
- Security Testing - Home
- Security Testing - Overview
- Security Testing - Process
- Security Testing - Malicious Software
- HTTP Protocol Basics
- HTTPS Protocol Basics
- Encoding and Decoding
- Security Testing - Cryptography
- Security Testing - Same Origin Policy
- Security Testing - Cookies
- Hacking Web Applications
- Security Testing - Injection
- Testing Broken Authentication
- Testing Cross Site Scripting
- Insecure Direct Object Reference
- Testing Security Misconfiguration
- Testing Sensitive Data Exposure
- Missing Function Level Access Control
- Cross Site Request Forgery
- Components with Vulnerabilities
- Unvalidated Redirects and Forwards
- Security Testing - Ajax Security
- Testing Security - Web Service
- Security Testing - Buffer Overflows
- Security Testing - Denial of Service
- Testing Malicious File Execution
- Security Testing - Automation Tools
Security Testing - Missing Function Level Access Control
Most of the web applications verify function level access rights before making that functionality accessible to the user, However, if the same access control checks are NOT performed on the server, hackers will be able to penetrate into the application without proper authorization.
Let us understand Threat Agents, Attack Vectors, Security Weakness, Technical Impact and Business Impacts of this flaw with the help of simple diagram.
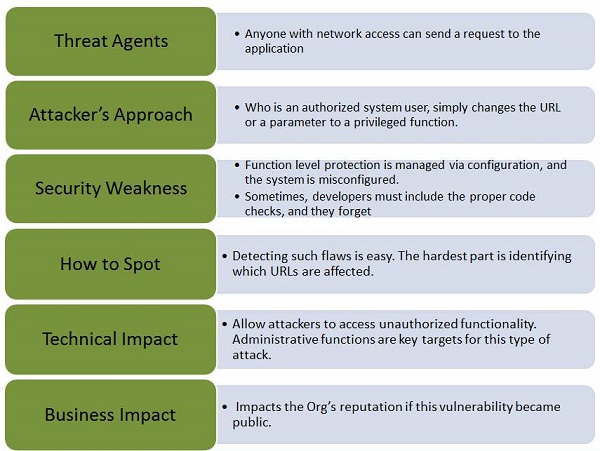
Example
Below is a classic example of Missing Function Level Access Control :
The hacker simply forces target URLs. Usually admin access requires authentication, however, if the application access is NOT verified an unauthenticated user can access admin page.
' Below URL might be accessible to an authenticated user http://website.com/app/standarduserpage ' A NON Admin user is able to access admin page without authorization. http://website.com/app/admin_page
Hands ON
1 .Let us login as account manager by first going through the list of users and their access previleges.
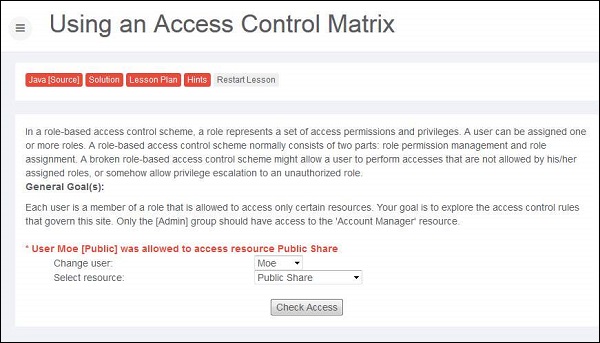
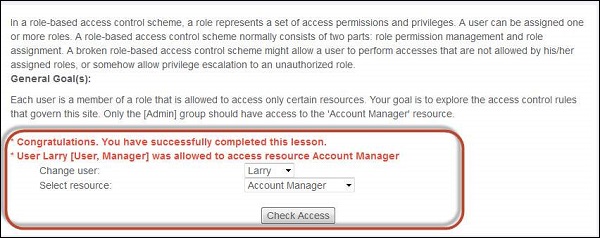
2 .Upon trying various combinations we can find it out that Larry has access to resource account manager.
Preventing Mechanisms
The authentication mechanism should deny all access by default, and provide access to specific roles for every function
In a workflow based application, verify the user state before allowing them to access any resources.
Dev can use the following resources as a guide to prevent this flaw during development process