
 Data Structure
Data Structure Networking
Networking RDBMS
RDBMS Operating System
Operating System Java
Java MS Excel
MS Excel iOS
iOS HTML
HTML CSS
CSS Android
Android Python
Python C Programming
C Programming C++
C++ C#
C# MongoDB
MongoDB MySQL
MySQL Javascript
Javascript PHP
PHP
- Selected Reading
- UPSC IAS Exams Notes
- Developer's Best Practices
- Questions and Answers
- Effective Resume Writing
- HR Interview Questions
- Computer Glossary
- Who is Who
What are Digital Signatures and how do they work?
Digital Signature is a mathematical technique which is used to authenticate a digital document. This is equivalent to handwritten signature or a stamped seal and offers far more security and integrity to the message or digital document. It solves the problem of impersonation in digital communications by providing evidence of origin, identity and status of the digital transactions. Many countries like the United States of America consider digital signatures as legal. They even publish public laws, private laws and the Budget with digital signatures.

How does a Digital Signature Work?
Digital signatures are based on asymmetric cryptography, which means that the information can be shared using a public key cryptography, and uses both public and private keys to encrypt and decrypt data. These two keys are not identical. There will be one public key which can be shared with everyone and the Private key is known only to the user. To understand it better, we can say public key is the email id which can be shared openly and you can compare the private key to the password of that email id which has to be kept a secret. One has to be very careful to store the private key in a secure place, as there is no way to regain the private key, once it is lost.
When it comes to Block Chain, the digital signatures are one of the aspects which ensures the security and integrity of the data which is written into the Block Chain. They are the used to secure transactions and prevent external tampering. Digital Signatures use asymmetric cryptography which means the information of the cryptocurrency can be shared on the public ledger with everyone in the network using the public key.
The key success secret of a Bitcoin Protocol is the Bitcoin digital signature and its verification process. The person who sent the message of Bitcoin transaction should possess the corresponding private key, which confirms that he owns the Bitcoins. Anyone in the network can verify the transaction as a result.
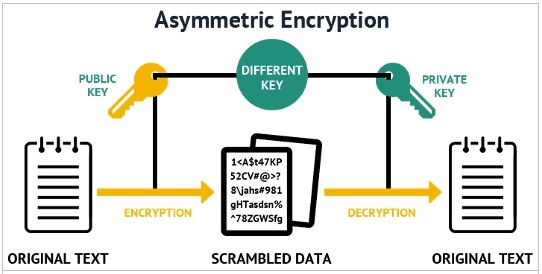
Public key and Private key
The asymmetric cryptography, uses two mutually authenticating cryptographic keys. Public and Private keys are simply extremely large and random numbers. The sender on the network generates a private key and public key. They sign the message with the Digital signature comprising of both the keys and send their transaction message using public key. In the peer to peer network, each transaction is validated by every node. Every node or receiver of the message then checks the transaction using the public key and verifies that the sender is genuine using elliptic curves and complex modular mathematics.
The Public key and private key pair is uniquely related cryptographic keys and they are basically random long numbers comprising alphabets and numbers and goes like this –
3048 0241 00C9 18FA CF8D EB2D EFD5 FD37 89B9 E069 EA97 FC20 5E35 F577 EE31 C4FB C6E4 4811 7D86 BC8F BAFA 362F 922B F01B 2F40 C744 2654 C0DD 2881 D673 CA2B 4003 C266 E2CD CB02 0301 0001
As the key pair is mathematically related, whatever is encrypted with a Public Key can only be decrypted by its corresponding Private Key and vice versa. The sender will encrypt the message using his private key and sends across public key in the matter of Bitcoin Network.
The node or receiver of the message checks it using the verification algorithm that the message has been signed by the sender, and that the Node is a valid user and the holder of the private key to the public key sent. This is how the digital signatures are authenticated and used to secure transactions.

