
 Data Structure
Data Structure Networking
Networking RDBMS
RDBMS Operating System
Operating System Java
Java MS Excel
MS Excel iOS
iOS HTML
HTML CSS
CSS Android
Android Python
Python C Programming
C Programming C++
C++ C#
C# MongoDB
MongoDB MySQL
MySQL Javascript
Javascript PHP
PHP
- Selected Reading
- UPSC IAS Exams Notes
- Developer's Best Practices
- Questions and Answers
- Effective Resume Writing
- HR Interview Questions
- Computer Glossary
- Who is Who
WiFi Protected Access (WPA) and WiFi Protected Access 2 (WPA2)
Wi-Fi Protected Access (WPA) and Wi-Fi Protected Access 2 (WPA2) are security standards to protect network stations connected to WiFi networks. They were developed by WiFi Alliance for delivering sophisticated data encryption technologies and improved user authentication than the pre-existing Wired Equivalent Privacy (WEP).
WiFi Protected Access (WPA)
Wi-Fi Protected Access (WPA) was supported in IEEE 802.11i wireless networks and was proposed in 2004. It was backward-compatible with the existing WEP that led to its rapid, hassle-free adoption.
The encryption method adopted in WPA is the Temporal Key Integrity Protocol (TKIP). TKIP includes per-packet key, integrity check, re-keying mechanism. It dynamically generates an encryption for each packet thus providing better security.
WiFi Protected Access 2 (WPA2)
Wi-Fi Protected Access II (WPA2) aims for complete compatibility with IEEE802.11i standard that was partially achieved by WPA. It provides stronger data protection and more control over network access. WPA2 is a NIST (National Institute of Standards and Technology) compliant encryption algorithm and provides 802.1x-based authentication.
WPA2 replaces TKIP in WPA with Counter mode Cipher block chaining Message authentication Code Protocol (CCMP). However, WPA2 is not compatible with older systems, and so it has emerged as a concurrent security standard along with WPA.
Modes of WPA and WPA2
WPA and WPA2 operate in two separate modes catering to enterprise and personal users.
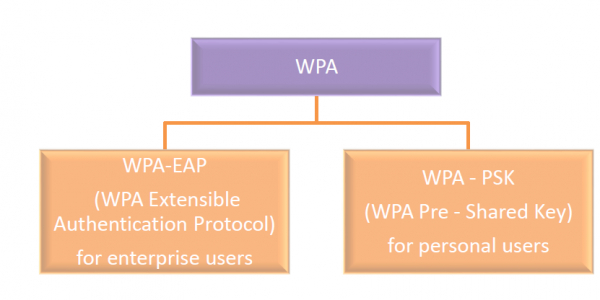
WPA-EAP (WPA Extensible Authentication Protocol) − It was developed for enterprise or business networks and requires a Remote Authentication Dial-In User Service (RADIUS) authentication server. It requires a complicated setup and provides automatic key generation and additional security measures. It uses various Extensible Authentication Protocol (EAP) for authenticating various categories of network users.
WPA-PSK (WPA Pre - Shared Key) − It was developed for use in home and small offices and does not need any authentication server. There is a 256-bit shared key in the wireless network, from which each connected device derives its 128-bit encryption key.

