Data Structure
Data Structure Networking
Networking RDBMS
RDBMS Operating System
Operating System Java
Java MS Excel
MS Excel iOS
iOS HTML
HTML CSS
CSS Android
Android Python
Python C Programming
C Programming C++
C++ C#
C# MongoDB
MongoDB MySQL
MySQL Javascript
Javascript PHP
PHP
- Selected Reading
- UPSC IAS Exams Notes
- Developer's Best Practices
- Questions and Answers
- Effective Resume Writing
- HR Interview Questions
- Computer Glossary
- Who is Who
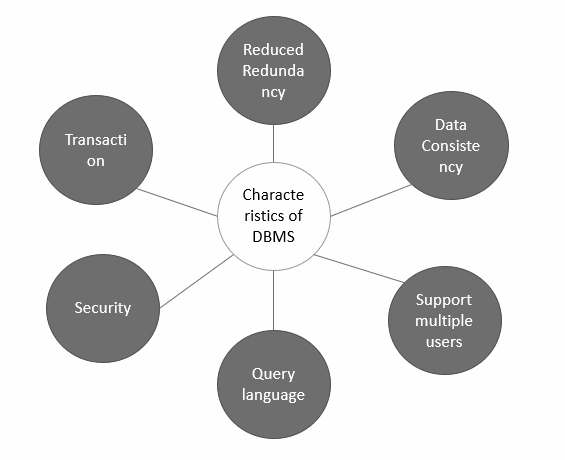
Explain the characteristics of DBMS?
There are so many characteristics of a database management system, which are as follows −
-
A database management system is able to store any kind of data in a database.
-
The database management system has to support ACID (atomicity, consistency, isolation, durability) properties.
-
The Database management system allows so many users to access databases at the same time.
-
Backup and recovery are the two main methods which allow users to protect the data from damage or loss.
-
It also provides multiple views for different users in a single organization.
-
It follows the concept of normalization which is helpful to minimize the redundancy of a relation.
-
It also provides users query language, helpful to insert, retrieve, update, and delete the data in a database.
Examples of DBMS
There so many examples of DBMS, which are as follows −
-
MySQL Database − It was founded in 1995. MySQL was acquired by Sun Microsystems in 2008 and Sun Microsystems was acquired by Oracle after two years. It is one of the largest open-source companies and is popular due to its high level of efficiency, reliability and cost.
-
MS-Access − It was developed by Microsoft and this computer-based application is used to form as well as create the databases on the desktop of the computers. It can be used for personal work and for small scale businesses that require a database. It is easy as it uses the graphical user interface.
-
Oracle database − It is the fourth relational database management system which is developed by Oracle Corporation. It is useful for storing a large amount of data. Moreover, it is flexible and very beneficial for shared SQL and locking.
-
DB2 − It was founded by IBM Corporation to store data for big industries. It is also called a relational database management system and extended version of DB2 that supports object-oriented features.
-
Microsoft SQL Server − As the name indicates, it is an RDBMS from Microsoft Company which creates computer databases for MS Windows. Based on customer’s requirements, Microsoft has developed various versions of SQL Server.
The characteristics of DBMS are explained below in pictorial form −