
 Data Structure
Data Structure Networking
Networking RDBMS
RDBMS Operating System
Operating System Java
Java MS Excel
MS Excel iOS
iOS HTML
HTML CSS
CSS Android
Android Python
Python C Programming
C Programming C++
C++ C#
C# MongoDB
MongoDB MySQL
MySQL Javascript
Javascript PHP
PHP
- Selected Reading
- UPSC IAS Exams Notes
- Developer's Best Practices
- Questions and Answers
- Effective Resume Writing
- HR Interview Questions
- Computer Glossary
- Who is Who
What is Ransomware Attack?
If you find that documents, pictures, and other files on your system are automatically renamed by appending an unknown suffix, then it might be because of a Ransomware attack. In this guide, we would discuss in detail what Ransomware is, how it works, and how to prevent Ransomware attacks on your system.
What is Ransomware?
Ransomware is one of the deadliest malware programs that, after infiltrating the system, lock the files with strong encryption. After encrypting the files, the cybercriminal(s) behind the attack would ask the victim for the ransom in return for an encrypting tool or key.
Without the decrypting key or tool, it is almost impossible to unlock the files from strong encryption. The Ransomware attack is usually conducted on an organization rather than an individual for getting a significant monetary gain.

How does Ransomware enter your system?
The entry method of the Ransomware is the same as most other malware. It can infiltrate your system through the following ways:
Cybercriminals can use Phishing techniques, for example, sending an email with malicious attachments.
If you click on any unsolicited link without knowing the source behind it, you can introduce Ransomware or any other dangerous malware to your system.
Downloading the freeware from unknown sources
Inserting an infected USB drive or attaching an infectious hard drive can transfer the Ransomware on your system.
How does Ransomware Work?
After infiltrating your system, the Ransomware would lock all your essential files with strong encryption and append every file with an extension. That extension is generally the name of the Ransomware. Take the example of XYZ Ransomware. After entering the system, it would rename the file by appending the ".XYZ" extension. For example, a file name 'File1..jpg' will be renamed to 'File1..jpg.XYZ'.
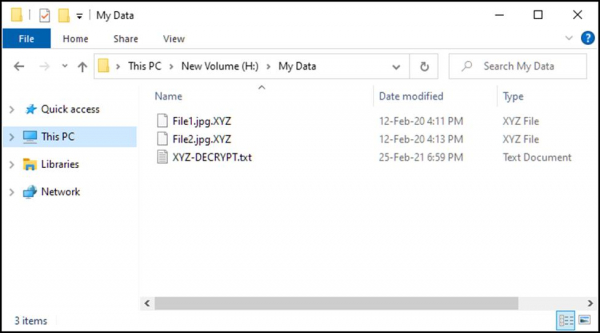
Once the encryption process is completed, generally, a text file is generated containing all the information related to Ransomware and details to contact the person behind it.
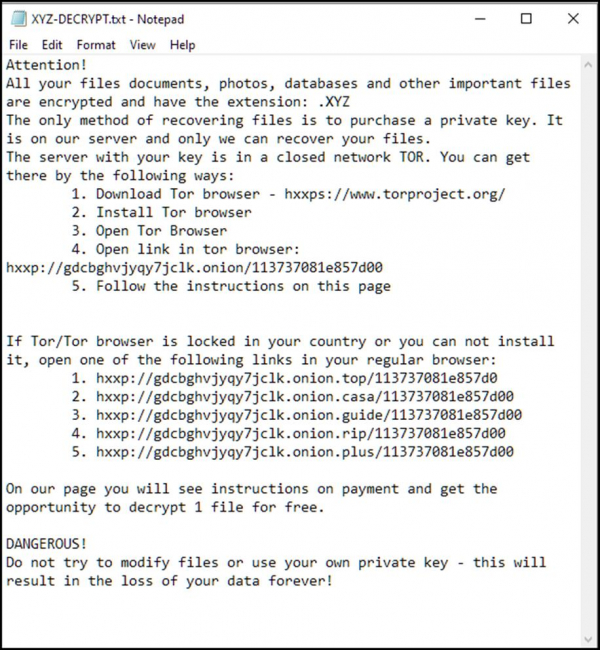
It is challenging to decrypt the encrypted files without involving the cybercriminals behind the encryption. It is because Ransomware attacks with unique encryption, which means it is impossible to decrypt files without tools that can be provided only by cybercriminals who designed Ransomware.
However, many times, even after paying the ransom, the files are not decrypted by the cybercriminals.
How to Prevent Ransomware Attacks?
It is said that prevention is better than cure. However, in the case of Ransomware attacks, prevention is probably the only cure. Unlike other malware attacks, you cannot undo the damage caused by Ransomware. To prevent Ransomware attacks on your system, follow these tips:
Most Ransomware takes advantage of the software's or operating system's vulnerabilities and attacks the system. Therefore, it is always recommended to keep all your applications and OS updated. Updating the OS will not only fix the potential vulnerabilities but will also install the latest security definitions and patches.
Always get your applications and games from the trusted sources. Untrustworthy sources like torrents are the most prominent gateway for malware programs like Ransomware. Never visit the illicit sites in the greed of getting the paid software for free.
While installing software, always pay attention if it is installing any additional program. Also, never ignore any security warning during the installation of the application.
While downloading software from the internet, if you get a security alert from the firewall, don't ever ignore it and immediately stop the download.
Keep installed a robust antimalware security solution on your device. Since most free security solutions are weak in providing protection against Ransomware, it is better to go for a paid one. Along with the antimalware program, configure a firewall too to monitor your network.
Regularly back up your system or all your essential data. This way, even if there is a Ransomware attack on your device, you can nullify it.
-
Always follow healthy browsing practices like:
Never click on an unsolicited link.
Avoid opening the email and attachments from unknown or unverified senders.
Never visit any malicious site.

