
 Data Structure
Data Structure Networking
Networking RDBMS
RDBMS Operating System
Operating System Java
Java MS Excel
MS Excel iOS
iOS HTML
HTML CSS
CSS Android
Android Python
Python C Programming
C Programming C++
C++ C#
C# MongoDB
MongoDB MySQL
MySQL Javascript
Javascript PHP
PHP
- Selected Reading
- UPSC IAS Exams Notes
- Developer's Best Practices
- Questions and Answers
- Effective Resume Writing
- HR Interview Questions
- Computer Glossary
- Who is Who
What are different types of multiple access protocols?
Multiple access protocols are generally used to coordinate access to link, here nodes can regulate their transmission onto the shared broadcast channels by using multiple access protocol, It is used on both wired and wireless LAN and satellite network.
Multiple nodes can transmit frames at the same time, if so the transmitted frame collides at the entire receiver. When there is a collision, there is no acknowledgement to the receiver that the frame is transmitted or not.
Thus, all frames involved in the collision are lost, and the broadcast channel is wasted during the collision interval. To rectify this problem Multiple Access protocol is implemented.
Various Multiple access channels are − Shared wire (Ethernet), shared wireless, satellite.
Multiple access protocols arise not only in the communications systems but as well in a lot of other systems such as the computer system, the storage facility or the server of any kind, where the resources are shared through the number of independent users.
Classification of Multiple Access Protocol
The multiple access protocol is classified into following types −
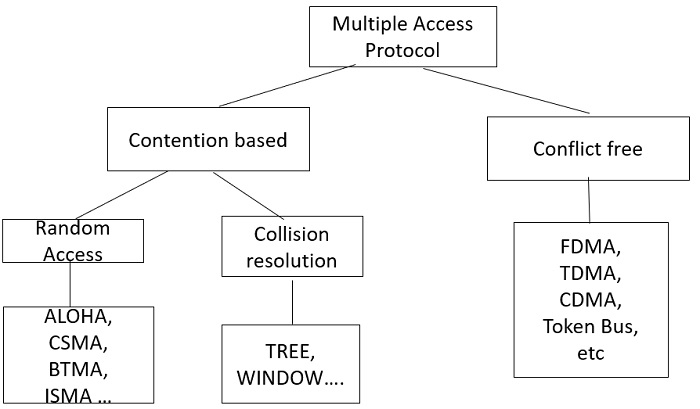
Random access MAC protocols
The random access MAC protocols are explained below in a stepwise manner.
Step 1 − In a random access MAC protocol, the transmitting node always transmits at full strength of the channel.
Step2 − When there is a collision, each node that is involved in the collision repeatedly retransmits its frame until the frame gets through without a collision.
Step 3 − But when a node experiences a collision, it does not necessarily retransmit the frame right away. Instead, it waits a random delay before retransmitting the frame.
Step 4 − Each node involved in a collision chooses independent random delays. Because after a collision the random delays are independently chosen, it is possible that one of the nodes will pick a delay that is sufficiently less than the delays of the other colliding nodes, and will therefore be able to transmit its frame into the channel without a collision.
Step 5 − Such a system is more random and there is no guarantee that a station will be able to transmit in the given medium due to more possibilities of collisions.
Step 6 − But there are certain protocols that help to reduce the collisions.
The protocols used here are as follows −
- ALOHA
- SLOTTED ALOHA
- CSMA(Carrier Sense Multiple Access)
- CSMA-CD(CSMA with Collision Detection)
- CSMA-CA(CSMA with Collision avoidance)
Channel Partitioning Protocols or conflict free protocol
The channel partitioning or conflict free protocols are explained below in stepwise manner.
Step 1 − The protocols used in his format is Time Division Multiplexing (TDM) and Frequency Division Multiplexing (FDM) the other is Code Division Multiple Access (CDMA) here, as the name says, the channel is partitioned on the basis of frequency, time depending on the protocol used and each participant/sender uses the channel in the time or frequency slot assigned specifically for them.
Step 2 − This type of partitioning ensures that each user has a predefined time/frequency slot to use the medium.
Step 3 − Suppose there are n nodes in TDM. The transmission time is divided into n nodes, and each node would be given a particular slot to transmit over the medium.
Step 4 − In FDM the frequency bandwidth is divided into certain slots and each node would send its transmission in that particular frequency.
Step 5 − In CDMA each node is assigned a unique code to transmit so that multiple transmissions can take place between different nodes, without the danger of collision.
Functions of MAC
The functions performed by Medium Access Protocol are given below −
It delimits and recognizes the frames
It is responsible for addressing at layer 2
Error checking by using frame check sequences (FCS)
Physical transmission medium's access control

