Article Categories
- All Categories
-
 Data Structure
Data Structure
-
 Networking
Networking
-
 RDBMS
RDBMS
-
 Operating System
Operating System
-
 Java
Java
-
 MS Excel
MS Excel
-
 iOS
iOS
-
 HTML
HTML
-
 CSS
CSS
-
 Android
Android
-
 Python
Python
-
 C Programming
C Programming
-
 C++
C++
-
 C#
C#
-
 MongoDB
MongoDB
-
 MySQL
MySQL
-
 Javascript
Javascript
-
 PHP
PHP
Explain the TCP Connection Management
The connection is established in TCP using the three-way handshake as discussed earlier to create a connection. One side, say the server, passively stays for an incoming link by implementing the LISTEN and ACCEPT primitives, either determining a particular other side or nobody in particular.
The other side performs a connect primitive specifying the I/O port to which it wants to join. The maximum TCP segment size available, other options are optionally like some private data (example password).
The CONNECT primitive transmits a TCP segment with the SYN bit on and the ACK bit off and waits for a response.
The sequence of TCP segments sent in the typical case, as shown in the figure below −
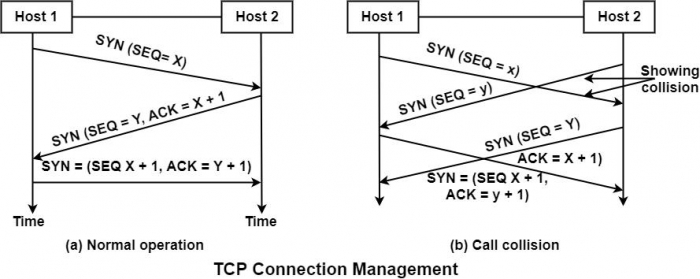
When the segment sent by Host-1 reaches the destination, i.e., host -2, the receiving server checks to see if there is a process that has done a LISTEN on the port given in the destination port field. If not, it sends a response with the RST bit on to refuse the connection. Otherwise, it governs the TCP segment to the listing process, which can accept or decline (for example, if it does not look similar to the client) the connection.
Call Collision
If two hosts try to establish a connection simultaneously between the same two sockets, then the events sequence is demonstrated in the figure under such circumstances. Only one connection is established. It cannot select both the links because their endpoints identify connections.
Suppose the first set up results in a connection identified by (x, y) and the second connection are also released up. In that case, only tail enter will be made, i.e., for (x, y) for the initial sequence number, a clock-based scheme is used, with a clock pulse coming after every 4 microseconds. For ensuring additional safety when a host crashes, it may not reboot for sec, which is the maximum packet lifetime. This is to make sure that no packets from previous connections are roaming around.


