
- SAP Security - Home
- SAP Security - Overview
- User Authentication & Management
- Network Communication Security
- Protecting Standard Users
- Un-authorizing Logons Protections
- System Authorization Concept
- SAP Security - Unix Platform
- SAP Security - Windows Platform
- SAP Security - Databases
- User Authentication & Single SignOn
- SAP Security - Logon Tickets
SAP Security - Unix Platform
You need to take various security measures while using certain Unix Properties, Files or Services, Protecting Password Files and Deactivating BSD Remote Services for rlogin and remsh.
Password Protection
In a Unix platform, an attacker can use dictionary attack program to discover password information stored in the Unix OS. You can store the passwords in a shadow password file and only a root user can have access to this file to improve the security in a system.
Deactivating Remote Services
BSD Remote services allows remote access to Unix systems. When a remote connection is initiated /etc/host.equiv and $HOME/.rhosts are used and in case when these files contain information about the hostname and IP address of connection source or any wildcard characters, there is no need to enter the password while logging in.
The remote services rlogin and remsh are security threat in this scenario and you need to deactivate these services. You can deactivate these services by going to inetd.conf file in the Unix system.
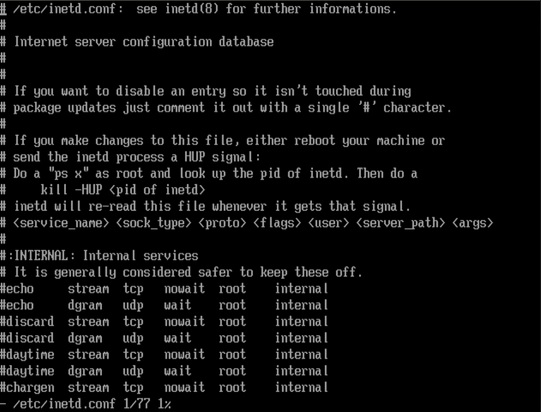
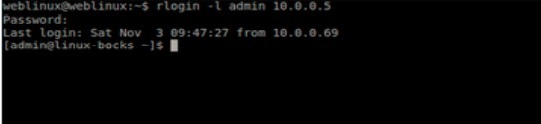
In a Unix system, rlogin is a remote shell client (like SSH), which is designed to be fast and small. It is not encrypted, which may have some small drawbacks in high security environments, but it can operate at very high speeds. Both the server and client do not use a lot of memory.
Securing Network File System in UNIX
In a UNIX platform, a Network File System is used to access transport and work directories over the network from a SAP system. To access work directories, the authentication process involves network addresses. It is possible that unauthorized access can be gained by attackers over the Network File System using IP spoofing.
To make the system secure, you shouldnt distribute home directory over the Network File System and write authorization to these directories should be carefully assigned.
SAP System Directory Access for SAP System in UNIX
You should set the following access rights for SAP System Directories in UNIX −
| SAP Directory | Octal form Access Privilege | Owner | Group |
|---|---|---|---|
| /sapmnt/<SID>/exe | 775 | <sid>adm | sapsys |
| /sapmnt/<SID>/exe/saposcol | 4755 | root | sapsys |
| /sapmnt/<SID>/global | 700 | <sid>adm | sapsys |
| /sapmnt/<SID>/profile | 755 | <sid>adm | sapsys |
| /usr/sap/<SID> | 751 | <sid>adm | sapsys |
| /usr/sap/<SID>/<Instance ID> | 755 | <sid>adm | sapsys |
| /usr/sap/<SID>/<Instance ID>/* | 750 | <sid>adm | sapsys |
| /usr/sap/<SID>/<Instance ID>/sec | 700 | <sid>adm | sapsys |
| /usr/sap/<SID>/SYS | 755 | <sid>adm | sapsys |
| /usr/sap/<SID>/SYS/* | 755 | <sid>adm | sapsys |
| /usr/sap/trans | 775 | <sid>adm | sapsys |
| /usr/sap/trans/* | 770 | <sid>adm | sapsys |
| /usr/sap/trans/.sapconf | 775 | <sid>adm | sapsys |
| <home directory of <sid>adm> | 700 | <sid>adm | sapsys |
| <home directory of <sid>adm>/* | 700 | <sid>adm | sapsys |