
 Data Structure
Data Structure Networking
Networking RDBMS
RDBMS Operating System
Operating System Java
Java MS Excel
MS Excel iOS
iOS HTML
HTML CSS
CSS Android
Android Python
Python C Programming
C Programming C++
C++ C#
C# MongoDB
MongoDB MySQL
MySQL Javascript
Javascript PHP
PHP
- Selected Reading
- UPSC IAS Exams Notes
- Developer's Best Practices
- Questions and Answers
- Effective Resume Writing
- HR Interview Questions
- Computer Glossary
- Who is Who
What is DevSecOps and Why it is Important?
DevSecOps is a new word that has emerged in the software industry as a result of rising cybercrime and cybersecurity risks in recent years. It is essential for developers and businesses to implement DevSecOps in order to stay up with the demands of contemporary application and software development.
1. What is DevSecOps?
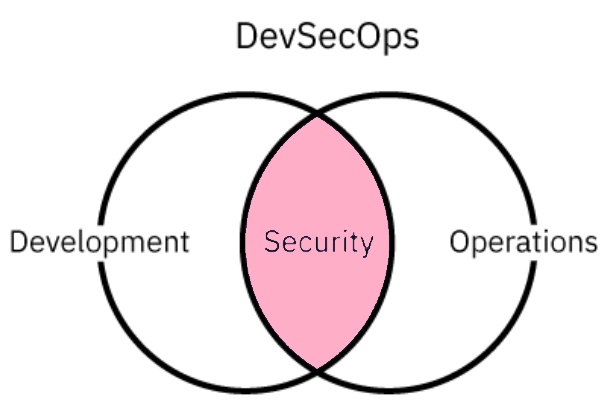
Development, security, and operations all make up the acronym "devSecOps." It is the inclusion of security right away in the process of developing software or an application.
Security was previously added to an application late in the lifecycle, following the development phase. The traditional development approach was hampered by the development of cloud platforms, microservices, and containers. As developers adopted agile and DevOps practices for modern application development and deployment, security was unable to keep up with the rapid releases.
By addressing issues as they arise within the Continuous Integration (CI) and Continuous Delivery (CD) pipelines, DevSecOps integrates security with DevOps.
2. DevOps vs. DevSecOps?
The primary difference between the two is that DevSecOps aims to integrate security into the DevOps lifecycle, whereas in the past DevOps had been distinct from security in the information technology lifecycle. This approach worked well when web and software development cycles were longer, but not with today's technology's increasing speed and condensed cycles.
With these modifications, our security strategy must adjust to keep up with DevOps's accelerating pace, agility, and scalability. Introducing DevSecOps. By incorporating security into the DevOps process, we can maintain its current at every stage of the lifecycle. This procedure results in a "Clean as you go" method of implementing security.
3. DevSecOps Best Practices
Following are the best practices of DevSecOps
-
Incorporate a ''Shift Left'' mentality.
The DevSecOps technique has made frequent use of this phrase. Consider the DevSecOps lifecycle as either a straight line or even a circle that rotates in a clockwise direction. In a similar line, the expression "Shift Left" encourages us to relocate security farther from the lifecycle's conclusion. In this manner, security is implemented at the outset of the project and is maintained throughout.
-
Add team?wide security education
A smaller knowledge gap and more uniform security procedures will result from educating all team members on the fundamentals of security and compliance.
-
Improve communication and transparency
Delays and unfinished projects are reduced when teams and individuals communicate effectively and openly. Additionally, transparency fosters a more fluid cross-role efficiency through comprehension. Efficiency and productivity significantly increase when team members are aware of how their duties relate to those of others.
-
Support team?driven workflow
Encourage your teams to create as much of their preferred workflow and tools as is feasible. By giving them that flexibility, they can work at their peak efficiency.
-
Utilize reporting and analytics
This becomes a DevSecOps lifecycle powerhouse when used in combination with automation and the other technologies
4. Implementation of DevSecOps?
Depending on the scale and complexity of your project, the procedures necessary in implementing DevSecOps may vary slightly, but these are the primary stages you'll go through.
-
Planning
It is important to keep in mind that early development should incorporate security objectives. A clear plan must be created, with an emphasis on threat-defense models, acceptance test criteria, application interface, and performance and security.
-
Developing
Security teams must be prepared to modify their procedures to fit the development workflow, and the development team should assess current security procedures and recommend essential adjustments. In remote product development, this is very important.
-
Building and testing
Automated build tools support the DevSecOps implementation process by enabling test-driven development and using statistical code analysis to make sure the software design complies with coding and security standards.
-
Deploying
Infrastructure-as-code (IaC) technologies are often used for provisioning and deployment, automating the process for consistency while accelerating software delivery. These technologies boost productivity while also assisting in lowering issues brought on by human mistakes.
-
Operating and monitoring
The operations team must do routine updates and monitoring, paying close attention to find zero-day vulnerabilities (software flaws that are publicly disclosed but may be discovered by attackers before the necessary patches are released). DevSecOps' ongoing security helps to avert such problems.
-
Scaling
Large data centers are no longer necessary for enterprises to maintain because of cloud computing and virtualization technologies. They may simply replace it in the case of a specific danger or grow their IT infrastructure as needed. Security of corporate communications is particularly relevant to this.
-
Adapting
DevSecOps requires ongoing improvement, just like any other business process, to make sure it is operating as it should. This entails assessing procedures and adapting to accommodate shifting trends and boost development.
5. The Advantages of DevSecOps?
An improved return on investment (ROI) for the organization's current security system
Due to automation, there are fewer opportunities for error or administrative failure situations, two factors that could normally lead to cyberattacks and downtime.
Automation eliminates the need for cybersecurity architects to set up security consoles, allowing security teams to focus on other urgent challenges while increasing their agility and speed.
Improved team collaboration and communication
More adaptability in handling unforeseen changes throughout the development lifecycle
greater potential for automated builds and quality assurance tests
6. DevSecOps Skills and Tools?
For teams concerned with security, the DevSecOps community has a variety of practical tools. Numerous security-related jobs are covered by the following tools:
Claire ? Examines Docker containers for flaws
HackerOne ? Allows you to prioritize and respond to vulnerability reports in an effective and timely manner.
Rapid7 Nexpose ? Manages the complete lifecycle of vulnerability detection and scans systems for flaws.
Snyk ? Looks for any known problems with open-source libraries.
Stethoscope ? Aids in user-focused security management; open-source
Suricata ? Open-source software that detects threats to networks
Conclusion
In conclusion, integrating DevSecOps, or building security into software and data from the outset of its development, is the greatest approach for businesses to benefit from the DevOps philosophy. Building on the idea that "everyone is accountable for security" is the goal and intent of DevSecOps.

