
- Cellular Concepts - Introduction
- GSM Architecture
- Cellular Concepts - GSM Radio Link
- Cellular Concepts - Mobility
- Cellular Concepts - GPRS
- Cellular Concepts - EDGE
- UMTS Introduction
- UMTS - A New Network
- UMTS - WCDMA Technology
- UMTS - HSPA Standardization
- UMTS - Objectives
- UMTS - Authentication
- UMTS - Success and Limitations
- UMTS Networks Standardization
- UMTS - 3GPP
- UMTS - Radio Access Network
- UMTS - Evolved Packet Core
- UMTS Protocol Environment
- UMTS - GPRS Tunneling Protocol
- UMTS - Proxy Mobile IPv6
- UMTS - EAP
- UMTS - IKEv2 & MOBIKE
- UMTS - SCTP
- UMTS - NAS Signaling Protocol
- UMTS Useful Resources
- UMTS - Quick Guide
- UMTS - Useful Resources
- UMTS - Discussion
Cellular Concepts - GSM Radio Link
BTS and MS are connected through radio links and this air interface is called the Um. A radio wave is subject to attenuation, reflection, Doppler shift, and interference from other transmitter. These effects cause loss of signal strength and distortion which impacts the quality of voice or data. To cope with the harsh conditions, GSM makes use of an efficient and protective signal processing. Proper cellular design must ensure that sufficient radio coverage is provided in the area.
The signal strength variation for mobile is due to the different types of signal strength fading. There are two types of signal strength variations.
Macroscopic Variations − Due to the terrain contour between BTS and MS. The fading effect is caused by shadowing and diffraction (bending) of the radio waves.
Microscopic variations − Due to multipath, Short-term or Rayleigh fading. As the MS moves, radio waves from many different path will be received.
Rayleigh Fading
Rayleigh Fading or Macroscopic Variations can be modeled as the addition of two components that make up the path loss between the mobile and the base station. The first component is the deterministic component (L) that adds loss to the signal strength as the distance (R) increases between the base and the mobile. This component can be written as −
L = 1/Rn
Where n is typically 4. The other macroscopic component is a Log normal random variable which takes into account the effects of shadow fading caused by variations in terrain and other obstructions in the radio path. Local mean value of path loss = deterministic component + log normal random variable.
Microscopic Variations or Rayleigh Fading occurs as the mobile moves over short distances compared to the distance between mobile and base. These short term variations are caused by signal scattering in the vicinity of the mobile unit say by a hill, a building, or traffic. This leads to many different paths that are followed between the transmitter and the receiver (Multipath Propagation). The reflected wave is altered in both phase and amplitude. The signal may effectively disappear if the reflected wave is 180 degree out of phase with the direct path signal. The partial out of phase relationships among multiple received signal produce smaller reduction in received signal strength.
Effects of Rayleigh Fading
Reflection and multipath propagation can cause positive and negative effects.
Transmitting/Receiving Processes
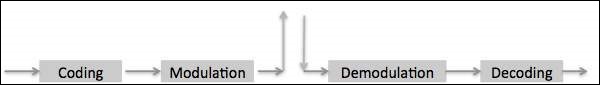
There are two major processes involved in transmitting and receiving information over a digital radio link, coding, and modulation.
Coverage Extension
Multipath propagation allows radio signals to reach behind hills and buildings and into tunnels. Constructive and destructive interference signals received through multi paths may add together or destroy each other.
Coding
Coding is the information processing that involves preparing the basic data signals so that they are protected and put in a form that the radio link can handle. Generally the coding process includes the Logical EXclusive OR (EXOR). Coding is included in −
- Speech coding or Trans coding
- Channel coding or Forward Error Correction coding
- Interleaving
- Encryption
Burst Formatting
Human speech is band limited between 300Hz to 3400Hz and undergoes Frequency Modulation in analog systems. In digital fixed PSTN systems band limited speech is sampled at the rate of 8KHz and each sampled is encoded into 8 bits leading to 64Kbps (PCM A-Law of encoding). Digital cellular radio cannot handle the high bit rate used for PSTN systems. Smart techniques for signal analysis and processing have been developed for reduction of the bit rate.
Speech Properties
Human speech can be distinguished in elementary sounds (Phonemes). Depending on the language, there are 30 to 50 different phonemes. The human voice is able to produce up to 10 phonemes per second, so that about 60 bit/s are required to transfer the speech. However, all individual features and intonations would disappear. To preserve the individual features, the real amount of information to be sent is a number of times higher, but still a fraction of the 64 Kbit/s used for PCM.
Based upon the phoneme production mechanism of the human organs of speech, a simple speech production model can be made. It appears that during a short time interval of 10-30 ms, the model parameters like pitch-period, voiced/unvoiced, amplification gain, and filter parameters remain about stationary (quasi stationary). The advantage of such a model is the simple determination of the parameters by means of linear prediction.
Speech Coding Techniques
There are 3 classes of speech coding techniques
Waveform Coding − Speech is transmitted as good as possible in wave form coding. PCM is an example of waveform coding. Bit rate ranges from 24 to 64kbps and the quality of speech is good and the speaker can be recognized easily.
Parameter Coding − Only a very limited quantity of information is sent. A decoder built up according to the speech production model will regenerate the speech at the receiver. Only 1 to 3kbps is required for the speech transmission. The regenerated speech is intelligible but it suffers from noise and often the speaker cannot be recognized.
Hybrid Coding − Hybrid Coding is a mix of waveform coding and parameter coding. It combines the strong points of both techniques and GSM uses a hybrid coding technique called RPE-LTP (Regular Pulse Excited-Long Term Prediction) resulting in 13Kbps per voice channel.
Speech Coding in GSM (Transcoding)
The 64kbits/s PCM transcoded from the standard A-law quantized 8bits per sample into a linearly quantized 13bits per sample bit stream that correspond to a 104kbits/s bit rate. The 104kbits/s stream is fed into the RPE-LTP speech encoder which takes the 13 bits samples in a block of 160 samples (every 20ms). RPE-LTP encoder produces 260bits in every 20 ms, resulting in a bit rate of 13kbits/s. This provides a speech quality acceptable for mobile telephony and comparable with wireline PSTN phones. In GSM 13Kbps speech coding is called full rate coders. Alternatively half rate coders (6.5Kbps) are also available to enhance the capacity.
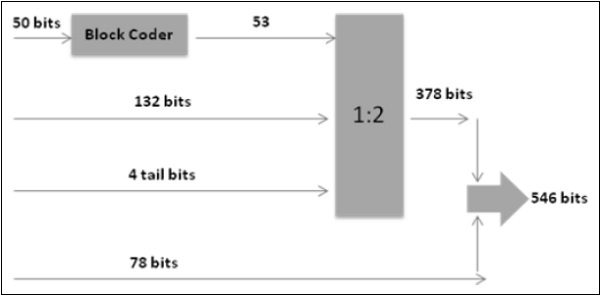
Channel Coding /Convolutional Coding
Channel coding in GSM uses the 260 bits from speech coding as input to channel coding and outputs 456 encoded bits. Out of the 260 bits produced by RPE-LTP speech coder, 182 are classified as important bits and 78 as unimportant bits. Again 182 bits are divided into 50 most important bits and are block coded into 53 bits and are added with 132 bits and 4 tail bits, totaling to 189 bits before undergoing 1:2 convolutional coding, converting 189 bits into 378 bits. These 378 bits are added with 78 unimportant bits resulting in 456 bits.
Interleaving - First Level
The channel coder provides 456 bits for every 20ms of speech. These are interleaved, forming eight blocks of 57 bits each, as shown in figure below.
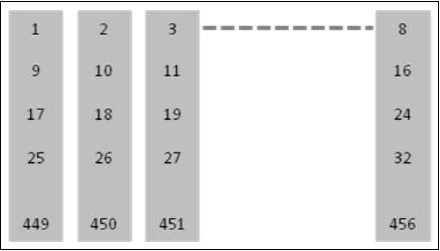
In a normal burst to blocks of 57 bits can be accommodated and if 1 such burst is lost there is a 25% BER for the entire 20ms.
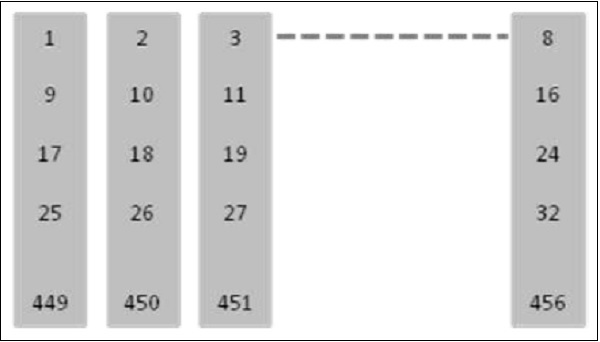
Interleaving - Second Level
A Second level of interleaving has been introduced to further reduce the possible BER to 12.5%. Instead of sending two blocks of 57 bits from the same 20 ms of speech within one burst, a block from one 20ms and a block from next sample of 20ms are sent together. A delay is introduced in the system when the MS must wait for the next 20ms of speech. However, the system can now afford to lose a whole burst, out of the eight, as the loss is only 12.5% of the total bits from each 20ms speech frame. 12.5% is the maximum loss level that a channel decoder can correct.
Encryption /Ciphering
The purpose of Ciphering is to encode the burst so that it may not be interpreted by any other devices than the receiver. The Ciphering algorithm in GSM is called the A5 algorithm. It does not add bits to the burst, meaning that the input and output to the Ciphering process is the same as the input: 456 bits per 20ms. Details about Encryption are available under the special features of GSM.
Multiplexing (Burst Formatting)
Every transmission from mobile/BTS must include some extra information along with basic data. In GSM, a total of 136 bits per block of 20ms are added bringing the overall total to 592 bits. A guard period of 33 bits is also added bringing 625 bits per 20ms.
Modulation
Modulation is the processing that involves the physical preparation of the signal so that the information can be transported on an RF carrier. GSM uses Gaussian Minimum Shift Keying technique (GMSK). Carrier frequency is shifted by +/- B/4, where B=Bit rate. However using the Gaussian filter, reduces the bandwidth to 0.3 instead of 0.5.
Special Features of GSM
Listed below are the special features of GSM that we are going to discuss in the following sections −
- Authentication
- Encryption
- Time Slot Staggering
- Timing Advance
- Discontinuous transmission
- Power Control
- Adoptive equalization
- Slow Frequency Hopping
Authentication
Since the air interface is vulnerable to fraudulent access, it is necessary to employ the authentication before extending the services to a subscriber. Authentication is built around the following notions.
Authentication Key (Ki) resides only in two places, SIM card and Authentication Center.
Authentication Key (Ki) is never transmitted over air. It is virtually impossible for unauthorized individuals to obtain this key to impersonate a given mobile subscriber.
Authentication Parameters
The MS is authenticated by the VLR with a process that uses three parameters −
RAND which is completely random number.
SRES which is an authentication signed response. It is generated by applying an authentication algorithm (A3) to RAND and Ki.
Kc which is cipher key. The Kc parameter generated by applying the cipher key generation algorithm (A8) to RAND and Ki.
These parameters (named an authentication triplet) are generated by the AUC at the request of the HLR to which the subscriber belongs. The algorithms A3 and A8, are defined by the PLMN operator and are executed by the SIM.
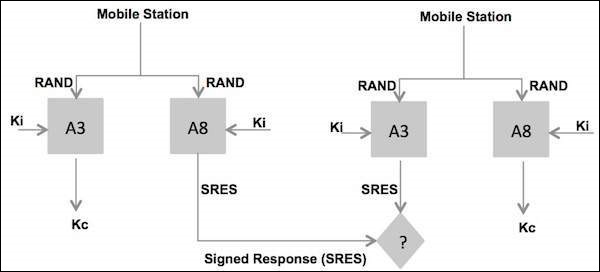
Steps in Authentication Phase
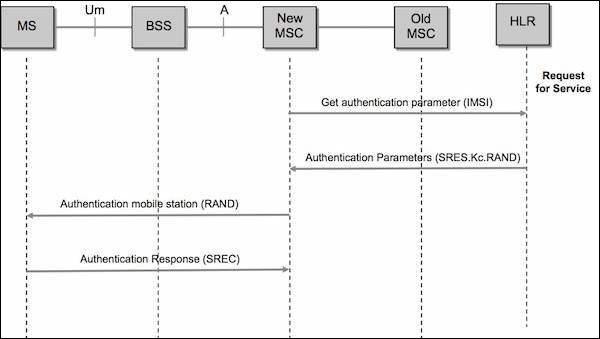
The new VLR sends a request to the HLR/AUC (Authentication Center) requesting the "authentication triplets" (RAND, SRES, and Kc) available for the specified IMSI.
The AUC using the IMSI, extracts the subscribers authentication key (Ki).The AUC then generates a random number (RAND), applies the Ki and RAND to both the authentication algorithm (A3) and the cipher key, generation algorithm (A8) to produce an authentication Signed Response (SRES) and a Cipher Key (Kc). The AUC then returns an authentication triplet: RAND, SRES and Kc to the new VLR.
The MSC/VLR keeps the two parameters Kc and SRES for later use and then sends a message to the MS. The MS reads its Authentication Key (Ki) from the SIM, applies the received random number (RAND) and Ki to both its authentication algorithm (A3) and Cipher key generation Algorithm (A8) to produce an Authentication Signed Response (SRES) and Cipher key (Kc). The MS saves Kc for later, and will use Kc when it receives command to cipher the channel.
The MS returns the generated SRES to the MSC/VLR. The VLR compares the SRES returned from the MS with the expected SRES received earlier from the AUC. If equal, the mobile passes authentication. If unequal, all signaling activities will be aborted. In this scenario, we will assume that authentication is passed.
Encryption/Ciphering
Data is encrypted at the transmitter side in blocks of 114 bits by taking 114-bit plain text data bursts and performing an EXOR (Exclusive OR) logical function operation with a 114-bit cipher block.
The decryption function at the receiver side is performed by taking the encrypted data block of 114 bits and going through the same "exclusive OR" operation using the same 114-bit cipher block that was used at the transmitter.
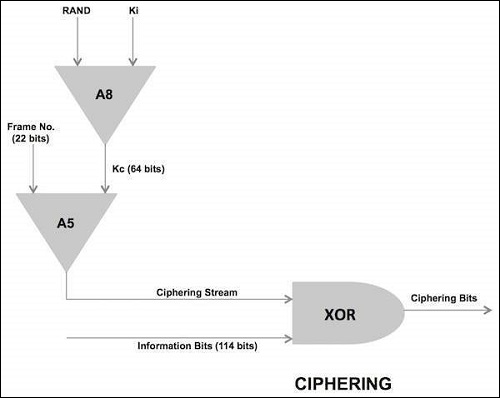
The cipher block used by both ends of transmission path for a given transmission direction is produced at the BSS and MS by an encryption algorithm called A5. The A5 algorithm uses a 64-bit cipher key (Kc), produced during the authentication process during call setup and the 22-bit TDMA frame number (COUNT) which takes decimal values from 0 through 2715647, and has a repetition time of 3.48 hours (hyper frame interval).The A5 algorithm actually produce two cipher blocks during each TDMA period. One path for the uplink path and the other for the downlink path.
Time Slot Staggering
Time slot staggering is the principle of deriving the time slot organization of uplink from the time slot organization of the downlink. A particular time slot of the uplink is derived from the downlink by shifting the downlink time slot number by three.
Reason
By shifting three time slots, the mobile station avoids the transmit and receive processes simultaneously. This allows an easier implementation of the mobile station; the receiver in the mobile station does not need to be protected from the transmitter of the same mobile station. Typically a mobile station will receive during one time slot, and then shifts in frequency by 45 MHz for GSM-900 or 95 MHz for GSM-1800 to transmit sometime later. This implies that there is one time base for downlink and one for uplink.
Timing Advance
Timing Advance is the process of transmitting the burst to the BTS (the timing advance) early, to compensate for the propagation delay.
Why is it Needed?
It is required because of the time division multiplexing scheme used on the radio path. The BTS receives signals from different mobile stations very close to each other. However when a mobile station is far from the BTS, the BTS must deal with the propagation delay. It is essential that the burst received at the BTS fits correctly into time slot. Otherwise the bursts from the mobile stations using adjacent time slots could overlap, resulting in a poor transmission or even in loss of communication.
Once a connection has been established, the BTS continuously measures the time offset between its own burst schedule and the reception schedule of the mobile station burst. Based on these measurements, the BTS is able to provide the mobile station with the required timing advance via the SACCH. Note that timing advance is derived from the distance measurement which is also used in the handover process. The BTS sends a timing advance parameter according to the perceived timing advance to each mobile station. Each of the mobile station then advances its timing, with the result that signals from the different mobile stations arriving at BTS, and are compensated for propagation delay.
Time Advance Process
A 6 bit number indicates how many bits the MS must advance its transmission. This time advance is TA.
The 68.25 bit long GP (guard period) of the access burst provides the required flexibility to advance the transmission time.
The time advance TA can have a value between 0 and 63 bits long, which corresponds to a delay of 0 to 233 micro second. For instance the MS at 10 km away from the BTS must start transmitting 66 micro second earlier to compensate for the round trip delay.
The maximum mobile range of 35Km is rather determined by the timing advance value than by the signal strength.