
 Data Structure
Data Structure Networking
Networking RDBMS
RDBMS Operating System
Operating System Java
Java MS Excel
MS Excel iOS
iOS HTML
HTML CSS
CSS Android
Android Python
Python C Programming
C Programming C++
C++ C#
C# MongoDB
MongoDB MySQL
MySQL Javascript
Javascript PHP
PHP
- Selected Reading
- UPSC IAS Exams Notes
- Developer's Best Practices
- Questions and Answers
- Effective Resume Writing
- HR Interview Questions
- Computer Glossary
- Who is Who
How to Secure ZOOM application
This article poses a common advisory and security measure note for the Zoom users to protect themself from presumptive hacking attempt, as this application is quite vulnerable to breach. Zoom is quite trending and its popularity mysteriously skyrocket in last 3 month in terms of downloads (20 CR) despite having other plethora of amazing video conferencing application. Zoom does not have the End-to-end encryption facility like whatsapp and WebEx and attackers can potentially gain control to the ZOOM without its user’s cognizance by mean of a secret tools called zWarDial.
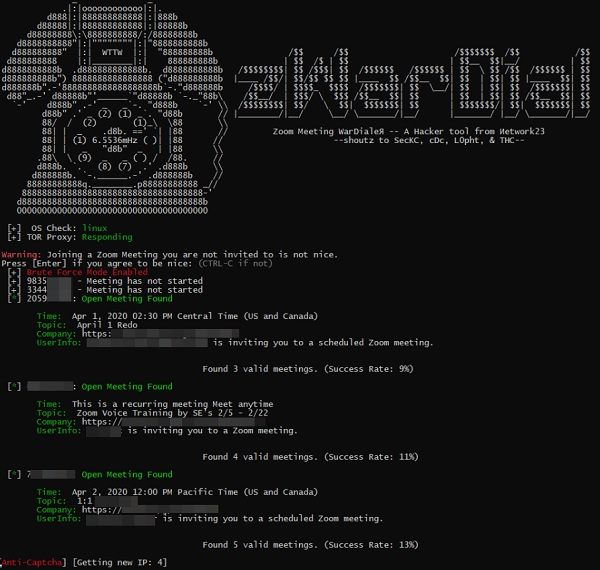
However, I am not going to discuss the usage of this tool here as the scope of this article is beyond the jurisdiction of that idea. By wielding this tool, a hacker can do the following unsolicited activities;
- Hackers can easily brute-force the meeting ID
- Can access your web camera as well as, view the existing other users ZOOM recordings
- He can send a malicious link in an e-mail that usually leads to malware that can take control of your computer (UNC bug).
- He can disrupt the current meeting by zoom-bombing
Protection Measures
-
Restrict outgoing NTLM traffic
Go to Computer Configuration-> windows settings->Security Settings->Network security -> Deny all.
-
Use a Password
You can enable the password feature in Zoom that protects those meetings with a password, and only share it with the people you want in your meeting.
-
Join before host
That way, you'll know that no one can start your meetings without you--including a hacker or "Zoombomber". To do this, make sure the "Join before host" setting is off (it's off by default). It's best to turn this off to protect your meetings.
-
Disable Guest Screen Sharing
By restricting screen sharing to the host, you can prevent anyone else from being able to display what is on their desktop. It won't stop anyone from joining your meeting, but it will at least keep them from taking over the meeting and sharing inappropriate material.
-
Keep Your Personal Meeting ID Private
Don't share your personal meeting ID (PMI) online. If you do, it's relatively easy for anyone to find it and join any meeting you're hosting. Instead, use a unique meeting ID for each separate meeting.
-
Use the Waiting Room
Another option is to enable to waiting room feature, which places every guest in a virtual waiting room before the meeting starts. When you're ready, you'll then have to manually admit your guests. This gives you control over who can attend and makes it easier to keep unwanted guests out.
-
Protect your Home Wi-Fi
A strong password helps to stop potential hackers from intercepting any data sent or received by your machine. Make your password a strong one, using a complex pattern of letters, numbers and symbols, and change it often to stay one step ahead.
-
Unplug camera’s or mice
The best way to combat with hackers is to just switch off your camera, speakers, and mice after ending the Zoom session.
-
Educate yourself on Scams
Attacks like phishing or social engineering (to compel you to open a malicious link) can be cleverly disguised to look like a communication. Be vigilant of emails/links that ask you for your personal information or data to be sent somewhere outside of your office usual repository.

