- Mobile Security - Home
- Mobile Security - Introduction
- Mobile Security - Attack Vectors
- App Stores & Issues
- Mobile Security - Mobile Spam
- Mobile Security - Android OS
- Mobile Security - Android Rooting
- Mobile Security - Android Devices
- Mobile Security - Android Tools
- Mobile Security - Apple iOS
- iOS Device Tracking Tools
- Windows Phone OS
- Mobile Security - BlackBerry OS
- Mobile Security - BlackBerry Devices
- Mobile Security - MDM Solution
- SMS Phishing Countermeasures
- Mobile Security - Protection Tools
- Mobile Security - Pen Testing
Mobile Security - Android Rooting
Rooting is a word that comes from Linux syntax. It means the process which gives the users super privilege over the mobile phone. After passing and completing this process, the users can have control over SETTINGS, FEATURES, and PERFORMANCE of their phone and can even install software that is not supported by the device. In simple words, it means the users can easily alter or modify the software code on the device.
Rooting enables all the user-installed applications to run privileged commands such as −
Modifying or deleting system files, module, firmware and kernels
Removing carrier or manufacturer pre-installed applications
Low-level access to the hardware that are typically unavailable to the devices in their default configuration
The advantages of rooting are −
- Improved performance
- Wi-Fi and Bluetooth tethering
- Install applications on SD card
- Better user interface and keyboard
Rooting also comes with many security and other risks to your device such as −
- Bricking the device
- Malware infection
- Voids your phone's warranty
- Poor performance
Android Rooting Tools
As Android OS is an open source, the rooting tools that can be found over the internet are many. However, we will be listing just some of them −
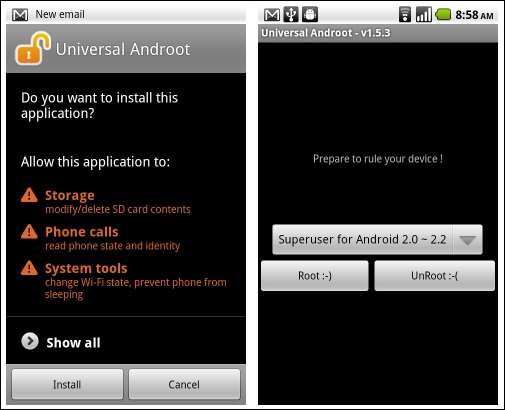
Universal Androot
You can download from https://androidapks.com/universal-androot/com-corner23-android-universalandroot/
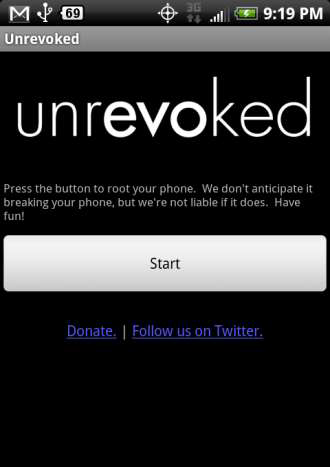
Unrevoked
Unrevoked available at https://unrevoked.com
Rooting Android Phones using SuperOneClick Rooting
SuperOneClick is one of the best tool designed especially for rooting an Android phone.
Let us see how to use it and root an android phone −
Step 1 − Plug in and connect your Android device to your computer with a USB cable.
Step 2 − Install the driver for the android device if prompted.
Step 3 − Unplug and re-connect, but this time select Charge only to ensure that your phone's SD card is not mounted to your PC.
Step 4 − Go to Settings → Applications → Development and enable USB Debugging to put your android into USB Debugging mode.
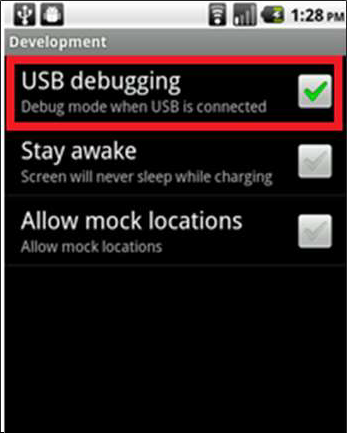
Step 5 − Run SuperOneClick.exe that you have downloaded from https://xdaforums.com/t/app-superoneclick-v2-3-3-motorola-exploit-added.803682/.
Step 6 − Click the Root button.
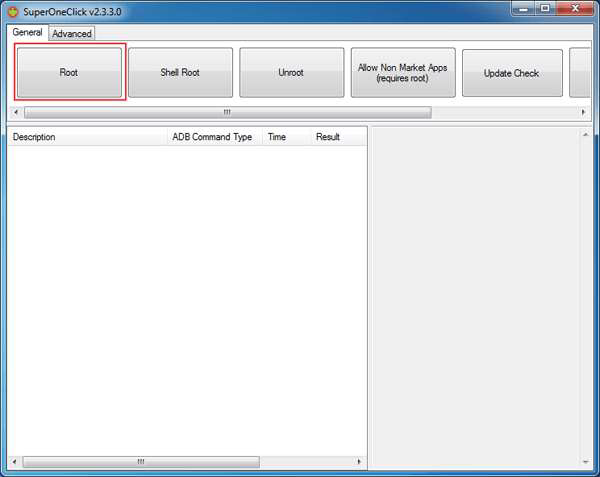
Step 7 − Wait for some time until you see a "Running a Su test Success!"
Step 8 − Check out the installed apps in your phone.
Step 9 − Superuser icon means you now have root access.
Rooting Android Phones Using Superboot
Superboot is a boot.img. It is designed specifically to root Android phones. It roots Android phones when they are booted for the very first time. Following are the steps
Step 1 − Download and extract the Superboot files
Step 2 − Put your Android phone in the bootloader mode −
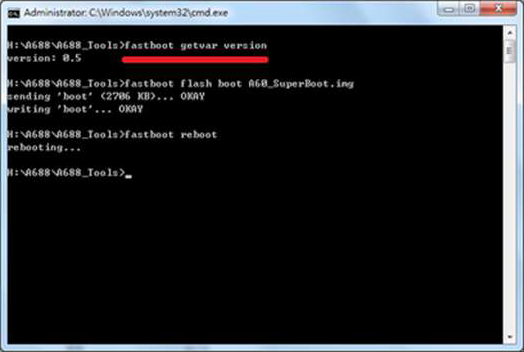
Step 3 − Turn off the phone, remove the battery, and plug in the USB cable.
Step 4 − When the battery icon appears on the screen, pop the battery back in.
Step 5 − Now tap the Power button while holding down the Camera key. For Android phones with a trackball: Turn off the phone, press and hold the trackball, then turn the phone back on.
Step 6 − Depending on your computer's OS, do one of the following.
Windows − Double-click install-superboot-windows.bat.
Mac − Open a terminal window to the directory containing the files, and type chmod +x. Install-superboot-mac.sh" followed by ./install-superboot-mac.sh.
Linux − Open a terminal window to the directory containing the files, and type chmod +x. Install-superboot-linux.sh" followed by ./install-superboot-linux.sh.
Step 7 − Your Android device has been rooted.
Android Trojan
ZitMo (ZeuS-in-the-Mobile)
Zitmo refers to a version of the Zeus malware that specifically targets mobile devices. It is a malware Trojan horse designed mainly to steal online banking details from users. It circumvents mobile banking app security by simply forwarding the infected mobile's SMS messages to a command and control mobile owned by cybercriminals. The new versions of Android and BlackBerry have now added botnet-like features, such as enabling cybercriminals to control the Trojan via SMS commands.
FakeToken and TRAMP.A
FakeToken steals both authentication factors (Internet password and mTAN) directly from the mobile device.
Distribution Techniques − Through phishing emails pretending to be sent by the targeted bank. Injecting web pages from infected computers, simulating a fake security app that presumably avoids the interception of SMS messages by generating a unique digital certificate based on the phone number of the device. Injecting a phishing web page that redirects users to a website pretending to be a security vendor that offers the "eBanking SMS Guard" as protection against "SMS message interception and mobile Phone SIM card cloning".
Fakedefender and Obad
Backdoor.AndroidOS.Obad.a is an Android Trojan known for its ability to perform several different functions such as, but not limited to, remotely performing commands in the console, sending SMS messages to premium-rate numbers, downloading other malware and even installing malware on an infected device just to send it to someone else through Bluetooth communication. The Backdoor.AndroidOS.Obad.a Android Trojan is a treacherous threat that disturbingly runs in the background lacking a common interface or front-end access.
FakeInst and OpFake
Android/Fakeinst.HB is a repackaged clone of a popular, free racing game. Unlike the original, the repackaged clone requires the user to pay a charge, supposedly to "access higher game levels".
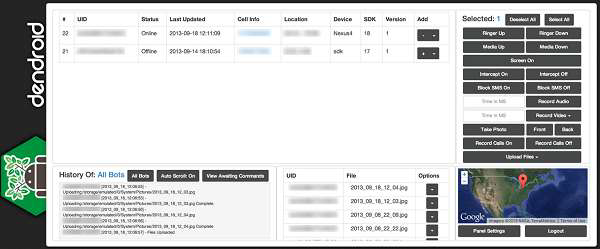
AndroRAT and Dendoroid
It is a free Android remote administration tool (RAT) known as AndroRAT (Android.Dandro) and what was believed to be the first ever malware APK binder. Since then, we have seen imitations and evolutions of such threats in the threat landscape. One such threat that is making waves in underground forums is called Dendroid (Android.Dendoroid), which is also a word meaning - something is tree-like or has a branching structure.