- Security Testing - Home
- Security Testing - Overview
- Security Testing - Process
- Security Testing - Malicious Software
- HTTP Protocol Basics
- HTTPS Protocol Basics
- Encoding and Decoding
- Security Testing - Cryptography
- Security Testing - Same Origin Policy
- Security Testing - Cookies
- Hacking Web Applications
- Security Testing - Injection
- Testing Broken Authentication
- Testing Cross Site Scripting
- Insecure Direct Object Reference
- Testing Security Misconfiguration
- Testing Sensitive Data Exposure
- Missing Function Level Access Control
- Cross Site Request Forgery
- Components with Vulnerabilities
- Unvalidated Redirects and Forwards
- Security Testing - Ajax Security
- Testing Security - Web Service
- Security Testing - Buffer Overflows
- Security Testing - Denial of Service
- Testing Malicious File Execution
- Security Testing - Automation Tools
Security Testing - Hacking Web Applications
Web Application - PenTesting Methodologies
There are various methodologies/approaches which we can make use as a reference for performing the attaks. Below are the following standards one can take into account while making developing their attack model.
Among the below list, OWASP is the most active and there are lot of contributors. We will focus on OWASP Techniques which each development team takes into consideration before designing a web app.
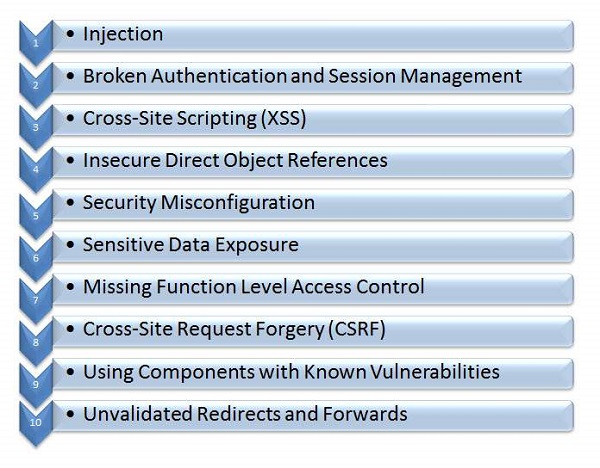
OWASP Top 10
The Open Web Application Security Protocol team released the top 10 vulnerabilities that are more prevelant in web in the recent years. Below are the list of security flaws that are more prevelant in a web based application. We will discuss all these techniques in detail in the upcoming chapters.
Application - Hands On
Inorder to understand each one of the techniques, let us work with a sample application. We will perform the attack on 'WebGoat', the J2EE application which has been developed explicitly with security flaws for learning purposes.
The complete details about the webgoat project can be located here
To Download the WebGoat Application, Navigate to https://github.com/WebGoat/WebGoat/wiki/Installation-(WebGoat-6.0) and goto downloads section.
To Install the downloaded Application, first ensure that you don't have any application running on Port 8080. It cab installed just using a single command - java -jar WebGoat-6.0.1-war-exec.jar. For more details, WebGoat Installation
Post Installation, we should be able to access the application by navigating to http://localhost:8080/WebGoat/attack and he page would be displayed as shown below.
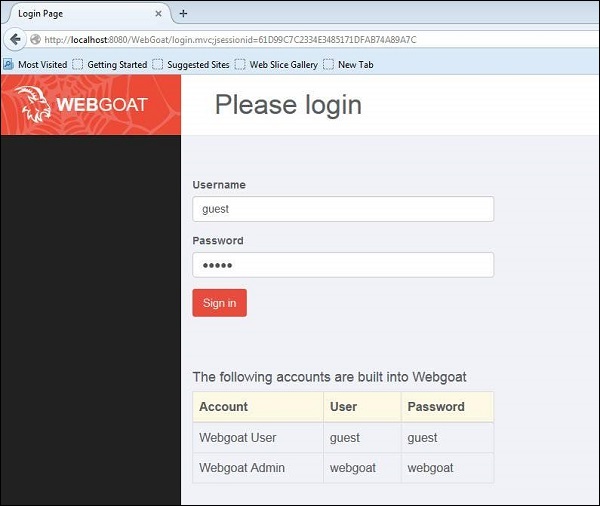
We can use the credentials of guest or admin as displayed in the login page.
Web Proxy
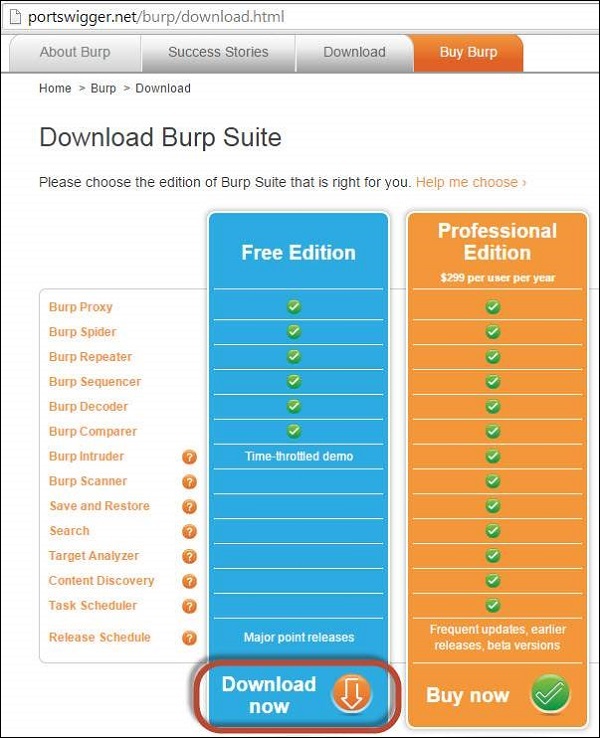
In order to intercept the traffic between client(Browser) and Server(System where Webgoat Application is hosted in our case), we will have to use a web proxy. We will use Burp Proxy and can be downloaded from http://portswigger.net/burp/download.html
It is sufficient to download the free version of burp suite as shown below.
CONFIGURING Burp Suite
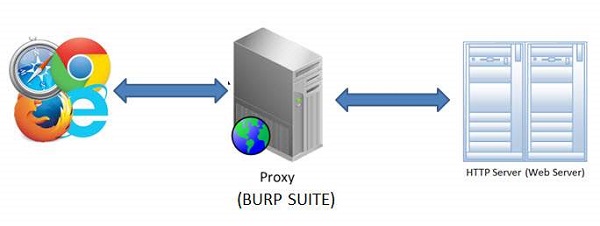
Burp Suite is a web proxy which can intercept each packet of information sent and received by the browser and webserver. This helps us to modify the contents before the client sends the information to the Web-Server.
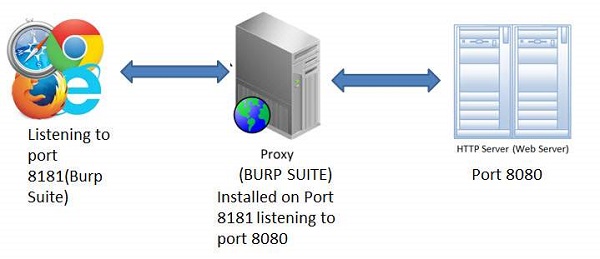
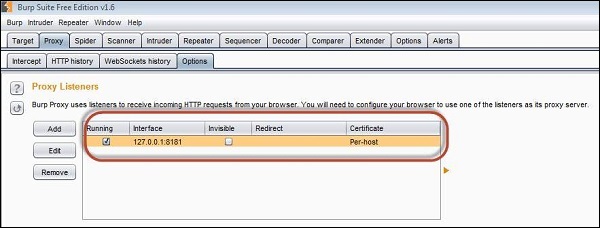
1. The App is installed on port 8080 and Burp is installed on port 8181 as shown below. Launch Burp suite and make the following settings inorder to bring it up in port 8181 as shown below.
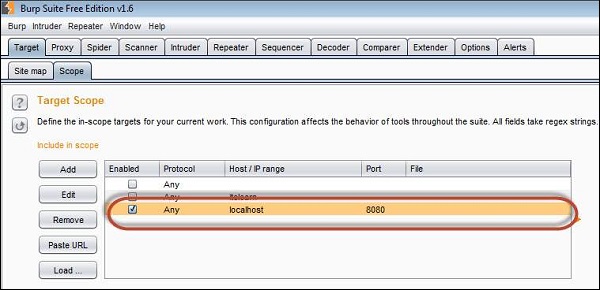
2. We Should ensure that the Burp is listening to Port#8080 where the application is installed so that Burp suite can intercept the traffic. This settings should be done on the scope tab of the Burp Suite as shown below.
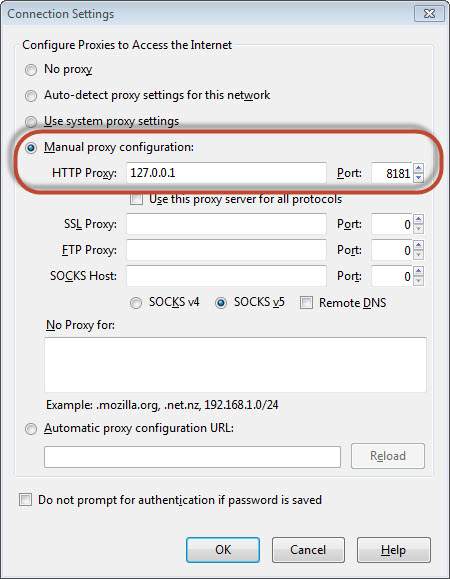
3. Then make your browser proxy settings to listen to the port 8181 (Burp Suite port). Thus we have configured the Web proxy to intercept the traffic between client(browser) and the server(Webserver) as shown below
4. The Snapshot of the configuration is shown below with a help of a simple workflow diagram as shown below