
 Data Structure
Data Structure Networking
Networking RDBMS
RDBMS Operating System
Operating System Java
Java MS Excel
MS Excel iOS
iOS HTML
HTML CSS
CSS Android
Android Python
Python C Programming
C Programming C++
C++ C#
C# MongoDB
MongoDB MySQL
MySQL Javascript
Javascript PHP
PHP
- Selected Reading
- UPSC IAS Exams Notes
- Developer's Best Practices
- Questions and Answers
- Effective Resume Writing
- HR Interview Questions
- Computer Glossary
- Who is Who
How secure is your cloud
Cloud computing is one of the hottest areas in IT sectors which has been a game changer. Cloud has moved the on-premise environment to internet environment and created a single platform of access. Since, the environment has moved to the network of network, one should be very careful with respect to security issues. During the initial phase, cloud suffered a lot with the security issues. Continuous research in the area of cloud security has created huge impact and built trust among the cloud users.

Various security features made the non-cloud users to move towards cloud. In this article, I am going to share few important security aspects of cloud which needs to be known before migrating towards it. This will help the non-cloud users to keep checkpoints before moving towards. Awareness on these features will make someone to know, how far cloud is secured than On-premise environment.
One Entry – One Exit
In cloud, On-premise environment has been moved to network of networks where one cannot predict the number of networks hosted in the cloud. There can be “N” number of networks forming a single cloud. While hosting the services in the on-premise environment, one has to provide the login credentials for each and every entry. The session should be closed (logged out) while coming outside the network. This is one of the tedious processes and if the session is not closed proper, the chance of vulnerability is too high. In cloud, this has been overcome by a single sign-on method. All you need to sign on once to access the entire cloud environment and sign out once to come out of the cloud environment. That single entry will have plenty of check points, which has been discussed below. Basically this method will automatically close all the sessions and avoid unnecessary issue.
Enter, before you Enter
Since most of the cloud environment follows single sign-on method, it is essential to have proper checks during the entry. One time password and Code generators are the two methods that will ensure the security in the entry point of the cloud. In both the methods random numbers will generated and checked the numbers in the data. The major difference between code generator and OTP is, code generator will generate random numbers continuously intervals. User need not request for new code. In most of the cloud, code generator is being used at the entry points.
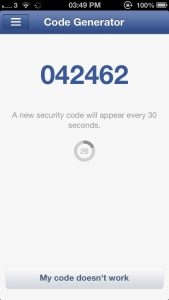
Most of us don’t know that, Code generator feature has been used in the Facebook. Try using this option from the tab ‘Help & Settings’. New security code will appear every 30 seconds which can be used for login.
Stop, Scan, Send
Irrespective of the credentials all the incoming request will be scanned and compared with the previous request history. Scanning double ensures the security for the data that is being stored in the cloud. Basically these software will read the request headers and compares with previous history of access. If any request from the external environment is found to be abnormal or malicious, scanning software will notify the cloud service provider about the request. This will help the cloud service providers to easily identify the illegal request and also identity the robots. Human request and robot request are differentiated using various criteria such as image identification and request speed. Scanning ensures that the cloud service is accessed by the authorized users from an authorized environment.
Intrusion Detection System
Intrusion Detection system is one of the popular scanning method used in the networks which can also be used in the cloud environment. IDS can be either hardware or Software. In general, these IDS will scan the incoming request and alert the user and network admin about the abnormal request. IDS generally detects the abnormal request either based upon the predefined rules or based upon the nature of the request.

Snort is one of the popular and open source Intrusion Detection System which is widely been used in the market. Basically, IDS concept was introduced for networks; still we don’t have standard IDS for the cloud. Research on this topic is still in progress.
Hybrid Cloud
Hybrid Cloud is one of the most popular models of cloud service which combines the various other cloud models and deliver the service to the user. In most of the Hybrid cloud model, private cloud model will be the major contributor. In hybrid cloud, all the sensitive and important information will be stored in the private cloud and rest are hosted in the other cloud service model. This will ensure that sensitive information is protected from the unwanted traffic from the external environment.
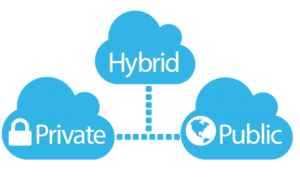
In hybrid cloud, private cloud will reside in the user environment and other cloud models will reside in the service provider end. This will create trust among the end user on the cloud services and will be a fuel for migrating towards the cloud. Building hybrid cloud is considered as the best practice which will also ensure that the service cost is low.
Know your Certificates
Beyond all these security aspects of the cloud, the end user should be aware about the available security features in the cloud. One should be aware about the security certificates received by the service provider. User should be aware about the clients of the service provider and analyze the security features of the cloud from the other clients. This will help the user to know more about the service provider. One should cross check browser certification with the information provided in the certificate issuing authority.

In the digital world, the ultimate responsibility of the security lies with the end user who is using the service than the service provider. ‘You are responsible for your data’ is the thumb rule.
Points to Ponder
- Try to know about the architecture of the cloud service provider
- Know about the security features of the cloud
- Know about the clients.
- Try to use secured device to access the cloud
- Do not share your cloud credentials to anyone. Code generator is preferable.

