
- Ethical Hacking - Home
- Ethical Hacking - Overview
- Ethical Hacking - Hacker Types
- Ethical Hacking - Famous Hackers
- Ethical Hacking - Terminologies
- Ethical Hacking - Tools
- Ethical Hacking - Skills
- Ethical Hacking - Process
- Ethical Hacking - Reconnaissance
- Ethical Hacking - Footprinting
- Ethical Hacking - Fingerprinting
- Ethical Hacking - Sniffing
- Ethical Hacking - Sniffing Tools
- Ethical Hacking - ARP Poisoning
- Ethical Hacking - DNS Poisoning
- Ethical Hacking - Exploitation
- Ethical Hacking - Enumeration
- Ethical Hacking - Metasploit
- Ethical Hacking - Trojan Attacks
- Ethical Hacking - TCP/IP Hijacking
- Ethical Hacking - Email Hijacking
- Ethical Hacking - Password Hacking
- Ethical Hacking - Wireless Hacking
- Ethical Hacking - Social Engineering
- Ethical Hacking - DDOS Attacks
- Ethical Hacking - Cross Site Scripting
- Ethical Hacking - SQL Injection
- Ethical Hacking - Pen Testing
Ethical Hacking - Overview
Hacking has been a part of computing for almost 55 years and it is a very broad discipline, which covers a wide range of topics. The first hacking had happened in 1960 at MIT and at the same time the term "Hacker" was originated.
Hacking is the act of finding the possible entry points that exist in a computer system or computer network and finally entering into them. Hacking is usually done to gain unauthorized access on the computer system or computer network either to harm the systems or to steal some important information available on the computer.
Hacking is usually illegal until its being done to find weaknesses in a computer or network system for testing purpose, which is called Ethical Hacking.
A computer expert who does the act of hacking is called a "Hacker". Hackers are those who seek knowledge, to understand how systems operate, how they are designed, and then attempt to play with these systems.
Hacking Examples
Below are very well known hacking examples:
Website Hacking: This means taking unauthorized control over a web server and associated softwares like database, and other interfaces.
Network Hacking: This means gathering information about a network by using tools like Telnet, NS look up, Ping, Tracert, Netstat, etc... over the network and finally harming the network system to hamper the operation.
Email Hacking: This includes getting unauthorized access on an Email account and getting to know about various communication.
Ethical Hacking: Ethical hacking means to find weaknesses in a computer or network system for testing purpose and finally getting them fixed.
Password Hacking: This is the process of recovering secret passwords from data that has been stored in or transmitted by a computer system.
Computer Hacking: This is the process of stealing computer ID and password by applying hacking ways and getting unauthorized access on complete computer system.
Advantages of Hacking
Recover lost information specially incase you lost your password.
Performing penetration testing to strengthen computer and network security.
Putting adequate preventative measures in place to prevent security breaches.
Finally to have a computer system that prevents malicious hackers from gaining access.
Prevent national security breach.
Disadvantages of Hacking
Massive security breach.
Unauthorized system access on private information.
Privacy violation.
Hampering system operation.
Denial of service attacks
Malicious attack on the system.
National security breach.
Purpose of Hacking
There could be various positive and negative intentions behind performing hacking activities. Few are below:
Just for fun
Show off
Egoistic Nature
Steal important information.
Damaging the system.
Hampering Privacy.
Money extortion
System Security Testing
Policy Compliance
Ethical Hacking - Hacker Types
Hackers can be categorized into white hat, black hat and grey hat categories based on their intent of hacking the system. These different terms come from old spaghetti westerns, where the bad guy wears a black cowboy hat, and the good guy wears a white hat.
White Hat Hackers
These are usually good hackers and also called Ethical Hackers. They never intent to harm the system rather they try to find out weaknesses in a computer or network system as a part of penetration testing and vulnerability assessments.
Ethical hacking is not illegal and it is one of the demanding job available in IT and various IT and non-IT companies hire ethical hackers for penetration testing and vulnerability assessments.
Back Hat Hackers
These are usually bad hackers and also called crackers. They always to gain unauthorized access on the systems to harm them in a way they can do and finally hampering the computing operation. Black Hat hacking is always illegal because of its bad intent which includes to steal corporate data, violate privacy, damage the system, stop network communication etc.
Grey Hat Hackers
Grey hat hackers are a blend of both black hat and white hat activities. They act without malicious intent but for their fun they exploit a security weakness in a computer system or network without the owners permission or knowledge. Their intent is to bring the weakness to the attention of the owners and getting appreciation or a little bounty from the owners.
Apart from the above well known classes of hackers, following are few more important terms related to Hacking:
Miscellaneous Hackers
Red Hat Hackers
Red hat hackers are again a blend of both black hat and white hat activities and they are usually on the level of hacking government agencies, top secrete information hubs and generally that falls underneath the category of sensitive information.
Blue Hat Hackers
A blue hat hacker is someone outside computer security consulting firms who is used to bug test a system prior to its launch, looking for exploits so they can be closed. Microsoft also uses the term BlueHat to represent a series of security briefing events.
Elite hacker
This is a social status among hackers, which is used to describe the most skilled. Newly discovered exploits will circulate among these hackers.
Script kiddie
A script kiddie is a non-expert who breaks into computer systems by using pre-packaged automated tools written by others, usually with little understanding of the underlying concepthence the term script.
Neophyte
A neophyte, "n00b", or "newbie" or "Green Hat Hacker" is someone who is new to hacking or phreaking and has almost no knowledge or experience of the workings of technology, and hacking.
Hacktivist
A hacktivist is a hacker who utilizes technology to announce a social, ideological, religious, or political message. In general, most hacktivism involves website defacement or denial-of-service attacks.
Ethical Hacking - Famous Hackers
We are listing down few of the most famous Hackers of the world:
Jonathan James
Ian Murphy
Kevin Mitnick
Mark Abene
Johan Helsinguis
Linus Torvalds
Robert Morris
Gary McKinnon
Kevin Poulsen
Ethical Hacking - Terminologies
Following is a list of important terms used in the field of hacking.
Adware: Adware is software designed to force pre-chosen ads to display on your system.
Attack: An attack is an action that is done on the system to have access on the system.
Back door: A back door, or trap door, is a hidden entry to a computing device or software that bypasses security measures, such as logins and password protections.
Bot: A program that automates an action so that it can be done repeatedly at a much higher rate for a more sustained period than a human operator could do it. For example sending HTTP, FTP or Telnet at a higher rate or calling script to create objects at higher rate.
Botnet: A botnet also known as zombie army is a group of computers controlled without their owners knowledge and used to send spam or make denial of service attacks.
Brute force attack: A brute force attack is an automated and the simplest kind of method to gain access to a system or website. It tries different combination of usernames and passwords, over and over again, until it gets in.
Buffer Overflow: Buffer Overflow is a flaw that occurs when more data is written to a block of memory, or buffer, than the buffer is allocated to hold.
Clone phishing: Clone phishing is the modification of an existing, legitimate email with a false link to trick the recipient into providing personal information.
Cracker: Then one who modifies the software to access the features which are considered undesirable by the person cracking the software, especially copy protection features.
Denial of service attack (DoS): A denial of service (DoS) attack is a malicious attempt to make a server or a network resource unavailable to users, usually by temporarily interrupting or suspending the services of a host connected to the Internet.
DDoS: Distributed denial of service attack (DDoS).
Exploit Kit: An exploit kit is software system designed to run on web servers, with the purpose of identifying software vulnerabilities in client machines communicating with it and exploiting discovered vulnerabilities to upload and execute malicious code on the client.
Exploit: Exploit is a piece of software, a chunk of data, or a sequence of commands that takes advantage of a bug or vulnerability to compromise the security of the computer or network system.
Firewall: A firewall is a filter designed to keep unwanted intruders outside a computer system or network while allowing safe communication between systems and users on the inside of the firewall.
Keystroke logging: Keystroke logging is the tracking of which keys are pressed on a computer (and which touchscreen points are used). It is, simply, the map of a computer/human interface. It is used by gray and black hat hackers to record login IDs and passwords. Keyloggers are usually secreted onto a device using a Trojan delivered by a phishing email.
Logic bomb: A virus secreted into a system that triggers a malicious action when certain conditions are met. The most common version is the time bomb.
Malware: Malware is an umbrella term used to refer to a variety of forms of hostile or intrusive software, including computer viruses, worms, trojan horses, ransomware, spyware, adware, scareware, and other malicious programs.
Master Program: A master program is the program a black hat hacker uses to remotely transmit commands to infected zombie drones, normally to carry out Denial of Service attacks or spam attacks.
Phishing: Phishing is an e-mail fraud method in which the perpetrator sends out legitimate-looking email in an attempt to gather personal and financial information from recipients.
Phreaker: Phreaker are considered the original computer hackers and they are someone who break into the telephone network illegally, typically to make free long-distance phone calls or to tap phone lines.
Rootkit: Rootkit is a stealthy type of software, typically malicious, designed to hide the existence of certain processes or programs from normal methods of detection and enable continued privileged access to a computer.
Shrink Wrap code : Shrink Wrap code attack is just the act of exploiting holes in unpatched or poorly configured software.
Social engineering: Social engineering means to deceive someone for the purpose of acquiring sensitive and personal information, like credit card details or user names and passwords.
Spam: Spam is simply unsolicited email, also known as junk email sent to a large number of recipients without their consent.
Spoofing: A technique used to gain unauthorized access to computers, whereby the intruder sends messages to a computer with an IP address indicating that the message is coming from a trusted host.
Spyware: Spyware is software that aims to gather information about a person or organization without their knowledge and that may send such information to another entity without the consumer's consent, or that asserts control over a computer without the consumer's knowledge.
SQL Injection: SQL injection is an SQL code injection technique, used to attack data-driven applications, in which malicious SQL statements are inserted into an entry field for execution (e.g. to dump the database contents to the attacker).
Threat: A threat is a possible danger that can exploit an existing bug or vulnerability to compromise the security of the computer or network system.
Trojan: A Trojan, or Trojan Horse, is a malicious program disguised to look like a valid program, making it difficult to distinguish from programs that are supposed to be there designed with an intention to destroy files, alter information, steal passwords or other information.
Virus: A virus is a malicious program or a piece of code which is capable of copying itself and typically has a detrimental effect, such as corrupting the system or destroying data.
Vulnerability: A vulnerability is a weakness which allows an hacker to compromise the security of the computer or network system.
Worms: A worm is a self-replicating virus that does not alter files but resides in active memory and duplicates itself.
Cross-site Scripting : Cross-site scripting (XSS) is a type of computer security vulnerability typically found in web applications. XSS enables attackers to inject client-side script into web pages viewed by other users.
Zombie Drone: A Zombie Drone is defined as a hi-jacked computer that is being used anonymously as a soldier or 'drone' for malicious activity like to distribute unwanted spam e-mails.
Ethical Hacking - Tools
We are listing down few of the most famous tools to be used for hacking (or preventing ) the system:
NMAP
Metaspoit
Burp Suit
Angry IP Scanner
Cain & Abel
Ettercap
EtherPeek
SuperScan
QualysGuard
WebInspect
LC4 (formerly called L0phtcrack)
LANguard Network Security Scanner
Network Stumbler
ToneLoc
Ethical Hacking - Skills
As an ethical hacker you will need to understand various hacking techniques like:
Password guessing and cracking
Session Hijacking
Session Spoofing
Network traffic Sniffing
Network traffic Sniffing
Denial of Service attacks
Exploiting buffer overflow vulnerabilities
SQL injection
Basic Skills
Computer Hacking is a Science as well as an Art and like any other expertise you need to put lof effort you gain required knowledge. Once you are on the track then you need more effort to keep you up-to-date with latest technologies, new vulnerabilities and exploitation techniques.
An ethical hacker typically must be computer systems experts and needs to have very strong programming and computer networking skills.
An ethical hacker needs to have lot of patience, persistence, and perseverance to try again and again and wait for the required result.
Additionally ethical hacker should be smart enough to understand the situation and opponent's mind for social engineering, manipulative, good problem-solving and communications skills.
Courses & Certifications
This tutorial gives you basic guidelines to become a successful Ethical Hacker:
Obtain a bachelor degree in Computer Science or A+ Certificate to have understanding of the most common hardware and software technologies.
Get a programmar role for few years and then switch to get a tech support position.
Proceed to get network certifications like Network+ or CCNA and then security certifications like Security+, CISSP, or TICSA.
It is recommended to work for sometime like a Network Engineer and System administrator to understand network and system in and out.
Keep going through various books, tutorials and papers to understand various computer security aspects and take them as challenge to secure your network, computer systems as network security engineer.
Study courses which cover creating Trojan horses, backdoors, viruses, and worms, denial of service (DoS) attacks, SQL injection, buffer overflow, session hijacking, and system hacking.
Get mastering in penetration testing, footprinting and reconnaissance, and social engineering.
Finally go for a Certified Ethical Hacker (CEH) Certification.
GIAC (Global Information Assurance Certification) and Offensive Security Certified Professional (OSCP) are additional IT security certifications which will add lot of value to your profile.
Final Note
You need to stay as a White Hat Hacker which means you need to work within given boundaries which means never intrude or attack any computer or network without a required permission from the authorities.
As a final note, its highly recommended to be refrain from engaging yourself in black hat hacking which may spoil your ethical hacking career in many government-related as well as in private organisations.
Ethical Hacking - Process
Ethical Hacking - DOS Attacks
A Distributed Denial of Service (DDoS) attack is an attempt to make an online service or simply saying a website unavailable by overloading it with huge floods of traffic generated from multiple sources.
Unlike a Denial of Service (DoS) attack, in which one computer and one internet connection is used to flood targeted resource with packets, a DDoS attack uses many computers and many Internet connections, often distributed globally in what is referred to as a botnet.
A large scale volumetric DDoS attack can generate a traffic of volumes measured in tens of Gigabits (and even hundreds of Gigabits) per second. I'm sure your normal network will not be able to handle such traffic.
What are Botnets?
Attackers build a network of hacked machines which are known as botnets, by spreading malicious piece of code through emails, websites and social media. Once these computers are infected, they can be controlled remotely, without their owners' knowledge, and used like an army to launch an attack against any target.
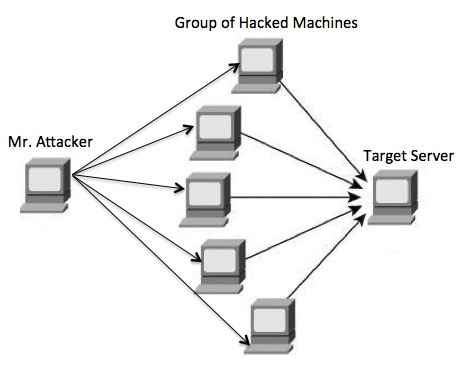
A DDoS floods can be generated in multiple ways, for example botnets can be used for sending more number of connection requests than a server can handle at a time, or having computers send the victim huge amounts of random data to use up the targets bandwidth. Due to a distributed nature of these machines, they can be used to generate distributed high traffic which may be difficult to handle and finally results in completely blockage of the service.
Types of DDOS Attacks
DDoS attacks can be broadly categorized into three category:
Volume Based Attacks
This attack includes TCP floods, UDP floods, ICMP floods, and other spoofed-packet floods. These are also called Layer 3 & 4 Attacks. Here attacker tries to saturate the bandwidth of the target site. The attack magnitude is measured in bits per second (Bps).
UDP Flood - This is used to flood random ports on a remote host with numerous UDP packets, more specifically port number 53. Specialized firewalls can be used to filter out or block malicious UDP packets.
ICMP Flood - This is similar to UDP flood and used to flood a remote host with numerous ICMP Echo Request. This type of attack can consume both outgoing and incoming bandwidth and a high volume of ping reuest will result in overall system slowdown.
HTTP Flood - The attacker sends HTTP GET and POST requests to a targeted web server in a larger volume which can not be handled by the server and leads to denial of additional connections from legitimate clients.
Amplification Attack - The attacker makes a request that generates a larger response which includes DNS requests for large TXT records and HTTP GET requests for large files like images, PDF or any other data files.
Protocol Attacks
This attack includes SYN floods, Ping of Death, fragmented packet attacks, and Smurf DDoS etc. This type of attack consumes actual server resources and other resources like firewalls and load balancers etc. The attack magnitude is measured in Packets per second.
DNS Flood - These attacks are used for attacking both the infrastructure and a DNS application to overwhelm a targets system and consume all available network bandwidth.
SYN Flood - The attacker sends TCP connection requests faster than the targeted machine can process them, causing network saturation. administrators can tweak TCP stacks to mitigate the effect of SYN floods. To reduce the effect of SYN flood you can reduce the timeout until a stack frees memory allocated to a connection, or selectively dropping incoming connections using firewall or iptables.
Ping of Death - The attacker sends malformed or oversized packets using a simple ping command. IP allows sending 65,535 bytes packets but sending a ping packet larger than 65,535 bytes violates the Internet Protocol and could cause memory overflow on the target system and finally crash the system. To avoid Ping of Deatch attacks, and its variants, many sites block ICMP ping messages altogether at their firewalls.
Application Layer Attacks
This attack includes Slowloris, Zero-day DDoS attacks, DDoS attacks that target Apache, Windows or OpenBSD vulnerabilities and more. Here the attack goal is to crash the web server. The attack magnitude is measured in Requests per second.
Application Attack - This is also called Layer 7 Attack, where attacker makes excessive log-in, database-lookup or search requests to overload the application. Its really harder to detect Layer 7 attacks because they resemble legitimate website traffic.
Slowloris - The attacker sends huge number of HTTP headers to a targeted web server, but never completes a request. The targeted server keeps each of these false connections open and eventually overflows the maximum concurrent connection pool, and leads to denial of additional connections from legitimate clients.
NTP Amplification - The attacker exploits publically-accessible Network Time Protocol (NTP) servers to overwhelm the targeted server with User Datagram Protocol (UDP) traffic.
Zero-day DDoS Attacks - A zero-day vulnerability is a system or application flaw previously unknown to the vendor, and has not been fixed or patched. These are new type of attacks coming into existence day by day, for example exploiting vulnerabilities for which no patch has yet been released.
Quick Fix
DDoS attacks have become more common than ever before, and unfortunately there is no quick fix for this but if your system is under DDoS attack then first and the most important step is not to panic and second step is to start looking into the matter step by step.
There are number of DDoS protection options which you can apply depending on the type of DDoS attack.
Your DDoS protection starts from identifying and closing all the possible OS and application level vulnerabilities in your system, closing all the possible ports, removing unnecessary access from the system and hiding your server behind a proxy or CDN system.
If you see a low magnitude of the DDoS then you can find many firewall based solutions which can help you in filtering out DDoS based traffic. But if you have high volume of DDoS attack like in giga bits or even more then you should look forward for any DDoS protection service providers that offers a more holistic, proactive and genuine approach.
You must be careful while approaching and selecting a DDoS protection service provider. There are number of service providers who want to take advantage of your bad situation and if you inform them that you are under DDoS attack then they will start offering you a variety of services at a very high prices.
I can suggest you a simple and working solution which starts with a search for a good DNS solution provider who is flexible enough to configure A and CNAME records for your website. Second you will need a good CDN provider who is capable enough to handle big DDoS traffic and provide you DDoS protection service as a part of their CDN package.
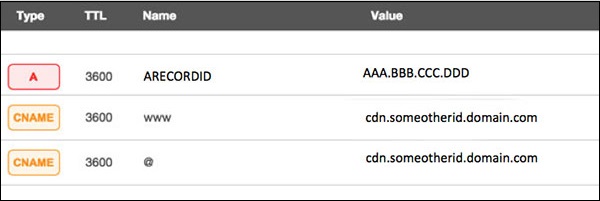
Now assume your server IP address is AAA.BBB.CCC.DDD then do the following DNS configuration.
Create a A Record in DNS zone file as shown below with a DNS identifier for example ARECORDID and keep it secret from outside world.
Now ask your CDN provider to link created DNS identifier with a URL something like cdn.someotherid.domain.com.
You will use CDN URL cdn.someotherid.domain.com to create two CNAME records first one to point to www and second record to point to @ as shown below.
You can take help from your system administrator to understand these points and configure DNS and CDN appropriately. Finally you will have following configuration at your DNS.
Now let the CDN provider handle all type of DDoS attacks and your system will remain safe. But here condition is that you should not disclose your system's IP address or A record identifier to anyone otherwise again direct attack will start.
Ethical Hacking - Footprinting
Footprint is a process of gathering possible information about the target computer system or network. This is basically the first step where hacker gathers as much information as possible to find ways to intrude into the target or at least deciding what type of attack will be more suitable for the target.
Following section discusses about the basic and easily accessible information about any computer system or network available on the internet.
Domain Name Information
You can use http://www.whois.com/whois website to get detailed information about a domain name information including its owner, registrar date, its registrar, expiry, name server, owner's contact etc.
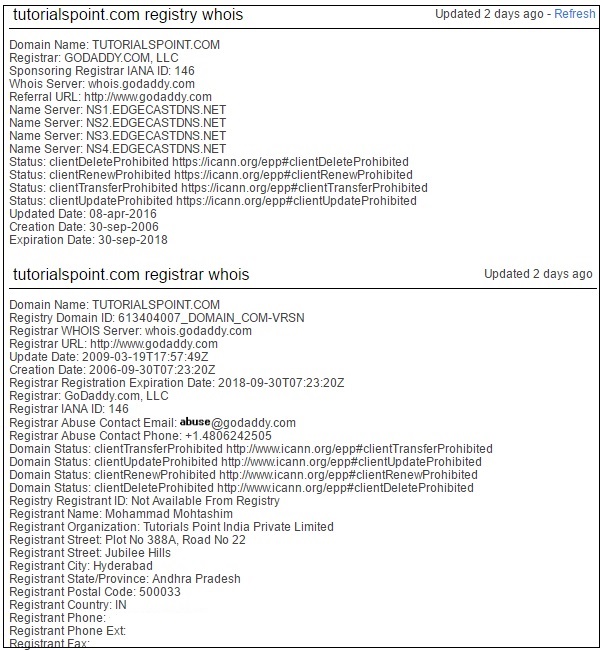
Following is a sample record about tutorialspoint.com
Quick Fix
It's always recommended to keep your domain name profile a private one which should hide above mentioned information form outside world.
Finding IP Address
You can use ping command at your prompt. This command is available on Windows as well as on Linux OS. Following is the example to find out IP address for tutorialspoint.com
$ping tutorialspoint.com
This will produce following result:
PING tutorialspoint.com (66.135.33.172) 56(84) bytes of data. 64 bytes from 66.135.33.172: icmp_seq=1 ttl=64 time=0.028 ms 64 bytes from 66.135.33.172: icmp_seq=2 ttl=64 time=0.021 ms 64 bytes from 66.135.33.172: icmp_seq=3 ttl=64 time=0.021 ms 64 bytes from 66.135.33.172: icmp_seq=4 ttl=64 time=0.021 ms
Finding Hosting Company
Once you have website address then you can get further detail by using ip2location.com website. Following is the example to find out the detail about IP adress:
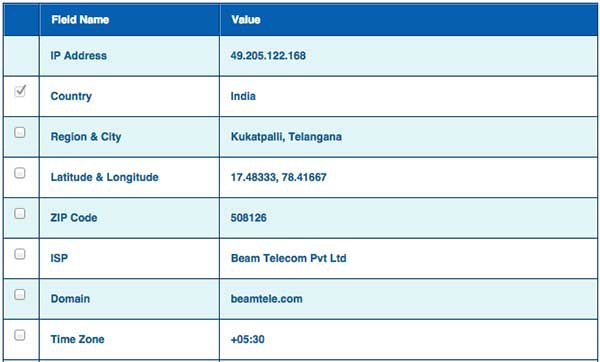
Here ISP row gives you detail about the hosting company because usually IP addresses are provided by hosting companies only.
Quick Fix
If a computer system or network is linked with the internet directly then you can not hide IP address and the related information like hosting company, its location, ISP etc. So if it's very sensitive server then its recommended to keep it behind a secure proxy so that hacker can not get detail about actual server and it will be difficult to reach to the server directly.
Another effective way of hiding your system IP and ultimately all the associated information is to go through a Virtual Private Network (VPN). If you configures a VPN then the whole traffic routes through the VPN network, so your true IP address assigned by your ISP is always hidden. You can find many good VPN service providers available.
IP Address Ranges
Small sites may have a single IP address associated with them but larger websites usually will have multiple IP addresses serving different domains and sub-domains.
You can obtain a range of IP addresses assigned to a particular company using American Registry for Internet Numbers (ARIN).
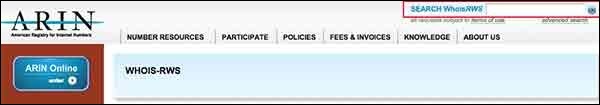
You can enter company name in the highlighted search box to find out the list of all the assigned IP addresses to that company.
History of the Website
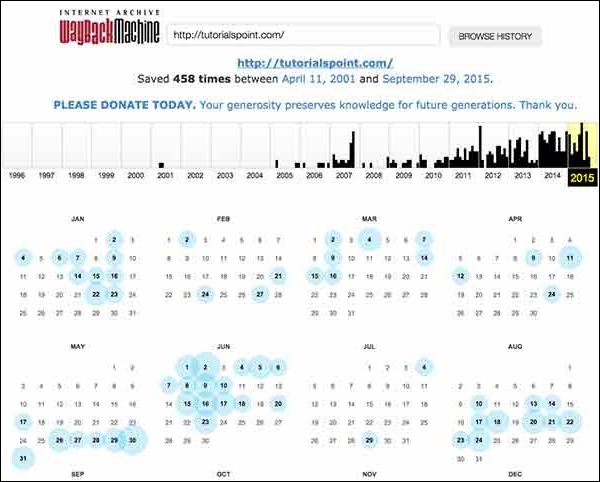
Its very easy to get complete history of the website using www.archive.org.

You can enter domain name in the search box to find out how a website was looking at a given point of time and what was the pages available on the website on different dates.
Quick Fix
Though it has some advantages of keeping your website in archive database but if you do not like any body to see how your website progressed through different stages then you can request archive.org to delete the history of your website.
Ethical Hacking - Fingerprinting
The term OS fingerprinting in Ethical Hacking refers to any method used to determine what operating system is running on a remote computer. This could be:
Active Fingerprinting - This is accomplished by sending specially crafted packets to the target machine and response is noted and analyzed to determine the target OS. We have discussed one example below using nmap tool to detect an OS of the target domain.
Passive Fingerprinting - Passive fingerprinting is based on sniffer traces from the remote system. Based on the sniffer traces (such as Wireshark) of the packets, you can determine the operating system of the remote host.
There are following four important elements that we will look at to determine the operating system:
- TTL - What the operating system sets the Time To Live on the outbound packet.
- Window Size - What the operating system sets the Window Size at.
- DF - Does the operating system set the Don't Fragment bit.
- TOS - Does the operating system set the Type of Service, and if so, at what.
By analyzing these factors of a packet, you may be able to determine the remote operating system. This system is not 100% accurate, and works better for some operating systems then others.
Basic Steps
Before attacking a system its always required to know what operating system is hosting a website. Once a target OS is known then it becomes easy to determine which vulnerabilities might be present to exploit the target system.
Below is a simple nmap command which can be used to identify operating system serving and all the opened ports associated with a domain name ie IP address
$nmap -O -v tutorialspoint.com
This will produce following sensitive information about the given domain name or IP address:
Starting Nmap 5.51 ( http://nmap.org ) at 2015-10-04 09:57 CDT Initiating Parallel DNS resolution of 1 host. at 09:57 Completed Parallel DNS resolution of 1 host. at 09:57, 0.00s elapsed Initiating SYN Stealth Scan at 09:57 Scanning tutorialspoint.com (66.135.33.172) [1000 ports] Discovered open port 22/tcp on 66.135.33.172 Discovered open port 3306/tcp on 66.135.33.172 Discovered open port 80/tcp on 66.135.33.172 Discovered open port 443/tcp on 66.135.33.172 Completed SYN Stealth Scan at 09:57, 0.04s elapsed (1000 total ports) Initiating OS detection (try #1) against tutorialspoint.com (66.135.33.172) Retrying OS detection (try #2) against tutorialspoint.com (66.135.33.172) Retrying OS detection (try #3) against tutorialspoint.com (66.135.33.172) Retrying OS detection (try #4) against tutorialspoint.com (66.135.33.172) Retrying OS detection (try #5) against tutorialspoint.com (66.135.33.172) Nmap scan report for tutorialspoint.com (66.135.33.172) Host is up (0.000038s latency). Not shown: 996 closed ports PORT STATE SERVICE 22/tcp open ssh 80/tcp open http 443/tcp open https 3306/tcp open mysql TCP/IP fingerprint: OS:SCAN(V=5.51%D=10/4%OT=22%CT=1%CU=40379%PV=N%DS=0%DC=L%G=Y%TM=56113E6D%P= OS:x86_64-redhat-linux-gnu)SEQ(SP=106%GCD=1%ISR=109%TI=Z%CI=Z%II=I%TS=A)OPS OS:(O1=MFFD7ST11NW7%O2=MFFD7ST11NW7%O3=MFFD7NNT11NW7%O4=MFFD7ST11NW7%O5=MFF OS:D7ST11NW7%O6=MFFD7ST11)WIN(W1=FFCB%W2=FFCB%W3=FFCB%W4=FFCB%W5=FFCB%W6=FF OS:CB)ECN(R=Y%DF=Y%T=40%W=FFD7%O=MFFD7NNSNW7%CC=Y%Q=)T1(R=Y%DF=Y%T=40%S=O%A OS:=S+%F=AS%RD=0%Q=)T2(R=N)T3(R=N)T4(R=Y%DF=Y%T=40%W=0%S=A%A=Z%F=R%O=%RD=0% OS:Q=)T5(R=Y%DF=Y%T=40%W=0%S=Z%A=S+%F=AR%O=%RD=0%Q=)T6(R=Y%DF=Y%T=40%W=0%S= OS:A%A=Z%F=R%O=%RD=0%Q=)T7(R=Y%DF=Y%T=40%W=0%S=Z%A=S+%F=AR%O=%RD=0%Q=)U1(R= OS:Y%DF=N%T=40%IPL=164%UN=0%RIPL=G%RID=G%RIPCK=G%RUCK=G%RUD=G)IE(R=Y%DFI=N% OS:T=40%CD=S)
If you do not have nmap command installed on your Linux system then you can install it using following yum command:
$yum install nmap
You can go through namp command in detail to check and know different features associated with the system and to secure against malicious attacks.
Quick Fix
You can hide your main system behind a secure proxy server or a VPN so that your complete identity is safe and ultimately your main system is safe.
Port Scanning
We have just seen information given by nmap command. This command lists down all the open ports on a given server.
PORT STATE SERVICE 22/tcp open ssh 80/tcp open http 443/tcp open https 3306/tcp open mysql
You can also check if a particular port is opened or not using the following command:
$nmap -sT -p 443 tutorialspoint.com
This will produce a result something as follows:
Starting Nmap 5.51 ( http://nmap.org ) at 2015-10-04 10:19 CDT Nmap scan report for tutorialspoint.com (66.135.33.172) Host is up (0.000067s latency). PORT STATE SERVICE 443/tcp open https Nmap done: 1 IP address (1 host up) scanned in 0.04 seconds
Once a hacker knows about open ports, then he can plan different attack techniques through the open ports.
Quick Fix
It is always recommended to check and close all the unwanted ports to safeguard the system from malicious attacks.
Ping Sweep
A ping sweep is a network scanning technique which is used to determine which of a range of IP addresses map to live hosts. Ping sweep also known as ICMP sweep.
You can use fping command for ping sweep. This command is a ping like program which uses the Internet Control Message Protocol (ICMP) echo request to determine if a host is up. fping is different from ping in that you can specify any number of hosts on the command line, or specify a file containing the lists of hosts to ping. If a host does not respond within a certain time limit and/or retry limit it will be considered unreachable.
Quick Fix
To disable ping sweeps on a network, you can block ICMP ECHO requests from outside sources. This can be done using the following command which will create a firewall rule in iptable.
$iptables -A OUTPUT -p icmp --icmp-type echo-request -j DROP
DNS Enumeration
Domain Name Server (DNS) is like a map or an address book, infact a distributed database which is used to translate an IP address 192.111.1.120 to a name www.example.com and vice versa.
DNS enumeration is the process of locating all the DNS servers and their corresponding records for an organization. The idea is to gather as much interesting details as possible about your target before starting the attack.
Though you can use nslookup command available on Linux to get DNS and host related information but you can use following DNSenum script to get detailed information about a domain:
DNSenum.pl
DNSenum script can perform various important operation:
Get the host's addresses
Get the nameservers
Get the MX record
Perform axfr queries on nameservers
Get extra names and subdomains via google scraping
Brute force subdomains from file can also perform recursion on subdomain that has NS records
Calculate C class domain network ranges and perform whois queries on them
Perform reverse lookups on netranges
Quick Fix
DNS Enumeration does not have a quick fix and its really beyond the scope of this tutorial. DNS and DNS Enumerations in itself are big topics to discuss and preventing DNS Enumeration is a big challenge.
If DNS is configured insecurely, it is possible that lots of sensitive information about the network and organization can go outside and an untrusted Internet user can perform a DNS zone transfer.
Ethical Hacking - Network Reconnaissance
Ethical Hacking - Social Engineering
Many times a company documents are thrown into dustbin and sensitive information such as Names, Phone Numbers, Account Numbers, Social Security Numbers, Addresses, etc go along with these documents. Many companies still use carbon paper in its fax machine and once the roll is over, its carbon goes into dustbin which may have traces of sensitive information.
Attackers can easily retrieve information from the company dumpsters and pilfering through the garbage.
Another social engineering attack could be like attacker will come in contact of any company personnel and establish good relationship over a period of time. This relationship can be established on-line through social network, chatting rooms or offline at coffee table, playground or through any other means. Attacker will take office personnel in confidence and finally dig out the required sensitive information without giving a clue that some information is being outside of the organization.
A social engineer may pretends to be an employee or a valid user or an VIP by faking an identification card or simply by convincing employees of his position in the company. Such attacker can gain physical access to restricted areas, thus providing further opportunities for attacks.
Many times attacker may be around you and can do shoulder surfing while you are typing sensitive information like user ID and password, account PIN etc.
A phishing attack is a computer-based social engineering where attacker crafts an e-mail that appears legitimate giving exactly same look and feel as original website but in fact contains links to fake websites or to download malicious content. If you are not smart enough then you will type your user ID and password and will try to login which will result in failure and by that time attacker will have you ID and password to attach your original account.
Quick Fix
You should enforce security policy in your organization and conduct required trainings to make all the employees aware of the possible Social Engineering attacks and their consequences. Document shredding is mandatory part for any company. Make double sure that any link given in your email is coming from authentic person and its pointing to correct website otherwise you may be a victim of Phishing. Be professional and never share your ID and password with anybody else in any case.