
- Cyber Security - Home
- Cyber Security - Introduction
- Cyber Security - History
- Basics of Cyber Technology
- Cyber Security - Aims and Goals
- Types of Cyber Attacks
- Cyber Security - Keyloggers
- Cyber Security - Dark Web
- Cyber Security - Technologies
- Cyber Security - VPN
- Cyber Security - Policies
- Cyber Security - Standards
- Cyber Security - Tools
- Cyber Security - Challenges
- Cyber Security - Risk Analysis
- Cyber Security - Applications
- Cyber Security - Emerging Trends
Cyber Security - Standards
Cybersecurity Standards are general-purpose laws and regulations made for a generic section of business. All major organizations typically follow these standards in their specific way. Some firms make laws according to the standards designed for the overall workplace environment, whereas some firms update these standards according to their requirements.

It is to be noted that these are the best practices of organizations, and these firms are evaluated based on compliance with these set of rules.
What are Cybersecurity Standards?
Cybersecurity Standards are a range of guidelines and best practices that organizations tend to follow to improve their security systems and develop a robust protective network. These differ from cybersecurity policies in their nature and range of applications. While policies are meant to be used internally and apply to the people connected to the organization, standards set a benchmark for all organizations a like.
For example, a policy may uphold that the password of an employee must be updated over 90 days in a certain company, whereas a standard might suggest the change of passwords once every month across the organization to protect critical information.
Importance of Cybersecurity Standards
There is a critical need for organizations to follow cybersecurity standards which are made by reputed and trustworthy organizations. The need for these standards is depicted in the following points −
- Reduces Risk − Cybersecurity standards, when followed, reduce the chances of any loophole in the security system. These are designed in such a way that they eliminate the amount of risk associated with cyberattacks.
- Increase in Trust − Several small and medium-level companies try to increase their level of trust by following these standards. This way, more number of users are attracted to these companies in the longer run.
- Security Management − The security systems of an organization are largely improved when these standards are applied. Also, it becomes much easier to deploy new standards when the framework is already set in an organization.
- Mandatory Regulations − As the organizations continue to follow these norms, they fall in the category of firms that mandatorily comply with industry-level standards. This becomes crucial as the reputation of the firm is at stake.

Industry-Level Cybersecurity Standards
There are many cybersecurity standards created and managed by many governments as well as private bodies around the globe. Some of the most followed and trusted standards and certifications are given as follows −
- ISO Standards
- IT Act 2000
- NIST Framework
- Copyright Act
- Patent Act
- IPR
ISO Standards
The International Organization for Standardization, commonly known by its abbreviation ISO, is a global firm that develops standards related to technology and manufacturing. It is one of the most trusted certifications in the whole world, and most big-tech companies hold these standards on almost all products and services.

It develops voluntary, consensus-based standards for quality assurance and cyber safety. It has upheld many standards, some of which are given as follows −
- ISO 27001
- ISO 27002
- ISO 27017
- ISO 27018
- ISO 27701
IT Act 2000
The Information Technology Act of 2000, also known as the IT Act, is a legislative law passed in 2000, which governs the framework for cybersecurity systems and protective measures in India. It provides a very detailed set of rules and regulations to govern the use of computers, networks, the Internet, and all peripheral areas.
The major provisions defined in the IT Act are given as follows −
- Digital Signatures
- e-Governance
- Data and Network Protection
- Cybercrime legislation also includes hacking, identity theft, cyberbullying, fraud and malicious intent, cyberterrorism, and many more areas.
NIST Framework
The National Institute of Standards and Technology (NIST) is an organization that conducts and designs technological standards and guidelines. It is a non-regulatory federal agency within the U.S. Department of Commerce.
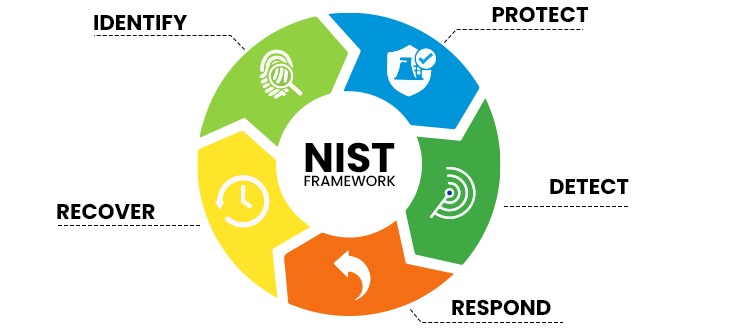
The NIST Cybersecurity Framework is a comprehensive and risk-evolved set of guidelines, which help organizations to adhere to a common set of industry-level standards. It is specifically designed to help organizations identify, examine, and manage cybersecurity risks.
The key elements of this framework include the following objectives −
- Search and Identify
- Detect and Examine
- Respond to the risk
- Recover from the incident
- Protect the organization from any future attacks
Intellectual Property Rights (IPR)
Intellectual Property Rights (IPR) are designed to protect and empower the talent of any landscape. It helps and protects innovations and creations that fall under the category of security solutions. These rights can provide a competitive edge to many individuals or organizations. Hence, these rights increase research and development of the sector and help in the overall growth of the cybersecurity ecosystem.
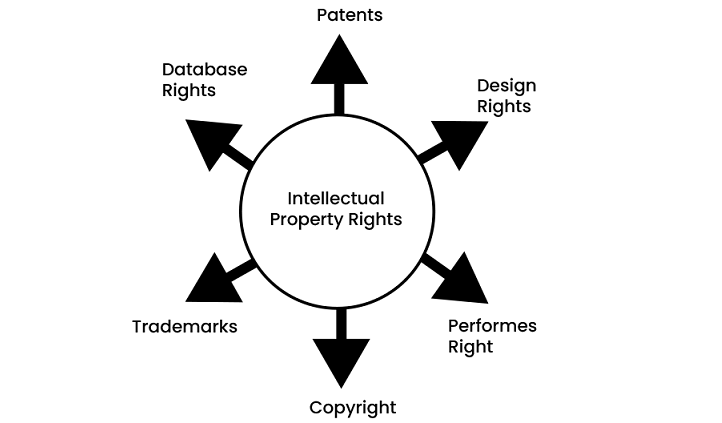
There are mainly 6 IPR categories as per legislation, and these are listed as follows −
- Patents
- Copyrights
- Trademarks
- Database Rights
- Design Rights
- Performance Rights