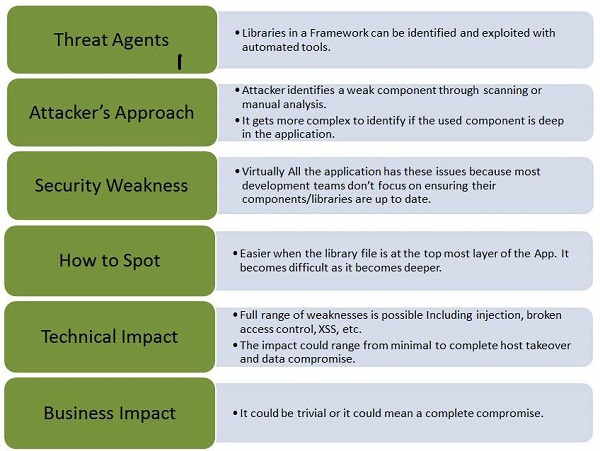
Example
Below are the examples of Using Components with Known Vulnerabilities :
Attackers could invoke any web service with full permission By failing to provide an identity token.
Remote-code execution with Expression Language injection vulnerability was introduced through the Spring Framework for Java based apps.
Preventing Mechanisms
Identify all components and the versions that are being used in the webapps not just restricted to database/frameworks.
Keeping all the components such as public databases, project mailing lists upto date.
It is important to add security wrappers around components that are vulnerable in nature.
Dev can use the following resources as a guide to prevent this flaw during development process