
- Data Comm & Networks Home
- DCN - Overview
- DCN - What is Computer Network
- DCN - Uses of Computer Network
- DCN - Computer Network Types
- DCN - Network LAN Technologies
- DCN - Computer Network Models
- DCN - Computer Network Security
- DCN - Components
- DCN - Connectors
- DCN - Switches
- DCN - Repeaters
- DCN - Gateways
- DCN - Bridges
- DCN - Socket
- DCN - Network Interface Card
- DCN - NIC: Pros and Cons
- DCN - Network Hardware
- DCN - Network Port
- Computer Network Topologies
- DCN - Computer Network Topologies
- DCN - Point-to-point Topology
- DCN - Bus Topology
- DCN - Star Topology
- DCN - Ring Topology
- DCN - Mesh Topology
- DCN - Tree Topology
- DCN - Hybrid Topology
- Physical Layer
- DCN - Physical Layer Introduction
- DCN - Digital Transmission
- DCN - Analog Transmission
- DCN - Transmission media
- DCN - Wireless Transmission
- DCN - Transmission Impairments
- DCN - Multiplexing
- DCN - Network Switching
- Data Link Layer
- DCN - Data Link Layer Introduction
- DCN - Data Link Control & Protocols
- DCN - RMON
- DCN - Token Ring Network
- DCN - Hamming Code
- DCN - Byte Stuffing
- DCN - Channel Allocation
- DCN - MAC Address
- DCN - Address Resolution Protocol
- DCN - Cyclic Redundancy Checks
- DCN - Error Control
- DCN - Flow Control
- DCN - Framing
- DCN - Error Detection & Correction
- DCN - Error Correcting Codes
- DCN - Parity Bits
- Network Layer
- DCN - Network Layer Introduction
- DCN - Network Addressing
- DCN - Routing
- DCN - Internetworking
- DCN - Network Layer Protocols
- DCN - Routing Information Protocol
- DCN - Border Gateway Protocol
- DCN - OSPF Protocol
- DCN - Network Address Translation
- DCN - Network Address Translation Types
- Transport Layer
- DCN - Transport Layer Introduction
- DCN - Transmission Control Protocol
- DCN - User Datagram Protocol
- DCN - Congestion Control
- DCN - TCP Service Model
- DCN - TLS Handshake
- DCN - TCP Vs. UDP
- Application Layer
- DCN - Application Layer Introduction
- DCN - Client-Server Model
- DCN - Application Protocols
- DCN - Network Services
- DCN - Virtual Private Network
- DCN - Load Shedding
- DCN - Optimality Principle
- DCN - Service Primitives
- DCN - Services of Network Security
- DCN - Hypertext Transfer Protocol
- DCN - File Transfer Protocol
- DCN - Secure Socket Layer
- Network Protocols
- DCN - ALOHA Protocol
- DCN - Pure ALOHA Protocol
- DCN - Sliding Window Protocol
- DCN - Stop and Wait Protocol
- DCN - Link State Routing
- DCN - Link State Routing Protocol
- Network Algorithms
- DCN - Shortest Path Algorithm
- DCN - Routing Algorithm
- DCN - Leaky Bucket Algorithm
- Wireless Networks
- DCN - Wireless Networks
- DCN - Wireless LANs
- DCN - Wireless LAN & IEEE 802.11
- DCN - IEEE 802.11 Wireless LAN Standards
- DCN - IEEE 802.11 Networks
- Multiplexing
- DCN - Multiplexing & Its Types
- DCN - Time Division Multiplexing
- DCN - Synchronous TDM
- DCN - Asynchronous TDM
- DCN - Synchronous Vs. Asynchronous TDM
- DCN - Frequency Division Multiplexing
- DCN - TDM Vs. FDM
- DCN - Code Division Multiplexing
- DCN - Wavelength Division Multiplexing
- Miscellaneous
- DCN - Shortest Path Routing
- DCN - B-ISDN Reference Model
- DCN - Design Issues For Layers
- DCN - Selective-repeat ARQ
- DCN - Flooding
- DCN - E-Mail Format
- DCN - Cryptography
- DCN - Unicast, Broadcast, & Multicast
- DCN - Network Virtualization
- DCN - Flow Vs. Congestion Control
- DCN - Asynchronous Transfer Mode
- DCN - ATM Networks
- DCN - Synchronous Vs. Asynchronous Transmission
- DCN - Network Attacks
- DCN - WiMax
- DCN - Buffering
- DCN - Authentication
- DCN Useful Resources
- DCN - Quick Guide
- DCN - Useful Resources
- DCN - Discussion
Token Ring Network (IEEE Standard 802.5) in Computer Networks
Token Ring Network (IEEE Standard 802.5)
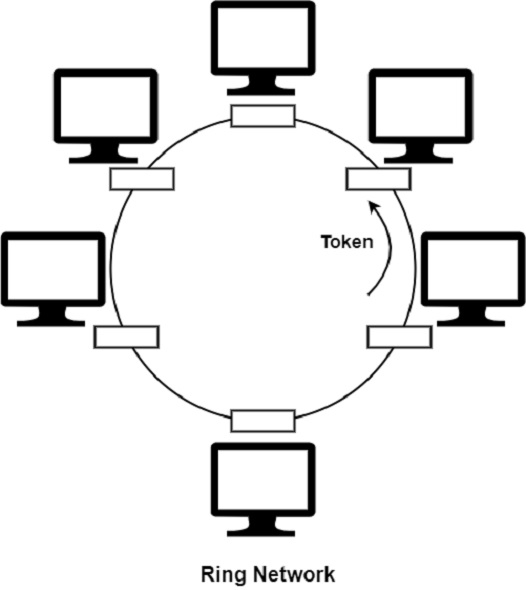
In a token ring, a special bit pattern, known as a token, circulates around the ring when all the stations are idle. Token Ring is formed by the nodes connected in ring format, as shown in the diagram below.
The principle used in the token ring network is that a token is circulating in the ring, and whichever node grabs that token will have the right to transmit the data.
Whenever a station wants to transmit a frame, it inverts a single bit of the 3-byte token, which instantaneously changes it into a normal data packet. As there is only one token, there can be only one transmission at a time.
Since the token rotates in the ring, it is guaranteed that every node gets the token within some specified time. So there is an upper bound on the time of waiting to grab the token so that starvation is avoided. There is also an upper limit of 250 on the number of nodes in the network.
The ring network is depicted in the figure given below
Modes of Operation in Token Ring Network (IEEE Standard 802.5)
There are various modes of operations which are as follows
-
Listen Mode In the listen mode, the incoming bits are simply transmitted to the output line with no further action taken.
-
Talk or Transmit Node The ring interface is set to the talk or transmit node when the station connected to the ring interface has acquired a token. The direct input to output connection through the single bit buffer is disconnected.
-
By-pass Mode This mode reaches when the node is down. Any data is just bypassed. There is no one-bit delay in this mode.
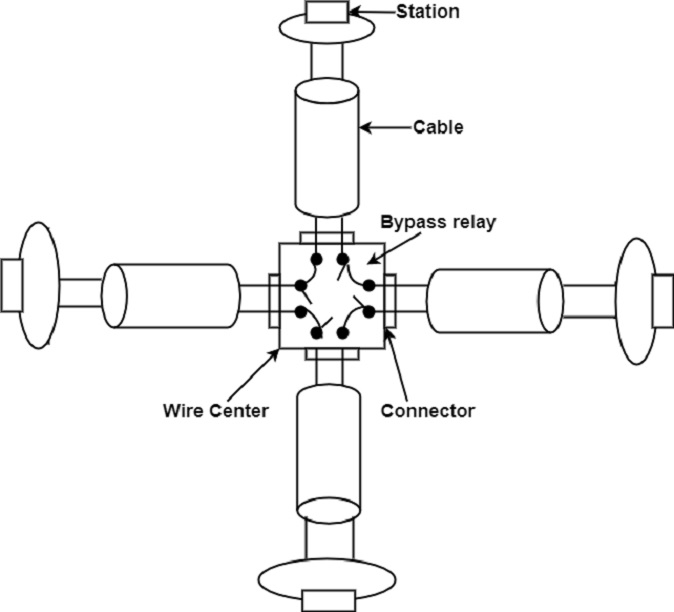
Handling Breakage
The main problem with a ring network is that the network goes down when the ring cable breaks down or gets tempered. The solution to this problem is the use of a wire centre, as shown in the figure.
This wire center bypasses the terminals that have gone down from the ring. This is done by connecting the bypass relay for that station. These relays are generally controlled by the software that operates automatically in case of station failure. The use of a wire center improves the reliability and maintainability of the ring network.
Priority and Reservation
In IEEE 802.5, each station has a priority code. As a token circulates on the ring, any station which wants to transmit the frame may reserve the token by entering its priority code in the Access Control (AC) field of the token frame or data frame.
Time Bounding
A station that is in possession of the token only can transmit his frames. It may transmit one or more data frames but before the expiry of Token Holding Time (THT). Typically, this time is 10 milliseconds. After the THT, the token frame must be handed over to some other station.
The Monitor Station
The monitor station sets the timer on when each time the token passes. If the token does not regenerate in the allotted time, it is assumed to be lost, and then the monitor station generates a new token and sends it to the ring. If the monitor fails, a second station is designated as back-up.