Malware Removal - Preparation for Removal
Malwares attach themselves to programs and transmit to other programs by making use of some events. They need these events to happen because they cannot start by themselves, transmit themselves by using non-executable files and infect other networks or a computer.
To prepare for the removal phase, we should first understand which all computer processes are being used by the malware in order to kill them. Which traffic ports are being used by them in order to block them? What are the files related to these malwares, so we can have the chance to repair them or delete. All this includes a bunch of tools that will help us to gather this information.
Investigation Process
From the above-mentioned conclusions, we should know that when some unusual processes or services run by themselves, we should investigate further their relations with a possible virus. The investigation process is as follows −
To investigate the processes, we should start by using the following tools −
- fport.exe
- pslist.exe
- handle.exe
- netstat.exe
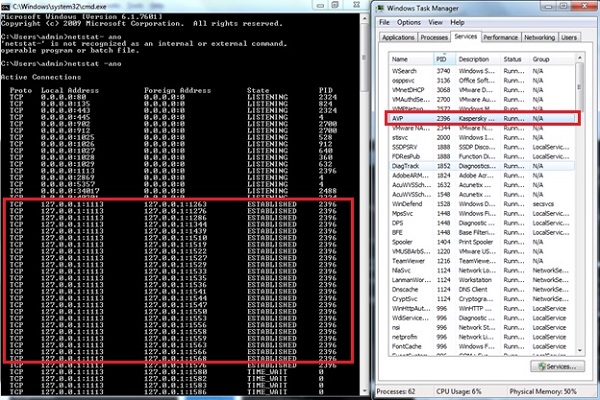
The Listdll.exe shows all the dll files that are being used. The netstat.exe with its variables shows all the processes being run with their respective ports. The following example shows, how a process of Kaspersky Antivirus is mapped to a command netstat-ano to see the process numbers. To check which process number it belongs to, we will use the task manager.
For Listdll.exe, we have download it from the following link https://technet.microsoft.com/en-us/sysinternals/bb896656.aspx and we can run it to check which processes are connected with the DLL that are being used.
We open CMD and go to the path of Listdll.exe as shown in the following screenshot, then run it.
We will get the result as shown in the following screenshot.
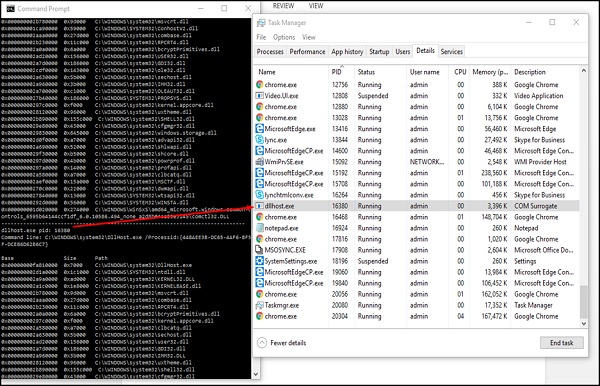
For example, PID 16320 is being used by the dllhost.exe, which has a description COM Surrogate and on the left. It has shown all the DLL being shown by this process, which we can google and check.
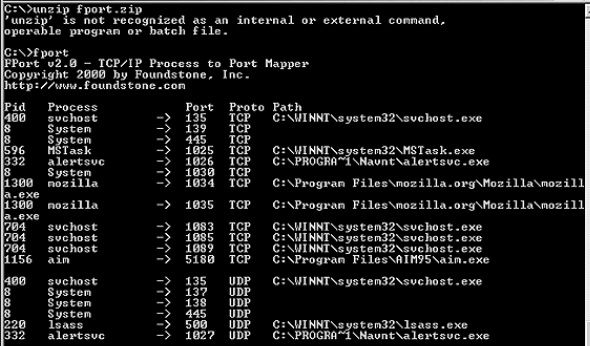
Now we will use the Fport, which can be downloaded from the following link https://www.mcafee.com/hk/downloads/free-tools/fport.aspx# to map the services and PID with the ports.
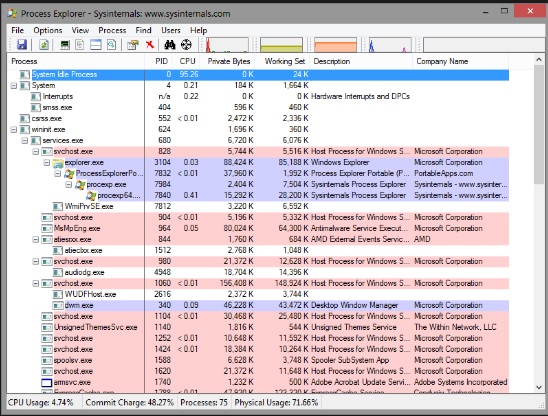
Another tool to monitor the services and to see how many resources they are consuming is called as the Process Explorer, which can be downloaded from the following link https://download.sysinternals.com/files/ProcessExplorer.zip and after downloading it, you have to run the exe file and you will see the following result −