
- Security Testing - Home
- Security Testing - Overview
- Security Testing - Process
- Security Testing - Malicious Software
- HTTP Protocol Basics
- HTTPS Protocol Basics
- Encoding and Decoding
- Security Testing - Cryptography
- Security Testing - Same Origin Policy
- Security Testing - Cookies
- Hacking Web Applications
- Security Testing - Injection
- Testing Broken Authentication
- Testing Cross Site Scripting
- Insecure Direct Object Reference
- Testing Security Misconfiguration
- Testing Sensitive Data Exposure
- Missing Function Level Access Control
- Cross Site Request Forgery
- Components with Vulnerabilities
- Unvalidated Redirects and Forwards
- Security Testing - Ajax Security
- Testing Security - Web Service
- Security Testing - Buffer Overflows
- Security Testing - Denial of Service
- Testing Malicious File Execution
- Security Testing - Automation Tools
Security Testing - Injection
Web Application - Injection
Injection technique consists of injecting a SQL query or a command using the input fields of the application. A successful SQL injection can read, modify sensitive data from the database and it can also to delete data from database. It also enables the hacker to perform administrative operations on the database such as shutdown the DBMS/dropping databases.
Let us understand Threat Agents, Attack Vectors, Security Weakness, Technical Impact and Business Impacts of this flaw with the help of simple diagram.
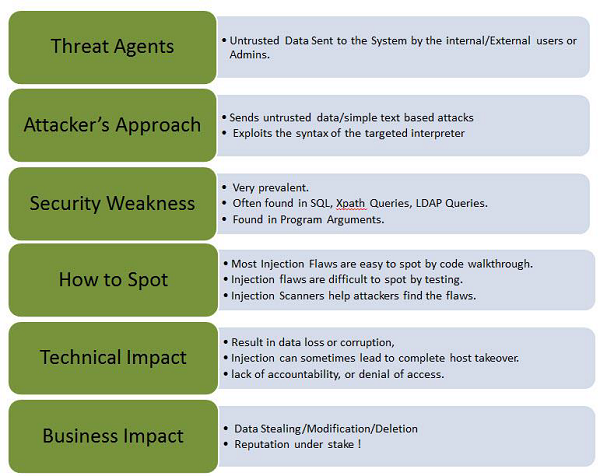
EXAMPLES
The application uses untrusted data in the construction of the following vulnerable SQL call
String query = "SELECT * FROM EMP WHERE EMPID='" + request.getParameter("id") + "'";
HANDS ON
1. Navigate to the SQL Injection area of the application as shown below.
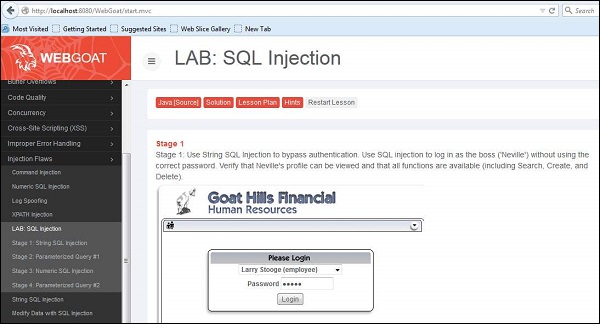
2. As given in the exercise, We will use String SQL Injection to bypass authentication. Use SQL injection to log in as the boss ('Neville') without using the correct password. Verify that Neville's profile can be viewed and that all functions are available (including Search, Create, and Delete).
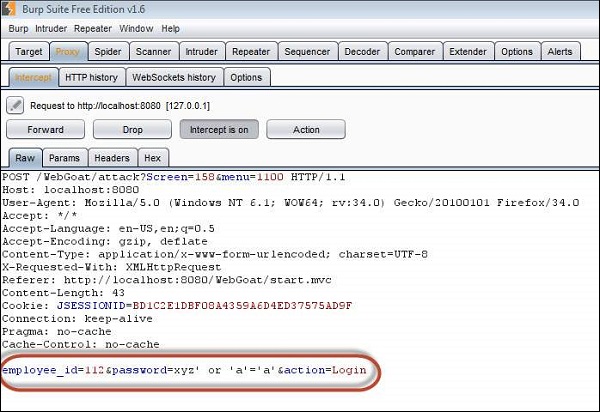
3. We will Inject a SQL such that we are able to bypass the password by sending the parameter as 'a'='a' or 1=1
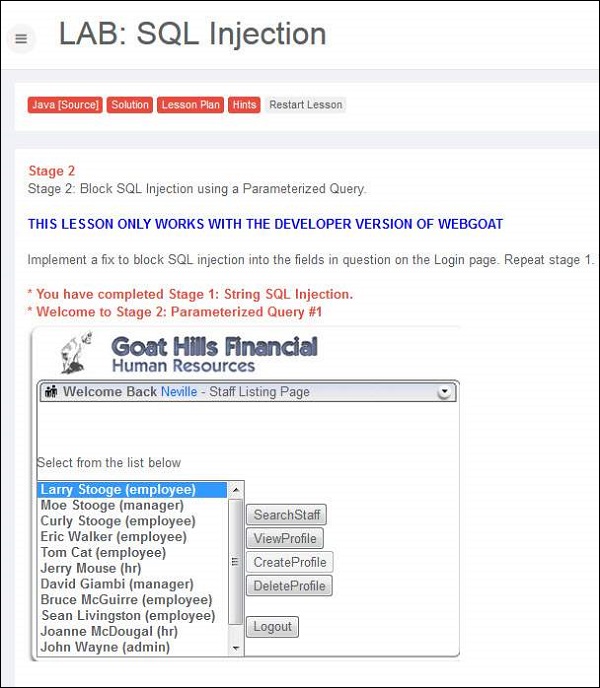
4. Post Exploitation we are able to login as Neville who is the Admin as shown below.
Preventing SQL Injection
There are plenty of ways to prevent SQL injection. When developers write the code they should ensure that they handle special characters accordingly. There are cheat sheets/prevention techniques available from OWASP which is definitely a guide for developers.