
- Mobile Security - Home
- Mobile Security - Introduction
- Mobile Security - Attack Vectors
- App Stores & Issues
- Mobile Security - Mobile Spam
- Mobile Security - Android OS
- Mobile Security - Android Rooting
- Mobile Security - Android Devices
- Mobile Security - Android Tools
- Mobile Security - Apple iOS
- iOS Device Tracking Tools
- Windows Phone OS
- Mobile Security - BlackBerry OS
- Mobile Security - BlackBerry Devices
- Mobile Security - MDM Solution
- SMS Phishing Countermeasures
- Mobile Security - Protection Tools
- Mobile Security - Pen Testing
Mobile Security - MDM Solution
Mobile Device Management (MDM) software is a vital component that monitors, safeguards, manages, and supports different types of mobile devices and tablets including iPhone, iPad, Android, and BlackBerry, along with the applications that run on them. It monitors all mobile devices with different operating system such as Android, Windows, and Symbian mobile.
MDM provides platforms for over-the-air or wired distribution of applications, data, and configuration settings for all types of mobile devices along with mobile phones, smartphones, tablet computers, etc.
With the help of MDM, enterprise-wide policies can be implemented easily to reduce support costs, time, and business and security threats. All the company-owned, consumerowned, as well as the employee-owned devices across the enterprise can be easily managed with the help of it.
MDM can reduce support cost and minimize business threats just by safeguarding and controlling all the data and configuration settings of all the mobile devices in the network.
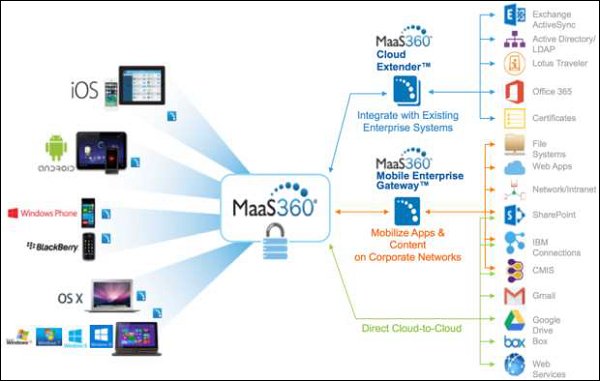
MaaS360 Mobile Device Management Solutions
MaaS360 Mobile Device Management solution is an IBM solution and is a software that allows you to monitor and govern mobile devices arriving into the organization, whether they are provided by the company or part of a Bring Your Own Device (BYOD) program. It can be downloaded at https://www-03.ibm.com/security/mobile/maas360.html
This technique allows organizations to implement the MDM life cycle for devices such as smartphones and tablets including iPhones, iPads, Androids, Windows Phones, BlackBerrys, and Kindle Fires. Using the integrated cloud platform, the MaaS360 streamlines MDM with improved visibility and control that spans across mobile devices, applications, and documents.
Bring Your Own Device (BYOD)
BYOD also called Bring Your Own Technology (BYOT), Bring Your Own Phone (BYOP), and Bring Your Own Personal Computer (BYOPC) refers to the policy of permitting employees to bring personally owned mobile devices (laptops, tablets, and smart phones) to their workplace, and to use those devices to access privileged company information and applications.
There are four basic options, which allow −
- Unlimited access for personal devices.
- Access only to non-sensitive systems and data.
- Access, but with IT control over personal devices, apps, and stored data.
- Access, while preventing local storage of data on personal devices.
BYOD Risks
Implementing BYOD in the company has its own risks and are as follows −
- Increases the possibility of data leak in the company.
- Increases the possibility of exploits in the company as there are more mobile devices in the network.
- Chances of mixing personal data with job data.
- Increase in possibility to access unauthorized data.
BYOD Policy Implementation
Following are the security guidelines for both administrators and employees.
BYOD Security Guidelines for Administrator
The administrator should follow the guidelines listed here to implement mobile device security −
Publish an enterprise policy that specifies the acceptable usage of consumer grade devices and bring-your-own devices in the enterprise.
Publish an enterprise policy for cloud.
Enable security measures such as antivirus to protect the data in the datacenter.
Implement policy that specifies which levels of application and data access are allowed on consumer-grade devices, and which are prohibited.
Specify a session timeout through Access Gateway.
Specify whether the domain password can be cached on the device, or whether users must enter it every time they request access.
Determine the allowed Access Gateway authentication methods from the following −
No authentication
Domain only
RSA SecurlD only
Domain + RSA SecurlD
SMS authentication
BYOD Security Guidelines for Employees
Disable the collection of Diagnostics and Usage Data under Settings/General/About.
Apply software updates when new releases are available.
Logging and limited data on device.
Device encryption and application patching.
Managed operating environment.
Managed application environment.
Press the power button to lock the device whenever it is not in use.
Verify the location of printers before printing sensitive documents.
Utilize a passcode lock to protect the access to the mobile device; consider the eight-character non-simple passcode.
Report a lost or stolen device to IT so they can disable certificates and other access methods associated with the device.