Article Categories
- All Categories
-
 Data Structure
Data Structure
-
 Networking
Networking
-
 RDBMS
RDBMS
-
 Operating System
Operating System
-
 Java
Java
-
 MS Excel
MS Excel
-
 iOS
iOS
-
 HTML
HTML
-
 CSS
CSS
-
 Android
Android
-
 Python
Python
-
 C Programming
C Programming
-
 C++
C++
-
 C#
C#
-
 MongoDB
MongoDB
-
 MySQL
MySQL
-
 Javascript
Javascript
-
 PHP
PHP
Trojan horse and Trap Door
A threat is designed by hijackers to change the behavior of the process. The threat can reach the system through any path to our system or any organization sever. When the attack happens, it leads to the corruption of data, the stealing of personal information, and the loss of data. The Trojan horse and trap door are some of the program threats which need to be avoided for the proper functioning of the system. So it is a great deal to protect the system from program threats. The protection of files and other resources from misusing the data is important.
Security Problem
Violations
Some of the violations that occur during the program threats are ?
Private information theft such as Credit card numbers, financial information, etc?
Modification of data without authorization.
Theft of resources such as CPU cycles.
The masquerading attack is given below,
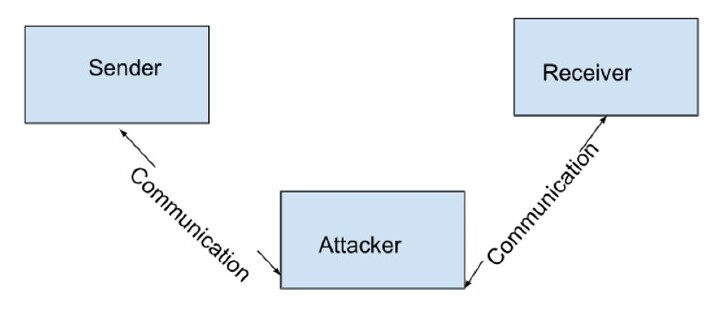
Program Threats
The Program threats are the programs that do malicious tasks, these threats are designed by the hijackers to change the process of any system. There are types of program threats and Trap Door and Trojan horse come under this list.
Trap Door
The trap door is also known as the back door. In which, the Programmer designs a security or secret code that gives a threat to the system. The trap door program threat is one in which the designer keeps a hole in the program, so it can be handled only by the designer. So, it is very difficult to track or find the hole in the program and need to go through the entire source code. This security hole helps the designer access that system. When the system is in an abnormal state, if we take data backup it also contains hidden threats.
Trap Door Purpose
The Legitimate use of trap door threat is the designers don?t actually create a hole or security code, but instead, they leave the space in the code. These blanks are used by the technicians for the emergency purpose of handling the data. The trap door is a kind of secret password used by developers for maintenance purposes.
Effects of Security
The effects of the trapdoor can be easily identified by persons who know the flow of the trapdoor and its vulnerability. Software vendors know the threats of trapdoors and the ways to avoid them, but nowadays users identify the threats and solve themselves without informing about the trap door threats to the specialists.
Attacks
The attacks by trap doors have impacted hundreds and thousands of systems to the threat. Even the companies like Google and Microsoft have been a target to trap doors.
Trojan Horse
Trojan horse is a type of malware that is designed to damage files, steal personal data, redirect the network traffic, monitor the user?s activities, track the user?s browsing activities. These stolen data are in danger that they could be copied to other sources, misuse the sensitive data and can even sell the data in the dark market.
The ways in which we can identify the Trojan horses are by having any Long search routes, particularly in some paths that include the current directory (".") as part of the path, are a risky entry point for Trojan horses. An unaware user may be tricked into starting the wrong application by mistake if a dangerous program with the same name as a safe program (or a common misspelling, such "sl" instead of "ls") is placed anywhere on the path.
Trojan Affects in a System
Trojan horse has been one of the most common program threats. It affects the windows and Mac operating system, well also the Android mobile phones. There are many ways by which Trojan horse enters the system are by downloading the content from the internet like songs and pictures, by downloading any attachments and by accepting the software agreement without reading it. Spyware is also a term that comes along the free downloaded software.
Prevention of Trojan horse
There are certain things needs that need to be followed for the user. They are avoiding clicking links from unknown resources. Access the URL that only starts with HTTP. The links received through emails or text messages are not advised to open directly. Before logging into any website, use their official sites to login using the credentials. The Password must be strong and same password should not be followed for all pages.
There are two solutions to stay away from the Trojan threats, when a user logs out they can go for system print usage data. And also, the keys for login system by pressing the Control-Alt-Delete is a non-trappable key combination being used by many organizations for their security.
Conclusion
The ways of occurrence of threats can be done manually, through the internet or through the devices used. Like the threats are many, the ways to protect them are also in high rate. By proper handling of the system and the networks, the program threats like trap doors and Trojan horses can be demolished or reduced.


