
- Cyber Security - Home
- Cyber Security - Introduction
- Cyber Security - History
- Basics of Cyber Technology
- Cyber Security - Aims and Goals
- Types of Cyber Attacks
- Cyber Security - Keyloggers
- Cyber Security - Dark Web
- Cyber Security - Technologies
- Cyber Security - VPN
- Cyber Security - Policies
- Cyber Security - Standards
- Cyber Security - Tools
- Cyber Security - Challenges
- Cyber Security - Risk Analysis
- Cyber Security - Applications
- Cyber Security - Emerging Trends
Cyber Security Aims and Goals
Cybersecurity deals with the protection and safeguard of networks and the corresponding data and information. It has developed from physical techniques to software methods like Antivirus and Anti-phishing platforms.
In this chapter, we will discuss the main objectives and principles of cybersecurity in detail with specific examples related to them. So, lets begin this with the objectives of cybersecurity.
Aims and Objectives of Cyber Security
Cybersecurity was developed to help in curbing the amount of cybercrimes and bullying on the internet. Some of the main objectives and aims which are delivered via the medium of cybersecurity are given as follows −
- Data Protection − To protect important data from being stolen, changed, or seen illegally, we need cybersecurity principles.
- Functioning of Systems − It is by the medium of cybersecurity that computers and networks run smoothly without interruptions.
- Identity Verification − It helps verify that people and devices are who they claim to be in the first place.
- Access Grant − In the concepts of cybersecurity, we only let people see and use information they need to do their jobs.
- Tracking Events − It helps us record everything that happens on computers and networks to find problems or catch the culprits.
- Risk Management − It helps you figure out what could go wrong, how likely it is, and how to stop it as soon as possible.
- Rules and Regulations − It demands people to obey laws and industry standards in order to protect data.
- Recovery − Cybersecurity principles help us create plans to recover from problems like cyberattacks or natural disasters.
- Generate Awareness − These guidelines help employees understand how to protect themselves and the company from cyber threats.
- Quick Response − These principles help us in making plans to deal with cyberattacks and fix problems fast.
- Organization Reputation − Cybersecurity methods help you by reducing or preventing cyberattacks, hence keeping customers and partners happy.
CIA Triad in Cybersecurity
The above-mentioned aims and objectives of Cybersecurity can be boiled down to the CIA goals. CIA is an acronym for "Confidentiality, Integrity and Availability". Some people confuse it with the American Intelligence Agency with the same name, but on the contrary, it is a security model which was formed to lay guidelines for information security within an organization or company.
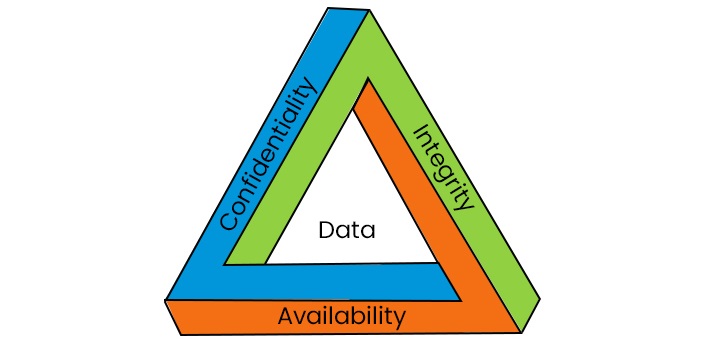
The following section will give you a detailed explanation of CIA Goals in Cybersecurity −
1. Confidentiality
Confidentiality means protecting specific information from illegal access or break-ins. This includes controlling access privilege and preventing data leakage. We can think of many threats which may include hackers, employees, and physical theft.
To counter these risks, organizations use techniques like encryption, access controls, and employee training on a large scale.
Example
Banks and insurance companies must protect their users' data from being illegally accessed during cyberattacks. Prevention methods include restricting hackers from stealing account numbers, passwords, and/or transaction history of users.
2. Integrity
We can think of integrity as a combination of data accuracy and reliability. This concept helps us prevent data modification and ensures that the information is trustworthy. The integrity of a system can be protected using methods like Hashing and Digital signatures.
Example
In a hospital, the medical data of a patient must have correct values and notations. Otherwise, the patient could end up in serious problems.
3. Availability
The term availability means that the resources are available whenever theyre required by the user or the program. Incidents like system failure, natural disasters, and cyberattacks can disrupt the availability of a system.
Methods like backup storage and critical recovery plans are important to retain access to the data in any organization.
Example
An online business must always provide access to consumers to their services. In case of a cyberattack, the retention systems should be activated to regain access to these services.
In conclusion, confidentiality, integrity, and availability are the major aspects of any cybersecurity system. These help in maintaining the dependability of any organization during a cyberattack.