
 Data Structure
Data Structure Networking
Networking RDBMS
RDBMS Operating System
Operating System Java
Java MS Excel
MS Excel iOS
iOS HTML
HTML CSS
CSS Android
Android Python
Python C Programming
C Programming C++
C++ C#
C# MongoDB
MongoDB MySQL
MySQL Javascript
Javascript PHP
PHP
- Selected Reading
- UPSC IAS Exams Notes
- Developer's Best Practices
- Questions and Answers
- Effective Resume Writing
- HR Interview Questions
- Computer Glossary
- Who is Who
Secure Apache with Let\\\'s Encrypt Certificate on Rocky Linux
To secure Apache with a Let's Encrypt certificate on Rough Linux, directors can guarantee secure communication over HTTPS. By getting and introducing a Let's encrypt certificate, Apache can encrypt information transmission, upgrading security and ensuring delicate data. This preparation includes designing Apache to utilise the certificate, empowering HTTPS for the site, and guaranteeing that all communication between the server and clients is encrypted. Let's encrypt certificates that are trusted by major browsers, giving a cost-effective and broadly recognised arrangement for securing Apache web servers on Rough Linux.
Methods Used
Obtaining a let's encrypt certificate
Configuring Apache
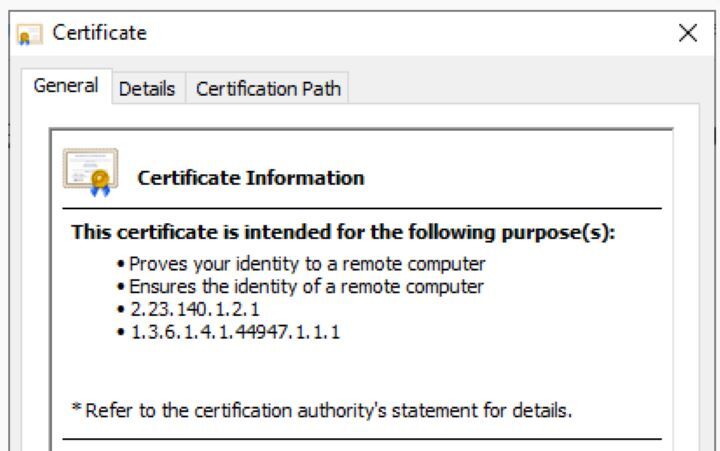
Obtaining a let's Encrypt Certificate
Getting a Let's encrypt certificate within the context of securing Apache with a Let's encrypt certificate on Rocky Linux includes the method of asking for and getting a substantial certificate from Let's encrypt. This regularly includes proving space proprietorship and creating a certificate that's trusted by Let's encrypt. The certificate acts as a computerised credential that confirms the genuineness of the server and empowers secure communication over HTTPS. By getting a Let's encrypt certificate, chairmen can guarantee that the net server on Rough Linux is prepared with a recognised and trusted certificate, improving security and ensuring delicate information is transmitted between the server and clients.
Algorithm
Start by introducing the Certbot instrument or an elective Summit client on the Rough Linux server.
Identify the space for which you need a Let's encrypt certificate.
Use the Certbot or Summit client command to ask for a certificate for the required space. This ordinarily includes demonstrating proprietorship of the space through a confirmation process, such as putting a particular record or DNS record on the server.
Once the confirmation is fruitful, the Summit client will produce a substantial Let's encrypt certificate for the domain.
Store the obtained certificate and the comparing private key in a secure area on the server.
Configure Apache's virtual host settings to utilise the gotten certificate and private key for secure communication.
Test the arrangement to guarantee that Apache can effectively utilise the Let's encrypt certificate and serve content over HTTPS.
Set up a component for programmed certificate reestablishment, as Let's encrypt certificates that have a constrained legitimacy period. This may be done by utilising Certbot's programmed reestablishment feature or by planning a cron job to run the certificate reestablishment command frequently.
Output
Configuring Apache
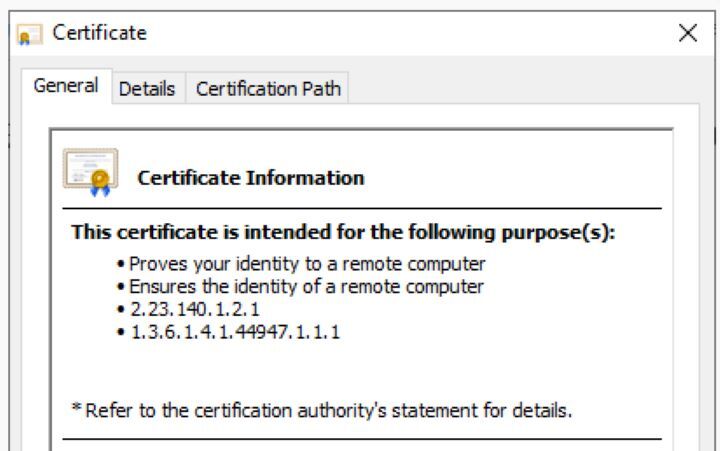
Designing Apache, within the context of securing Apache with a Let's encrypt certificate on Rough Linux, includes altering the Apache server setup to empower HTTPS and indicating the fitting settings for utilising the obtained certificate. This incorporates overhauling the Apache virtual have arrangement record to tune in on the HTTPS harbour, ordinarily 443, and arranging the SSL/TLS settings such as SSLCertificateFile and SSLCertificateKeyFile to point to the Let's encrypt certificate and private key records individually. Furthermore, any other fundamental SSL/TLS settings like SSLProtocol and SSLCipherSuite can be configured to guarantee a secure and compliant association. Appropriate setup of Apache is significant to guarantee that HTTPS is accurately empowered and the Let's encrypt certificate is utilised for setting up secure communication with clients.
Algorithm
Start by getting a Let's encrypt certificate for your space by employing an appropriate Summit client such as Certbot.
Once the certificate has been gotten, recognise the Apache setup record that compares to the virtual host that ought to be secured. This file is habitually found within the folders /etc/httpd/conf.d/ or /etc/apache2/sites-available/.
Using a substance editor, open the Apache setup record and locate the virtual have square for the space you would like to secure.
Within the virtual have square, include or alter the essential mandates to empower HTTPS. This incorporates indicating the SSL/TLS settings such as SSLCertificateFile and SSLCertificateKeyFile to point to the Let's encrypt certificate and private key records, respectively.
Additionally, design any other craved SSL/TLS settings, such as SSLProtocol and SSLCipherSuite, to improve security and compliance.
Save the changes to the Apache arrangement record and exit the content editor.
Test the Apache setup to guarantee there are no language structure blunders by running the suitable command, such as apachectl configtest or apache2ctl configtest.
If the arrangement test is fruitful, restart or reload the Apache server to apply the changes. Utilise commands like systemctl restart httpd or apache2 reload, depending on your Linux distribution.
Verify that Apache is presently serving the site over HTTPS by getting to the space in a web browser. Guarantee that the Let's encrypt certificate is substantial and trusted.
Output
Conclusion
This article gives a comprehensive guide on securing Apache with a Let's encrypt certificate on Rough Linux. It clarifies the significance of HTTPS communication and the benefits of utilising Let's encrypt certificates for encryption. The article covers two primary strategies, getting a Let's encrypt certificate and designing Apache, and gives calculations for each approach. It emphasises the noteworthiness of legitimate arrangements and highlights the dependability and cost-effectiveness of Let's encrypt certificates. Generally, the article points to engaging directors with the information and steps to upgrade the security of their Apache web servers on Rough Linux.

