Article Categories
- All Categories
-
 Data Structure
Data Structure
-
 Networking
Networking
-
 RDBMS
RDBMS
-
 Operating System
Operating System
-
 Java
Java
-
 MS Excel
MS Excel
-
 iOS
iOS
-
 HTML
HTML
-
 CSS
CSS
-
 Android
Android
-
 Python
Python
-
 C Programming
C Programming
-
 C++
C++
-
 C#
C#
-
 MongoDB
MongoDB
-
 MySQL
MySQL
-
 Javascript
Javascript
-
 PHP
PHP
What is Encapsulating Security Payload(ESP)?
Encapsulating Security Payload (ESP) provides all encryption services in IPSec based on integrity for the payload and not for the IP header, confidentiality and authentication that using encryption, without authentication is strongly discouraged because it is insecure.
Any translations in readable message format into an unreadable format are encrypted and used to hide the message content against data tampering.
IPSec provides an open framework, such as SHA and MD5 for implementing industry standard algorithms.
Encryption/decryption allows only the sender and the authorised receiver to make the data to be received in readable form and only after the integrity verification process is complete, the data payload in the packet is decrypted.
IPSec uses a unique identifier for each packet, which is a data equivalent of a fingerprint and checks for packets that are authorised or not. It doesn't sign the entire packet unless it is being tunnelled—ordinarily, for this IP data payload is protected, not the IP header. In Tunnel Mode, where the entire original IP packet is encapsulated with a new packet header added.
ESP in transport mode does not provide integrity and authentication for the entire IP packet.
ESP Format
The ESP format is diagrammatically represented as follows −
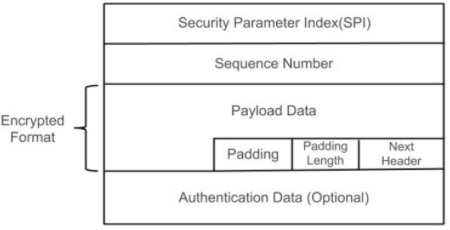
Explanation
Security Parameters Index (32 bits) − Identifies a security association. This field is mandatory. The value of zero is reserved for local, implementation- specific use and MUST NOT be sent on the wire.
Sequence Number (32 bits) − A monotonically increasing counter value; this provides an anti-replay function, as discussed for AH. The first packet sent using a given SA will have a Sequence number of 1.
Payload Data (variable) − This is a transport-level segment (transport mode) or IP packet (tunnel mode) that is protected by encryption. The type of content that was protected is indicated by the Next Header field.
Padding (0-255 bytes) − Padding for encryption, to extend the payload data to a size that fits the encryption's cipher block size, and to align the next field.
Pad Length (8 bits) − Indicates the number of pad bytes immediately preceding this field.
Next Header (8 bits) − Identifies the type of data contained in the payload data field by identifying the first header in that payload.
Authentication Data (variable) − A variable-length field (must be an integral number of 32-bit words) that contains the Integrity. Check Value computed over the ESP packet minus the Authentication Data field. This field is optional and is included only if the authentication service has been selected for the SA in question.


