
 Data Structure
Data Structure Networking
Networking RDBMS
RDBMS Operating System
Operating System Java
Java MS Excel
MS Excel iOS
iOS HTML
HTML CSS
CSS Android
Android Python
Python C Programming
C Programming C++
C++ C#
C# MongoDB
MongoDB MySQL
MySQL Javascript
Javascript PHP
PHP
- Selected Reading
- UPSC IAS Exams Notes
- Developer's Best Practices
- Questions and Answers
- Effective Resume Writing
- HR Interview Questions
- Computer Glossary
- Who is Who
Database Security
A crucial component of contemporary business and technology is database security. The danger of a data breach or cyber assault rises as organizations continue to gather, manage, and store enormous volumes of data. A data breach may result in monetary losses, harm to one's reputation, and legal repercussions. Therefore, it's crucial to establish strong database security measures to protect sensitive data and uphold the database's integrity and confidentiality. This post will address some best practices to make sure your database is safe as well as the many facets of database security.
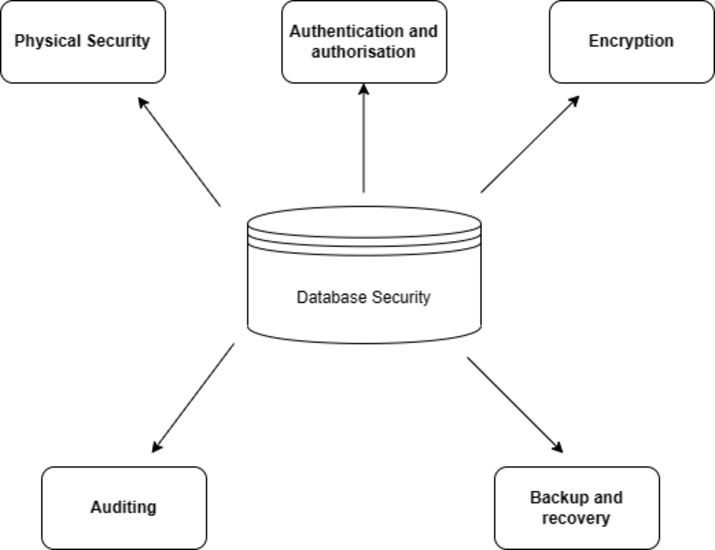
Database security types
Physical Security ? The safeguarding of the actual infrastructure that contains the database is referred to as physical security. This covers the server room's physical security as well as the security of the network and storage systems. Only authorized workers should be able to enter the server room, and CCTV cameras should be placed to keep an eye on the space. Utilizing firewalls, intrusion detection systems, and other security measures, the network infrastructure should be protected. Encryption should be used on storage devices to prevent theft and unauthorized access.
Authentication and authorization ? Two crucial elements of database security are authentication and authorization. Authorization is the process of giving access to certain resources depending on the user's role and rights, whereas authentication is the process of confirming a user's identity. Strong passwords and regular password changes should be mandated by password regulations. To add another level of protection, two-factor authentication ought to be implemented. To guarantee that users can only access data that they are authorized to access, authorization regulations should be strictly adhered to.
Encryption ? Data encryption is the process of encoding data so that it can only be read with a special key. Both data in transit (being transferred over a network) and data at rest (being kept on a disc) can be protected via encryption. Data at rest can be encrypted using disc encryption, while data in transit can be encrypted using SSL/TLS. Sensitive data in a database can also be encrypted using column-level encryption.
Auditing ? Monitoring and logging database activities is referred to as auditing. Unauthorized access, data breaches, and other security problems may all be found and avoided with the use of auditing. Auditing should be set up to record pertinent data, including user activity, failed login attempts, and alterations to the database structure. The logs should be kept in a secure location and routinely checked for any unusual activities.
Backup and recovery ? Essential elements of database security, backup and recovery. To guarantee that data can be restored in the case of a disaster or cyberattack, regular backups should be made. Backups have to be encrypted and kept in a safe place. Regular testing of recovery processes is necessary to guarantee efficient and speedy data recovery.
Best Database Security Practises
Implement a strong password policy ? Password policies should demand robust, challenging passwords. Regular password changes and the usage of two-factor authentication should be utilized to offer an extra layer of protection.
Implement access controls ? Access controls should be implemented to guarantee that users can only access data to which they have been granted access. Role-based access restrictions, which give access depending on a user's role and permissions, can be used to do this.
Regularly patch and update software ? Regular software patching and upgrading can assist stop the exploitation of security flaws. The operating system, database management system, and other software should all be kept up to date.
Encrypt sensitive data ? Sensitive information should be encrypted both in transit and at rest. This can aid in preventing security lapses and unauthorized access.
Implement audits and monitoring ? These procedures can aid in the detection and avoidance of security incidents. Regular log reviews are crucial, as is looking into any shady activities.
Conclusion
A crucial component of contemporary business and technology is database security. To safeguard sensitive data from cyberattacks and data breaches, organizations must deploy strong database security measures as they continue to acquire and store enormous volumes of data. Physical security, authentication and authorization, encryption, auditing, and backup and recovery are some of these safeguards.
Organizations can make sure that their database is safe and that their data is secured by adhering to best practices including creating strong password rules, enforcing access limits, routinely patching and upgrading software, encrypting sensitive data, and implementing audits and monitoring. To keep up with changing threats and stay ahead of possible security issues, it is crucial to routinely examine and update security procedures. Organizations may protect their data and uphold the confidence of their stakeholders and consumers by putting a high priority on database security.

