Article Categories
- All Categories
-
 Data Structure
Data Structure
-
 Networking
Networking
-
 RDBMS
RDBMS
-
 Operating System
Operating System
-
 Java
Java
-
 MS Excel
MS Excel
-
 iOS
iOS
-
 HTML
HTML
-
 CSS
CSS
-
 Android
Android
-
 Python
Python
-
 C Programming
C Programming
-
 C++
C++
-
 C#
C#
-
 MongoDB
MongoDB
-
 MySQL
MySQL
-
 Javascript
Javascript
-
 PHP
PHP
What is the TFTP Operation?
TFTP operation is very simple. The client sends a read or write request at the server's UDP port 69. The server accepts the request by sharing data messages in case of the read request and sending acknowledgement in the write request. In either case, the server chooses a UDP port for further dialogue and sends its first response to the client through the selected UDP port.
Each data message has a fixed size of the data block (512 octets) and is individually acknowledged. The last data block containing EOF (End of File) or a data block containing less than 512 octets terminates the session. The figure illustrates the mechanism after a diskless client has received the TFTP server's IP address and the boot-file name from the BOOTP server
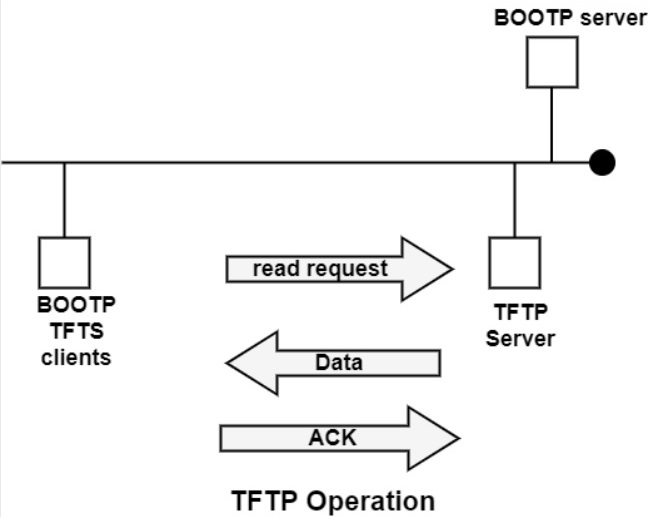
If a TFTP message is lost and if there is no expected response, the message is repeated by the sender after a timeout. Thus, if an acknowledgement is lost, the data message is repeated after a timeout.
Suppose the next data message is repeated after a timeout. If the next data message is not taken after acknowledgement, the last acknowledgement is repeated after the timeout.
Use of TFTP
- TFTP is mainly used during the device bootstrap process for downloading device OS/firmware and configuration documents. It is generally used for copying bootstrap and configuration data between nodes belonging to a similar LAN.
- TFTP is used in positions where all the features of an entire file transfer protocol such as FTP are not required.
- It is used along with boot protocols such as BOOTP and DHCP to initialize devices. Whenever an IP allows the node to boot up, it gets its IP address and other device and network-related parameters through BOOTP or DHCP. As part of these parameters, the users also receive the TFTP server address, bootstrap file and configuration file elements (file name and directory location). The client then uses the TFTP protocol to download the TFTP server's bootstrap image and configuration files.


