
- Home
- Internet Overview
- Intranet Overview
- Extranet Overview
- Internet reference Models
- Internet Domain Name System
- Internet Services
- Internet Connectivity
- Internet Protocols
- Electronic Mail Basics
- E-Mail Overview
- E-Mail Protocols
- E-Mail Working
- E-Mail Operations
- E-mail Features
- E-Mail Etiquettes
- E-mail Security
- E-mail Providers
- Website Development
- Websites Overview
- Websites Types
- Website Designing
- Websites Development
- Website Publishing
- Website URL Registration
- Website Hosting
- Website Security
- Search Engine Optimization
- Website Monetization
- World Wide Web
- WWW Overview
- Web Pages
- Web Browsers
- Web Servers
- Proxy Servers
- Search Engines
- Internet Collaboration
- Collaboration Overview
- Mailing List
- Usenet Newsgroup
- Online Education
- Social Networking
- Internet Security and Privacy
- Internet Security Overview
- Data Encryption
- Digital Signature
- Firewall Security
- Internet Web Programming
- HTML
- CSS
- JavaScript
- PHP
- Internet Useful Resources
- Internet Quick Guide
- Internet Useful Resources
- Internet Discussion
Extranet Overview
Extranet
Extranet refers to network within an organization, using internet to connect to the outsiders in controlled manner. It helps to connect businesses with their customers and suppliers and therefore allows working in a collaborative manner.
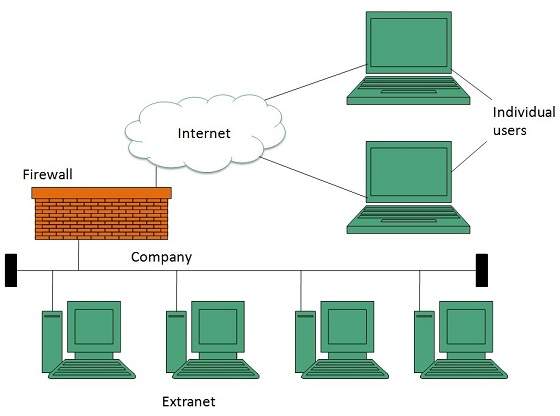
Implementation
Extranet is implemented as a Virtual Private Networks (VPN) because it uses internet to connect to corporate organization and there is always a threat to information security. VPN offers a secure network in public infrastructure (Internet).
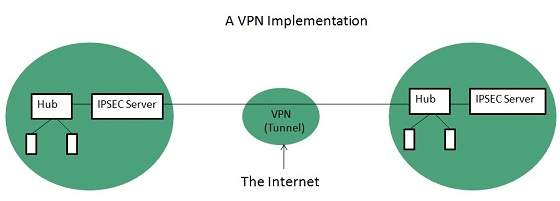
Key Points
The packet is encapsulated at boundary of networks in IPSEC complaint routers.
It uses an encryption key to encapsulate packets and IP addresses as well.
The packet is decoded only by the IPSEC complaint routers or servers.
The message is sent over VPN via VPN Tunnel and this process is known as tunneling.
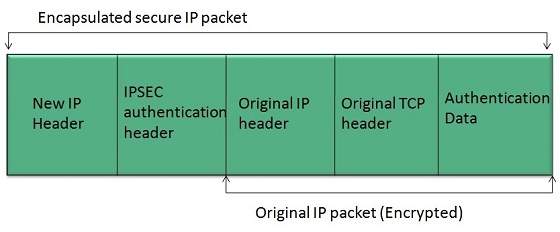
VPN uses Internet Protocol Security Architecture (IPSEC) Protocol to provide secure transactions by adding an additional security layer to TCP/IP protocol. This layer is created by encapsulating the IP packet to a new IP packet as shown in the following diagram:
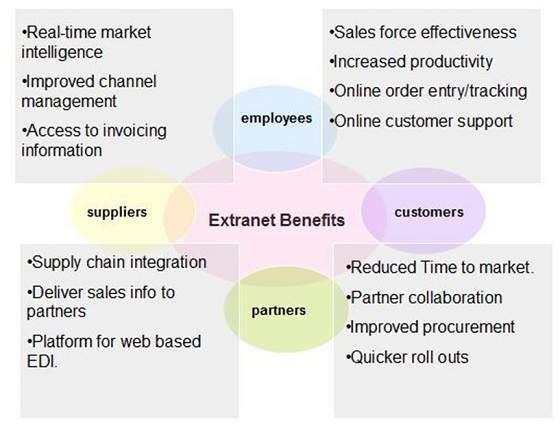
Benefits
Extranet proves to be a successful model for all kind of businesses whether small or big. Here are some of the advantages of extranet for employees, suppliers, business partners, and customers:
Issues
Apart for advantages there are also some issues associated with extranet. These issues are discussed below:
Hosting
Where the extranet pages will be held i.e. who will host the extranet pages. In this context there are two choices:
Host it on your own server.
Host it with an Internet Service Provider (ISP) in the same way as web pages.
But hosting extranet pages on your own server requires high bandwidth internet connection which is very costly.
Security
Additional firewall security is required if you host extranet pages on your own server which result in a complex security mechanism and increase work load.
Accessing Issues
Information can not be accessed without internet connection. However, information can be accessed in Intranet without internet connection.
Decreased Interaction
It decreases the face to face interaction in the business which results in lack of communication among customers, business partners and suppliers.
Extranet vs. Intranet
The following table shows differences between Extranet and Intranet:
| Extranet | Intranet |
|---|---|
| Internal network that can be accessed externally. | Internal network that can not be accessed externally. |
| Extranet is extension of company's Intranet. | Only limited users of a company. |
| For limited external communication between customers, suppliers and business partners. | Only for communication within a company. |