
- Cryptography - Home
- Cryptography - Origin
- Cryptography - History
- Cryptography - Principles
- Cryptography - Applications
- Cryptography - Benefits & Drawbacks
- Cryptography - Modern Age
- Cryptography - Traditional Ciphers
- Cryptography - Need for Encryption
- Cryptography - Double Strength Encryption
- Cryptosystems
- Cryptosystems
- Cryptosystems - Components
- Attacks On Cryptosystem
- Cryptosystems - Rainbow table attack
- Cryptosystems - Dictionary attack
- Cryptosystems - Brute force attack
- Cryptosystems - Cryptanalysis Techniques
- Types of Cryptography
- Cryptosystems - Types
- Public Key Encryption
- Modern Symmetric Key Encryption
- Cryptography Hash functions
- Key Management
- Cryptosystems - Key Generation
- Cryptosystems - Key Storage
- Cryptosystems - Key Distribution
- Cryptosystems - Key Revocation
- Block Ciphers
- Cryptosystems - Stream Cipher
- Cryptography - Block Cipher
- Cryptography - Feistel Block Cipher
- Block Cipher Modes of Operation
- Block Cipher Modes of Operation
- Electronic Code Book (ECB) Mode
- Cipher Block Chaining (CBC) Mode
- Cipher Feedback (CFB) Mode
- Output Feedback (OFB) Mode
- Counter (CTR) Mode
- Classic Ciphers
- Cryptography - Reverse Cipher
- Cryptography - Caesar Cipher
- Cryptography - ROT13 Algorithm
- Cryptography - Transposition Cipher
- Cryptography - Encryption Transposition Cipher
- Cryptography - Decryption Transposition Cipher
- Cryptography - Multiplicative Cipher
- Cryptography - Affine Ciphers
- Cryptography - Simple Substitution Cipher
- Cryptography - Encryption of Simple Substitution Cipher
- Cryptography - Decryption of Simple Substitution Cipher
- Cryptography - Vigenere Cipher
- Cryptography - Implementing Vigenere Cipher
- Modern Ciphers
- Base64 Encoding & Decoding
- Cryptography - XOR Encryption
- Substitution techniques
- Cryptography - MonoAlphabetic Cipher
- Cryptography - Hacking Monoalphabetic Cipher
- Cryptography - Polyalphabetic Cipher
- Cryptography - Playfair Cipher
- Cryptography - Hill Cipher
- Polyalphabetic Ciphers
- Cryptography - One-Time Pad Cipher
- Implementation of One Time Pad Cipher
- Cryptography - Transposition Techniques
- Cryptography - Rail Fence Cipher
- Cryptography - Columnar Transposition
- Cryptography - Steganography
- Symmetric Algorithms
- Cryptography - Data Encryption
- Cryptography - Encryption Algorithms
- Cryptography - Data Encryption Standard
- Cryptography - Triple DES
- Cryptography - Double DES
- Advanced Encryption Standard
- Cryptography - AES Structure
- Cryptography - AES Transformation Function
- Cryptography - Substitute Bytes Transformation
- Cryptography - ShiftRows Transformation
- Cryptography - MixColumns Transformation
- Cryptography - AddRoundKey Transformation
- Cryptography - AES Key Expansion Algorithm
- Cryptography - Blowfish Algorithm
- Cryptography - SHA Algorithm
- Cryptography - RC4 Algorithm
- Cryptography - Camellia Encryption Algorithm
- Cryptography - ChaCha20 Encryption Algorithm
- Cryptography - CAST5 Encryption Algorithm
- Cryptography - SEED Encryption Algorithm
- Cryptography - SM4 Encryption Algorithm
- IDEA - International Data Encryption Algorithm
- Public Key (Asymmetric) Cryptography Algorithms
- Cryptography - RSA Algorithm
- Cryptography - RSA Encryption
- Cryptography - RSA Decryption
- Cryptography - Creating RSA Keys
- Cryptography - Hacking RSA Cipher
- Cryptography - ECDSA Algorithm
- Cryptography - DSA Algorithm
- Cryptography - Diffie-Hellman Algorithm
- Data Integrity in Cryptography
- Data Integrity in Cryptography
- Message Authentication
- Cryptography Digital signatures
- Public Key Infrastructure
- Hashing
- MD5 (Message Digest Algorithm 5)
- SHA-1 (Secure Hash Algorithm 1)
- SHA-256 (Secure Hash Algorithm 256-bit)
- SHA-512 (Secure Hash Algorithm 512-bit)
- SHA-3 (Secure Hash Algorithm 3)
- Hashing Passwords
- Bcrypt Hashing Module
- Modern Cryptography
- Quantum Cryptography
- Post-Quantum Cryptography
- Cryptographic Protocols
- Cryptography - SSL/TLS Protocol
- Cryptography - SSH Protocol
- Cryptography - IPsec Protocol
- Cryptography - PGP Protocol
- Image & File Cryptography
- Cryptography - Image
- Cryptography - File
- Steganography - Image
- File Encryption and Decryption
- Cryptography - Encryption of files
- Cryptography - Decryption of files
- Cryptography in IoT
- IoT security challenges, Threats and Attacks
- Cryptographic Techniques for IoT Security
- Communication Protocols for IoT Devices
- Commonly Used Cryptography Techniques
- Custom Building Cryptography Algorithms (Hybrid Cryptography)
- Cloud Cryptography
- Quantum Cryptography
- DNA Cryptography
- One Time Password (OTP) algorithm in Cryptography
- Difference Between
- Cryptography - MD5 vs SHA1
- Cryptography - RSA vs DSA
- Cryptography - RSA vs Diffie-Hellman
- Cryptography vs Cryptology
- Cryptography - Cryptology vs Cryptanalysis
- Cryptography - Classical vs Quantum
- Cryptography vs Steganography
- Cryptography vs Encryption
- Cryptography vs Cyber Security
- Cryptography - Stream Cipher vs Block Cipher
- Cryptography - AES vs DES ciphers
- Cryptography - Symmetric vs Asymmetric
Cryptography - Symmetric Key Encryption
Symmetric cryptography is a type of cryptography also known as secret key cryptography or private key cryptography. An encryption technique called symmetric encryption uses the same key to encrypt and decrypt data or transactions. The parties using symmetric encryption methods must securely exchange the key since it is a secret or private key.
Once the data is encrypted using a symmetric encryption algorithm, anyone without the key cannot view it because the key is private. However, the data or communication can be decrypted and converted into a form that is easily readable if the recipient have the key. Secret keys might be short, simple keys or large, random strings of characters and integers. Randomised strings can be automatically generated using software algorithms.
Before communication starts, both sides must exchange their shared secret key. Each pair of communicating entities needs a distinct shared key. The other communication parties do not have access to the key.
Symmetric cryptography has other names for the key include secret key, conventional key, session key, file encryption key, and so on. It is ideal for bulk encryption as it is much faster than asymmetric cryptography.
Below is a simple diagram which is showing symmetric cryptography process −
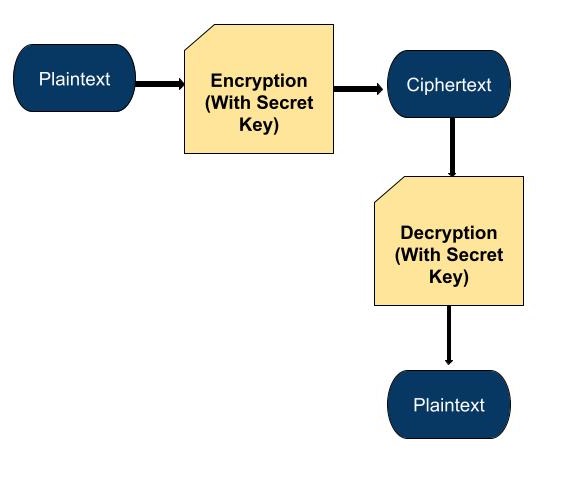
In the above diagram −
Plaintext − It represents the original message.
Encryption − This shows how to use a secret key to transform plaintext into ciphertext.
Ciphertext − It represents the encrypted message.
Decryption − This shows the process of converting the ciphertext back into plaintext using the same secret key.
Last Plaintext − It shows the original message again after decryption.
Symmetric cryptography is exactly like having a secret language between friends. Suppose you and your friend have an original way of sending communications that only you two friends know about. You both use the same secret key to encrypt and decrypt your messages. So, if anyone else tries to read your communications, they will not make sense because they do not have the secret key. It is like having a hidden language that only you and your friend can communicate in.
Principles
The following are some basic principles behind symmetric key algorithms −
Symmetric key algorithms use the same key for both encryption and decryption, allowing messages to be reversed between two parties. This means that both parties need the same private key in order to send and receive the message.
Since symmetric key algorithms do not need to use complex mathematical operations such as exponentiation, they are generally faster and more efficient than asymmetric key algorithms this makes them ideal for applications such as Internet connection security.
All asymmetric key algorithms are more secure than symmetric key algorithms. However, symmetric key algorithms are usually faster and more efficient than asymmetric key algorithms. This is because the encryption and decryption systems use the same key, so if the key is stolen, the security of the system is also compromised.
Symmetric Encryption with Authentication
With authentication, you are able to add a special mark to our message before you send it in the channel. This mark proves that the message is really from the intended person and has not been modified.
So when your friend gets the message, they can check the mark to make sure it is really from you and has not been altered or modified. So we can say it is like putting your signature on a letter to prove that it is written by you.
Symmetric Encryption without Authentication
Let us see and understand this concept with the help of an example. Let's say, you and your friend have your secret key for encrypting and decrypting messages.
But this time, you are only concerned about keeping the message secret. You do not care if someone changes the message during the transmission.
So you encrypt the message with the help of your secret key, and your friend can decrypt it using the same key. This makes sure that only you and your friend can understand the message, but there is no way to know if the message has been modified by someone else.
Advantages
As symmetric cryptography requires only one key, it can encrypt and decrypt information or data more quickly.
There is only one key needed to make this simple to use and understand.
The reason this kind of encryption is effective is that it allows for secure communication between a limited group of trusted parties.
It is more difficult for unauthorised people to read the message and more secure the longer the key is held.
Disadvantages
It can be difficult for parties to safely share the secret key with one other. So we can say key Distribution is difficult.
If the key is lost or compromised, all encrypted messages become vulnerable. So key management is a difficult task.
It is not ideal for large-scale communication in which many parties need to securely exchange messages.
This cryptography has limited security. While secure with a strong key, it is susceptible to attacks if the key is weak or poorly managed.
Applications
For many daily online activities, including banking apps and safe online browsing, symmetric encryption is important. Here are a some of the examples of these applications −
Before completing a transaction, many online banking and payment applications demand that personally identifiable information be verified. Predicting accurate information helps in stopping scams and cybercrime.
Software like BitLocker and FileVault use symmetric cryptography to encrypt files and folders.
Software like BitLocker and FileVault use symmetric cryptography to encrypt files and folders.
Symmetric encryption is used to secure the personal data that a website or organisation keeps for its visitors or the business itself. This is done to stop hackers from outside the company or unhappy staff members from within the company from tracking on sensitive data.
We can use this cryptography in messaging apps. Many messaging apps like WhatsApp and Telegram use symmetric cryptography to encrypt messages between users.
When accessing a secure website ("https" in the URL), symmetric cryptography is often used to encrypt data transferred between your browser and the website's servers.
A VPN (Virtual Private Network) uses symmetric encryption to protect data transmitted between your device and the VPN server. It protects your internet connection from hackers.
It is also used to encrypt entire disk drives which provides security for data stored on devices like laptops and smartphones.
Symmetric Cryptography Algorithms
Below are some names listed of Symmetric Cryptography algorithm −
Block Ciphers − Block Ciphers divide the unprocessed data into fixed-size data sections. The exact cipher being used determines the size. A 128-bit block cipher encrypts the blocks of 128 bits each, as compared to a single number, by splitting the plaintext into these units.
Stream Ciphers − The algorithms that encrypt basic information one byte or bit at a time are called stream ciphers. You encrypt the plaintext and generate a binary key using a bitstream generation technique.
AES (Advanced Encryption Standard) − Mainly used for securing sensitive data, like government information.
DES (Data Encryption Standard) − An older encryption method which is less secure than AES but still used in some legacy systems.
Triple DES (3DES) − It is a more secure version of DES that applies the DES algorithm three times.
Blowfish − It is a symmetric-key block cipher which is known for its fast encryption and flexibility.
Rivest Cipher 4 (RC4) − Previously it was widely used, but now considered insecure because of its vulnerabilities.
Why is Private Key Cryptography Known as Symmetric Key Cryptography?
It should be clear why it is so important to always keep the key secret because the entire architecture of symmetric cryptography depends on the one key that is used. Anyone can intercept the package and obtain the data if the sender manages to communicate the secret key together with the ciphertext. Because a significant portion of the data's integrity depends on the users' ability to keep the keys secret, this encryption type is known as private key cryptography.
You still need to decide the cipher methods to use to encrypt the data, even if you are successful in keeping the keys hidden. There are basically two types of ciphers that you can use in symmetric-key cryptography: Stream Ciphers and Block Ciphers.