
- SAP HANA - Overview
- In-Memory Computing Engine
- SAP HANA - Studio
- Studio Administration View
- SAP HANA - System Monitor
- SAP HANA - Information Modeler
- SAP HANA - Core Architecture
- SAP HANA Modeling
- SAP HANA - Modeling
- SAP HANA - Data Warehouse
- SAP HANA - Tables
- SAP HANA - Packages
- SAP HANA - Attribute View
- SAP HANA - Analytic View
- SAP HANA - Calculation View
- SAP HANA - Analytic Privileges
- SAP HANA - Information Composer
- SAP HANA - Export and Import
- SAP HANA Reporting
- SAP HANA - Reporting View
- Bi 4.0 Connectivity to HANA Views
- SAP HANA - Crystal Reports
- SAP HANA - Excel Integration
- SAP HANA Security
- SAP HANA - Security Overview
- User Administration & Management
- SAP HANA - Authentications
- SAP HANA - Authorization methods
- SAP HANA - License Management
- SAP HANA - Auditing
- SAP HANA Data Replication
- SAP HANA - Data Replication Overview
- SAP HANA - ETL Based Replication
- SAP HANA - Log Based Replication
- SAP HANA - DXC Method
- SAP HANA - CTL Method
- SAP HANA - MDX Provider
- SAP HANA Monitoring
- SAP HANA - Monitoring and Alerting
- SAP HANA - Persistent Layer
- SAP HANA - Backup & Recovery
- SAP HANA - High Availability
- SAP HANA - Log Configuration
- SAP HANA SQL
- SAP HANA - SQL Overview
- SAP HANA - Data Types
- SAP HANA - SQL Operators
- SAP HANA - SQL Functions
- SAP HANA - SQL Expressions
- SAP HANA - SQL Stored Procedures
- SAP HANA - SQL Sequences
- SAP HANA - SQL Triggers
- SAP HANA - SQL Synonym
- SAP HANA - SQL Explain Plans
- SAP HANA - SQL Data Profiling
- SAP HANA - SQL Script
- SAP HANA Useful Resources
- SAP HANA - Questions and Answers
- SAP HANA - Quick Guide
- SAP HANA - Useful Resources
- SAP HANA - Discussion
SAP HANA - Security Overview
Security means protecting companys critical data from unauthorized access and use, and to ensure that Compliance and standards are met as per the company policy. SAP HANA enables customer to implement different security policies and procedures and to meet compliance requirements of the company.
SAP HANA supports multiple databases in a single HANA system and this is known as multitenant database containers. HANA system can also contain more than one multitenant database containers. A multiple container system always has exactly one system database and any number of multitenant database containers. AN SAP HANA system that is installed in this environment is identified by a single system ID (SID). Database containers in HANA system are identified by a SID and database name. SAP HANA client, known as HANA studio, connects to specific databases.
SAP HANA provides all security related features such as Authentication, Authorization, Encryption and Auditing, and some add on features, which are not supported in other multitenant databases.
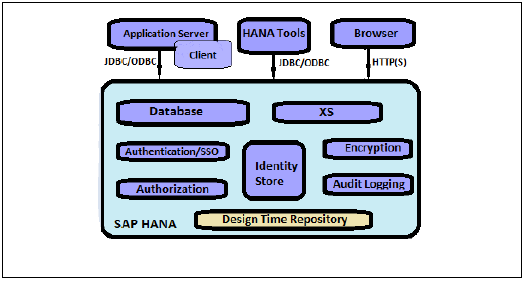
Below given is a list of security related features, provided by SAP HANA −
- User and Role Management
- Authentication and SSO
- Authorization
- Encryption of data communication in Network
- Encryption of data in Persistence Layer
Additional Features in multitenant HANA database −
Database Isolation − It involves preventing cross tenant attacks through operating system mechanism
Configuration Change blacklist − It involves preventing certain system properties from being changed by tenant database administrators
Restricted Features − It involves disabling certain database features that provides direct access to file system, the network or other resources.
SAP HANA User and Role Management
SAP HANA user and role management configuration depends on the architecture of your HANA system.
If SAP HANA is integrated with BI platform tools and acts as reporting database, then the end-user and role are managed in application server.
If the end-user directly connects to the SAP HANA database, then user and role in database layer of HANA system is required for both end users and administrators.
Every user wants to work with HANA database must have a database user with necessary privileges. User accessing HANA system can either be a technical user or an end user depending on the access requirement. After successful logon to system, users authorization to perform the required operation is verified. Executing that operation depends on privileges that user has been granted. These privileges can be granted using roles in HANA Security. HANA Studio is one of powerful tool to manage user and roles for HANA database system.
User Types
User types vary according to security policies and different privileges assigned on user profile. User type can be a technical database user or end user needs access on HANA system for reporting purpose or for data manipulation.
Standard Users
Standard users are users who can create objects in their own Schemas and have read access in system Information models. Read access is provided by PUBLIC role which is assigned to every standard users.
Restricted Users
Restricted users are those users who access HANA system with some applications and they do not have SQL privileges on HANA system. When these users are created, they do not have any access initially.
If we compare restricted users with Standard users −
Restricted users cannot create objects in HANA database or their own Schemas.
They do not have access to view any data in database as they dont have generic Public role added to profile like standard users.
They can connect to HANA database only using HTTP/HTTPS.
