
- Cryptography Tutorial
- Cryptography - Home
- Cryptography - Origin
- Cryptography - History
- Cryptography - Principles
- Cryptography - Applications
- Cryptography - Benefits & Drawbacks
- Cryptography - Modern Age
- Cryptography - Traditional Ciphers
- Cryptography - Need for Encryption
- Cryptography - Double Strength Encryption
- Cryptosystems
- Cryptosystems
- Cryptosystems - Components
- Attacks On Cryptosystem
- Cryptosystems - Rainbow table attack
- Cryptosystems - Dictionary attack
- Cryptosystems - Brute force attack
- Cryptosystems - Cryptanalysis Techniques
- Types of Cryptography
- Cryptosystems - Types
- Public Key Encryption
- Modern Symmetric Key Encryption
- Cryptography Hash functions
- Key Management
- Cryptosystems - Key Generation
- Cryptosystems - Key Storage
- Cryptosystems - Key Distribution
- Cryptosystems - Key Revocation
- Block Ciphers
- Cryptosystems - Stream Cipher
- Cryptography - Block Cipher
- Cryptography - Feistel Block Cipher
- Block Cipher Modes of Operation
- Electronic Code Book (ECB) Mode
- Cipher Block Chaining (CBC) Mode
- Cipher Feedback (CFB) Mode
- Output Feedback (OFB) Mode
- Counter (CTR) Mode
- Symmetric Algorithms
- Data Encryption Standard
- Triple DES
- Advanced Encryption Standard
- Data Integrity in Cryptography
- Data Integrity in Cryptography
- Message Authentication
- Cryptography Digital signatures
- Public Key Infrastructure
- Cryptography Useful Resources
- Cryptography - Quick Guide
- Cryptography - Discussion
Cryptography - Counter (CTR) Mode
Counter Mode (CTR) is similar to OFB, with one difference that CTR uses a counter for feedback. This method has the same advantages as OFB (patterns are destroyed and errors are not transmitted), but it also allows for parallel encryption because the feedback can be as simple as an ascending number. A simple example is that the first block is XORed with the number 1, the second with the number 2, and so on. This method allows for the simultaneous completion of any number of rounds.
It can be thought of as a counter-based version of CFB mode without the feedback. In this mode, both the sender and receiver must have access to a reliable counter that generates a new shared value each time a ciphertext block is transferred. This shared counter is not always a secret value; though, both parties must keep the counter synchronised.
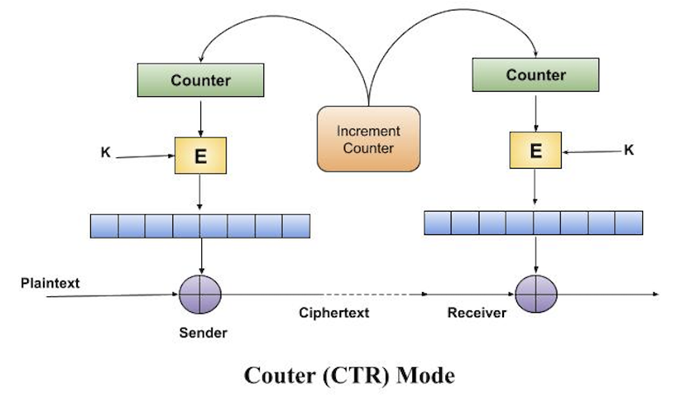
Operation
The following image shows encryption and decryption in CTR mode. Steps in operation are as follows −
Load the top register with the initial counter value that is the same for both the sender and receiver. It provides the same purpose as the IV in CFB (and CBC) mode.
Encrypt the data of the counter with the key and save the result in the bottom register.
Take the first plaintext block (P1) and XOR it with the data of the bottom register. The outcome of this is C1. Send C1 to the receiver, then update the counter. The counter update a substitutes the ciphertext feedback in the CFB mode.
Continuing in this manner until the final plaintext block is encrypted.
Decryption is an opposite process. The ciphertext block is XORed with the encrypted data of the counter value. Each ciphertext block counter is updated after decryption, exactly as it was when encrypted.
Analysis of CTR Mode
It has no message dependency, hence a ciphertext block is not dependent on preceding plaintext blocks.
Just like CFB mode, CTR mode does not include block cipher decoding. This is because the CTR mode generates a key-stream with the block cipher and then encrypts it with the XOR function. In other words, CTR mode changes a block cipher into a stream cipher.
The major disadvantage of CTR mode is that it needs the use of synchronous counters at both the transmitter and receiver. Loss of synchronisation causes insufficient plaintext recovery.
However, CTR mode offers practically all of the same advantages as CFB mode. Also, no transmission errors are propagated.
Formula for CTR Mode
CTR is similar to OFB in that it XORs a series of pad vectors with plaintext and ciphertext blocks. The primary difference is how these pad vectors are created.
In the CTR mode, we begin with a random seed, s, and then compute pad vectors using the formula −
Vi = EK(s+i-1)
where EK is the block encryption technique with key K, Vi is a pad vector, and i is the vector's offset from 1.
Once the vectors have been constructed, encryption comparable to the OFB mode can be performed using the following formula −
Ci = Vi ⊕ Bi
Decryption works in a similar way −
Bi = Vi ⊕ Ci
CTR uses the same encryption algorithm for both encryption and decryption just like CFB and OFB modes.
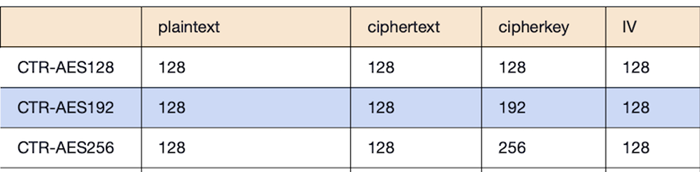
Bit-Width of CTR Mode
The Counter (CTR) mode is a typical block cipher mode of operation that uses the block cipher algorithm.In this version, we offer Advanced Encryption Standard (AES) processing; the cipherkey length for AES is 128/192/256 bits. Another constraint is that our working mode operates on units of a set size (128 bits per block), but text in the actual world has a variety of lengths. As a result, the final block of text provided to this primitive must be padded to 128 bits before it can be encrypted or decrypted.
The following table show the bit-width of the interfaces that CTR mode offer −
Advantages of CTR Mode
So below are some advantages of counter (CTR) mode −
Hardware efficiency − Unlike the three chaining modes, CTR mode allows encryption (or decryption) to be performed in parallel on many blocks of plain-text or ciphertext. For chaining modes, the algorithm has to complete the computation on one block before proceeding to the next. This limits the algorithm's maximum throughput to the reciprocal of the time required for a single execution of block encryption or decryption. In CTR mode, throughput is just limited by the amount of parallelism obtained.
Software efficiency − Additionally, while CTR mode supports parallel execution, processors with parallel capabilities like aggressive pipelining, multiple instruction dispatch per clock cycle, a high number of registers, and SIMD instructions can be properly used.
Preprocessing − The underlying encryption technique is executed regardless of whether the plaintext or ciphertext is given. As a result, considering enough memory is available and security is maintained, preprocessing can be utilised to prepare the output of the encryption boxes, which feed into the XOR functions. When the plaintext or ciphertext input is given, the only operation performed is a series of XORs. As an approach significantly increases throughput.
Random access − The ith block of plaintext or ciphertext is possible to handled using random access. With the chaining modes, block Ci cannot be computed before the i - 1 preceding block is computed. There are applications where a ciphertext is kept and just one block needs to be decrypted; in these applications, the random access functionality is useful.
Simplicity − CTR mode is simpler than ECB and CBC modes since it only requires the encryption algorithm to be implemented, not the decryption algorithm. This is especially important when the decryption algorithm differs significantly from the encryption algorithm, as is the case with AES. Also, there is no requirement to create decryption key scheduling.
Disadvantages of CTR Mode
The main drawback of the CTR is that a synchronised counter must be maintained at both the receiving and sending destinations. Losing track of this counter may result in incorrectly restoring plaintext.
To Continue Learning Please Login