
- Penetration Testing - Home
- Penetration Testing - Introduction
- Penetration Testing - Method
- Testing Vs. Vulnerability Assessment
- Penetration Testing - Types
- Manual and Automated
- Penetration Testing - Tools
- Penetration Testing - Infrastructure
- Penetration Testing - Testers
- Penetration Testing - Report Writing
- Penetration Testing - Ethical Hacking
- Pen Testing Vs. Ethical Hacking
- Penetration Testing - Limitations
- Penetration Testing - Remediation
- Penetration Testing - Legal Issues
Penetration Testing - Ethical Hacking
The fast growth of the internet has changed the way of life for everyone. These days, most of the private and public works are internet dependent. Governments all secret working plans, and operations are internet based. All these things made the life very simple and easily accessible.
But with the good news, there is also a dark face of this development i.e., the criminal hacker. There is no geopolitical limitation of these criminal hackers, they can hack any system from any part of the world. They can damage confidential data and credit history very badly.
Therefore, to protect from the criminal hackers, the concept of the ethical hacker evolved. This chapter discusses the concept and the role of an ethical hacker.
Who are Ethical Hackers?
Ethical hackers are the computer experts who are legally allowed to hack a computer system with the objective to protect from the criminal hackers. An ethical hacker identifies the vulnerabilities and risks of a system and suggests how to eliminate them.
Who are Criminal Hackers?
Criminal hackers are those computer programming experts who hack others systems with the intention to steal data, steal money, defame others credit, destroy others data, blackmail someone, etc.
What can Criminal Hackers do?
Once a system is hacked, a criminal hacker can do anything with that system. The following two images C.C. Palmer, which is published on pdf.textfiles.com, illustrates a simple example of a hacked page −
Here is a screenshot of a webpage taken before it was hacked −
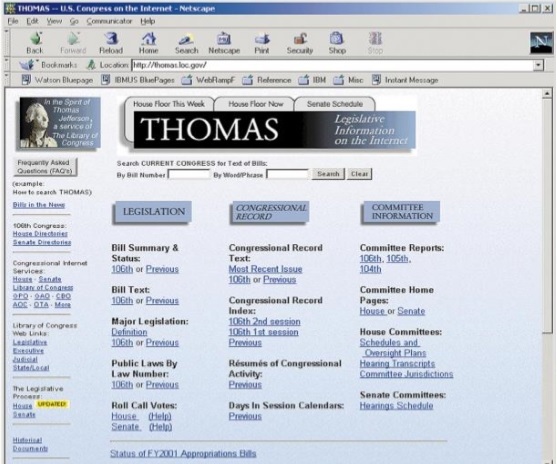
And, here is the screenshot of the same webpage after it was hacked −
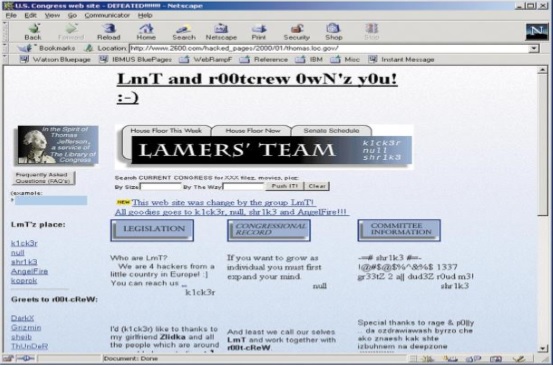
What are the Skill-Sets of Ethical Hackers?
Expert ethical hackers have the following skill-sets to hack the system ethically
They must be trustworthy.
Whatever the risks and vulnerabilities, they discover while testing the system, they have to keep them confidential.
Clients provide confidential information about their system infrastructure such as IP address, password, etc. Ethical hackers need to keep this information confidential.
Ethical hackers must have sound knowledge of computer programming, networking and hardware.
They should have good analytical skills to analyze the situation and speculate the risk in advance.
They should have the management skill along with patience, as pen testing can take one day, one week, or even more.
What do Ethical Hackers do?
Ethical hackers, while performing penetration testing, basically try to find the answers to the following questions −
- What are the weak points that a criminal hacker can hit?
- What can a criminal hacker see on the target systems?
- What can a criminal hacker do with that confidential information?
Moreover, an ethical hacker is required to address adequately the vulnerabilities and risks, which he found to exist in the target system(s). He needs to explain and suggest the avoidance procedures. Finally, prepare a final report of his all ethical activities that he did and observed while performing penetration testing.
Types of Hackers
Hackers are normally divided into three categories.
Black Hat Hackers
A "black hat hacker" is an individual who has an extensive computer software as well as hardware and his purpose is to breach or bypass internet security of someone else. Black hat hackers are also popular as crackers or dark-side hackers.
White Hat Hackers
The term "white hat hacker" refers to an ethical computer hacker who is a computer security expert, specialized in penetration testing and in other associated testing methodologies. His primary role is to ensure the security of an organization's information system.

Grey Hat Hacker
The term "grey hat hacker" refers to a computer hacker who cracks computer security system whose ethical standards fall somewhere between purely ethical and solely malicious.