
 Data Structure
Data Structure Networking
Networking RDBMS
RDBMS Operating System
Operating System Java
Java MS Excel
MS Excel iOS
iOS HTML
HTML CSS
CSS Android
Android Python
Python C Programming
C Programming C++
C++ C#
C# MongoDB
MongoDB MySQL
MySQL Javascript
Javascript PHP
PHP
- Selected Reading
- UPSC IAS Exams Notes
- Developer's Best Practices
- Questions and Answers
- Effective Resume Writing
- HR Interview Questions
- Computer Glossary
- Who is Who
How OSPF routes the packets from source to destination?
Open Shortest Path First (OSPF) is a router protocol used to find the best path for packets as they pass through a set of connected networks.
This protocol is designated by the Internet Engineering Task Force (IETF) one of the Interior Gateway Protocols (IGPs) aimed at traffic moving around within a larger autonomous system network like a single enterprise's network, which may in turn be made up of many separate local area networks linked through routers.
Explanation
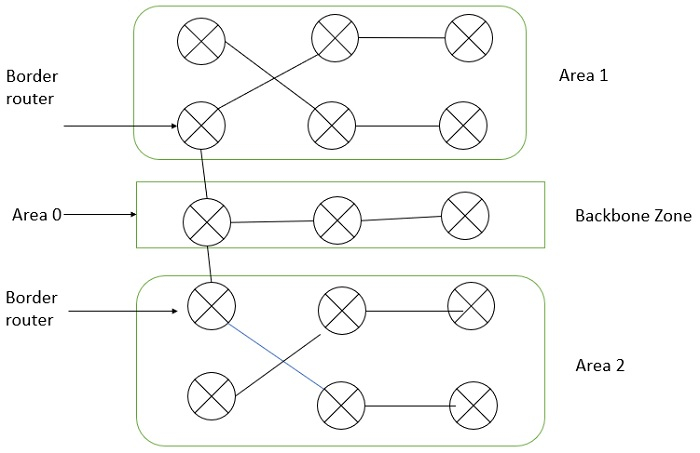
Area 1 Border router Area 0 Backbone zone Border router Area 2 OSPF.
OSPF protocol is called a link state routing protocol, which maintains link state databases. The state of a route in the network is the cost. OSPF protocol allows every router to calculate the cost of the routes to any given reachable destination.
A router interface with OSPF will advertise its link cost to neighbouring routers through multicast procedure, known as the hello procedure. This network is divided into areas that can simplify administration and optimize traffic and resource utilization.
Areas are represented by 32 bit dot-decimal representation. By convention Area 0 represents the backbone zone of OSPF network as shown in above figure.
Each area must have a connection with the OSPF backbone zone. Such connections are implemented by an interconnecting router, known as an area border router (ABR) as shown in above figure.
The Border Router implements separate link-state databases for each area it is connected to and maintains summarized routes for all areas in the network. OSPF detects changes in the network topology, such as link failures, and it converges on a new loop-free routing structure in very less time.
In OSPF information is sent to every node so traffic will be very high as we have to do flooding. Link State Routing is complex as it uses Dijkstra's algorithm to find the shortest path between nodes.
The Border router will take all the flooded packets and will summarize the information. The entire information about an area will be kept in one packet and it will be sent to other areas. The border router will forward the information to the backbone router and the backbone router will forward the information to the border router of another area.
OSPF packet format
The OSPF packet format is as follows −
0 8 16 31
| Version | Type | Message |
|---|---|---|
| Source Address | ||
| AreaID | ||
| Checksum | Authentication Type | |
| Authentication | ||
Here,
Version − It represents the current version
Type − represents the type (1–5) of OSPF message.
- Type 1 − “hello” message,
- Type 2 − request,
- Type 3 − send,
- Type 4 − acknowledge the receipt of link state messages,
- Type 5 − reserved.
Message Length − Represents the length of the message to be exchanged.
SourceAddr − Identifies the sender.
AreaId − 32-bit identifier of the area in which the node is located.
Checksum − 16-bit internet checksum.
Authentication type − 1 (normal password), 2 (cryptographic authentication).
Authentication − It contains password or cryptographic checksum.

