
 Data Structure
Data Structure Networking
Networking RDBMS
RDBMS Operating System
Operating System Java
Java MS Excel
MS Excel iOS
iOS HTML
HTML CSS
CSS Android
Android Python
Python C Programming
C Programming C++
C++ C#
C# MongoDB
MongoDB MySQL
MySQL Javascript
Javascript PHP
PHP
- Selected Reading
- UPSC IAS Exams Notes
- Developer's Best Practices
- Questions and Answers
- Effective Resume Writing
- HR Interview Questions
- Computer Glossary
- Who is Who
How to Detect Remote Access to My Computer?
An authorized user can access a computer system or network remotely from a separate location using a network connection, often the internet. Remote access allows users to engage with the procedures and services they need, even when they are physically far away. This is essential for employees that work remotely, freelance, travel, or operate out of international offices.
Remote users have constant access to data and other infrastructure elements from servers or devices connected to the network. Consequently, productivity increases and workers are more prepared to collaborate with colleagues from around the globe. Businesses can hire top talent from anywhere, tear down organizational barriers, and promote cooperation across departments, companies, and locations by using a remote access technique.
The remote access technique has a number of benefits and drawbacks.
Advantages:
Better productivity and teamwork are achieved through universal accessibility, customizable configuration, efficient costs, complete control over authorization and access, centralized storage and backups, and shared resources.
Disadvantages:
Complications include the working environment, sophisticated technology, version issues and information vulnerabilities, hardware problems that still require on-site maintenance, security threats, and privacy concerns.
Start by cutting off your internet connection if you believe anyone is remotely controlling your computer. This will cease any remote sessions immediately. There are simple techniques to determine if someone was remotely accessing your computer system once you have securely unplugged it. We'll demonstrate how to lock down your computer, search for indications of remote connections and access, and avoid further invasions.
Searching for Breach Symptoms
Remove the internet connection from your PC
Disconnect the device from the internet if you think someone is using it to access your device remotely. This means unplugging any Ethernet cords and disabling your Wi-Fi.
Your cursor is moving unintentionally, programs appearing on your screen, or data proactively being destroyed are some of the most visible indications of ongoing access. Not all pop-ups, though, need to be taken seriously; many programs that update themselves automatically produce pop-ups when they do so.
It's only sometimes the case that someone has gained remote access to your machine if you are experiencing slow internet or strange apps.
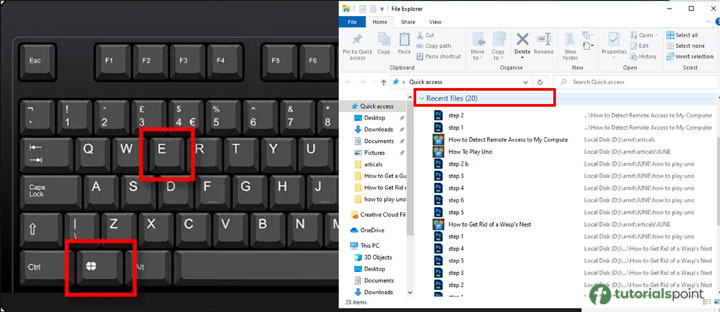
Look at the list of recently used programs and files
Macs and Windows Computers make it simple to examine a menu of the most recent programs you've used in addition to your last visited files. If you see anything unusual in these listings, your computer could be compromised:
Windows ? Press the Windows Key + E to launch File Explorer and view the most recently opened files. Check the "Recent files" area at the bottom of the main window to see any files that you don't recognize. A list of recently used apps is also visible at the top of the Start menu.
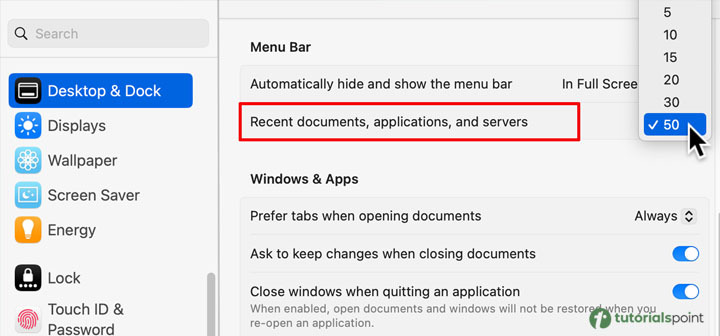
Mac ? Select Recent Items from the Apple menu in the top-left corner of the display. Now, by selecting Applications, Documents, or Servers, you may view a list of recently used applications, files, and remote outbound connections.
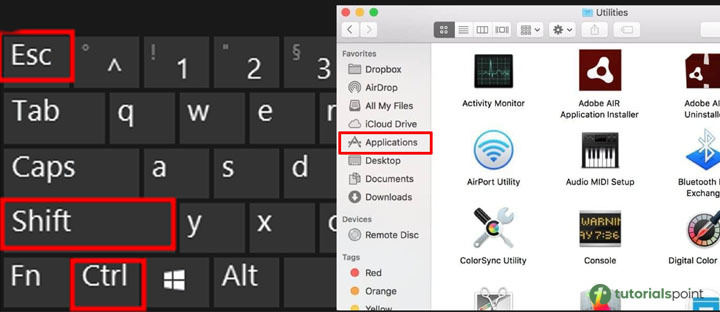
Launch Activity Monitor or Task Manager
You may use these tools to determine what programs are executing on your computer. Ctrl + Shift + Esc on a Windows computer.
Double-click the Utilities folder in the Finder's Applications folder, and double Activity Monitor in Mac OS.
Check your list of currently running programs for remote access programs
In the Task Manager or Activity Monitor, glance through the list of active apps and note any that stand out as suspicious or unusual. Popular remote access applications, including VNC, RealVNC, TightVNC, UltraVNC, AnyDesk, GoToMyPC, and TeamViewer, might have been downloaded without your consent.
Search for any programs that appear shady or that you need to familiarize yourself with. If you are still determining a program, you can search the internet for its purpose.
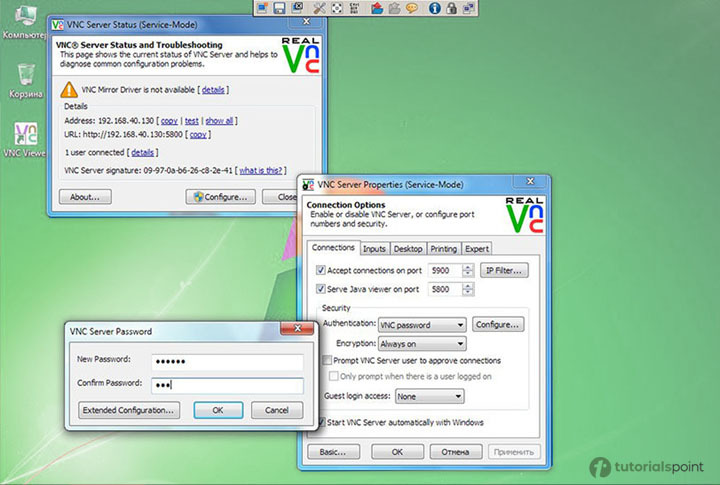
Keep an eye out for eerily high CPU utilization
This will be shown in the Activity Monitor or Task Manager. Heavy CPU consumption, even when you aren't using your device, might mean that programs are operating in the background that you may not have allowed. High CPU utilization is frequent and isn't a sign of a cyberattack.
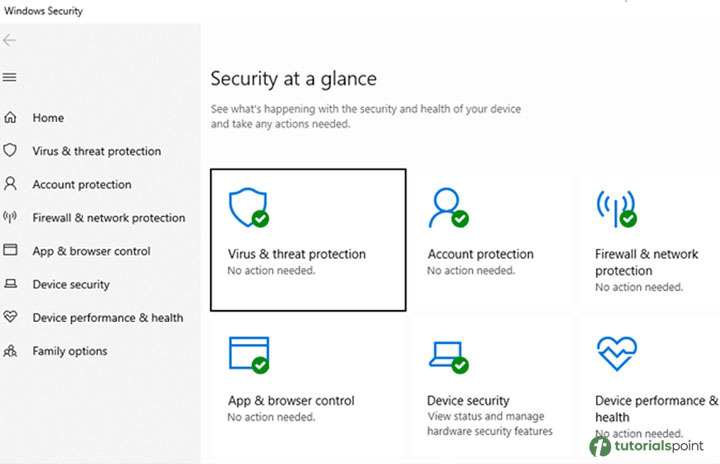
Check your machine for viruses and malicious software.
Use the pre-installed vulnerability scanners in Settings > Update & Security > Windows Security in Windows to look for malicious programs. Mac OS is highly secure in terms of security and anti-cyberattack measures, so there is not much need to worry if you are using a macOS device.
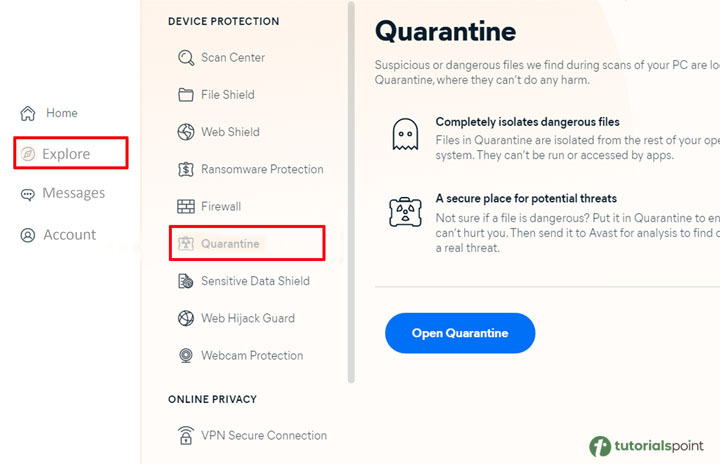
Remove any suspicious materials you find in Quarantine
Quarantining any objects that your anti-virus or anti-malware software finds during the check can stop them from damaging your device further.
Your passwords should all be changed frequently
A keylogger was used to capture all of your credentials if your device was hacked. If necessary, reset the password from all your numerous accounts once the virus is gone. It is best to utilize a different password for several accounts.
Now, this is the last and final option; if none of the precautions and actions can help you.
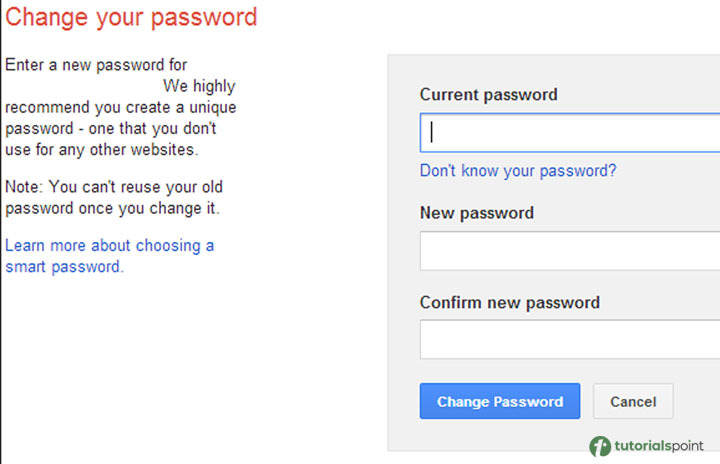
If you cannot remove the infiltration, conduct a complete system reset.
The only way to be sure that you are clean is to clean your system and reinstall the operating system if you continue to have incursions or are worried that you could still be contaminated. Data crucial to you should be backed up beforehand because everything will be erased and reset.
Check every file before backing up any files from a compromised device. Resurrecting an outdated file could result in an invasion again.
Now that was how to detect remote access intrusions in your device to minimize data loss and privacy issues. Now let's discuss the ways to prevent further such incidents.
Update your anti-virus and malware protection programs
Often these assaults will be discovered by security software that is updated before they occur. Windows Defender is a capable anti-virus that runs in the background and receives automatic updates as part of the operating system. Additionally, many free apps are offered, including BitDefender, avast! Etc. Installing an anti-virus application is all that is necessary.
Windows machines come with Windows Defender pre-installed, a reliable anti-virus program. Windows Defender will immediately turn off if you set up an alternative virus protection product.
Use links or attachments with extreme caution
Among the most popular methods for malicious software and viruses to infect your machine is through email attachments. Always open links sent to you by someone you know and trust, but then again, be sure they meant to. If any of your associates have an infection, they can unknowingly send forward attachments containing the infection.
Be cautious about choosing secure and original passwords
You must select a different, challenging password for each password-protected system or software you use. This should ensure that a cybercriminal cannot access one service using the credentials from another account or service that has been compromised.
Prevent using public Networks when possible
Considering that you have no authority over the network, public Wi-Fi hotspots are dangerous. You need to find out whether another person utilizing the space is watching the data in and out of your device.
They might be able to access your active online session or do more harm.

