
 Data Structure
Data Structure Networking
Networking RDBMS
RDBMS Operating System
Operating System Java
Java MS Excel
MS Excel iOS
iOS HTML
HTML CSS
CSS Android
Android Python
Python C Programming
C Programming C++
C++ C#
C# MongoDB
MongoDB MySQL
MySQL Javascript
Javascript PHP
PHP
- Selected Reading
- UPSC IAS Exams Notes
- Developer's Best Practices
- Questions and Answers
- Effective Resume Writing
- HR Interview Questions
- Computer Glossary
- Who is Who
What are the different components and architectures of firewalls?
Firewall in general is defined as a wall between personal computer and outside world. So it will filter the traffic coming from the outside world based on the user configuration like which sites are trusted sites and which we need to allow.
Example of firewall system design is shown below −
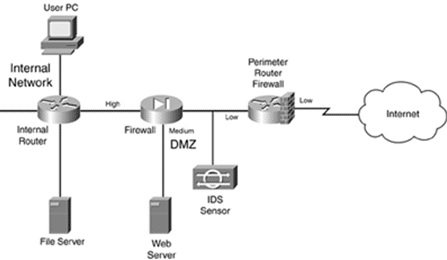
Components of a Firewall System
The components of firewall system are explained below −
Perimeter Router
It is used to provide a link to the public networking system like the internet, or a distinctive organization. It performs the routing of data packets with the help of an appropriate routing protocol. It also provides the filtering of packets and addresses translations.
Firewall
The provision of distinctive levels of security and supervises traffic among each level. Most of the firewalls are present near the router that provides security from external threats, but sometimes the firewall is present in the internal network to protect from internal attacks.
Virtual Private Network (VPN)
Its function is to provide a secure connection among two machines or networks. It consists of encryption, authentication, and packet-reliability assurance. It provides the secure remote access of the network, thereafter connecting two WAN networks on the same platform while not being physically connected.
Intrusion Detection System (IDS)
It is used to identify, investigate, and resolve unauthorized attacks. A hacker can attack the network in various ways. It can execute a denial-of-service (DoS) attack or an attack from the backside of the network through some unauthorized access. An IDS solution should be smart enough to deal with these types of attacks.
We all know that a firewall is a network security system that monitors and controls the incoming and outgoing network traffic on predetermined security rules. A firewall typically and controls the incoming and outgoing network traffic based on predetermined security rules.
The internet provides a two-way flow of traffic that may be undesirable in many organizations where some information may concern exclusively the organization or for the internet.
Internet is a TCP/IP network that is modelled after the internet that only works within the organizations to delineate information meant only for the benefit of organization to its internet and other open to all or meant for internet, some sorts of security measures need to be employed to control two-way flow of traffic.
Types of firewall architectures
There are three types of firewall architectures which are as follows −
- Packet filter
- Circuit filter
- Application level filter

