
- Cyber Security - Home
- Cyber Security - Introduction
- Cyber Security - History
- Basics of Cyber Technology
- Cyber Security - Aims and Goals
- Types of Cyber Attacks
- Cyber Security - Keyloggers
- Cyber Security - Dark Web
- Cyber Security - Technologies
- Cyber Security - VPN
- Cyber Security - Policies
- Cyber Security - Standards
- Cyber Security - Tools
- Cyber Security - Challenges
- Cyber Security - Risk Analysis
- Cyber Security - Applications
- Cyber Security - Emerging Trends
Cybersecurity - Tools
With the increase in the number of cyberattacks all around the globe and the increasing need for cybersecurity measures, many tools, and defensive mechanisms have been developed to counter such attacks. These attacks, along with the standards and policies, form the defensive corridor of cybersecurity systems in general.

Cybersecurity tools are used regularly in all areas, ranging from personal computers on a small scale to a company network on a large scale. These help the owners defend their systems from attacks committed by cybercriminals and hackers. So, lets discuss some important cybersecurity tools and mechanisms.
Important Cybersecurity Tools
Some of the most important and widely-used cybersecurity tools are given as follows −
- Antivirus
- Malware Removal
- Penetration Testing
- Public Key Infrastructure
- Endpoint Protection Platforms
- Managed Detection and Response
Antivirus Software
Antivirus software is the most widely used cybersecurity tool. It is designed to protect the systems from different malicious programs which include Virus, Worm, Trojan, Spyware, and many others. This detection and protection helps prevent any data theft or illegal access to organizational assets.

The following features are present in antivirus software which makes it a very valuable tool in the cybersecurity ecosystem −
- Continuous Tracking
- Signature Detection
- Behavior Analysis
- Cloud Scanning
- Self-defense
Malware Removal
Similar to an antivirus, malware removal software is used to remove malware programs that may have arrived in the computer system from a potential cybercriminal.
These work in the following steps −
- Start your computer in Safe Mode
- Delete all temporary files and folders
- Stop any malware process related using CLI
- Download a malware scanner and start the scan.
Penetration Testing
Penetration Testing is a very popular way to detect and manage any intrusion into the system of an organization. It is also known as a Pen Test. In this, the organization tests the cybersecurity system internally by conducting a self-created attack on the system, and this way, all major loopholes and vulnerable areas are exposed and identified by the cybersecurity team of the organization.
The following are the seven steps of penetration testing −
- Planning and Preparation
- Reconnaissance
- Discovery
- Analyzing Information and Risks
- Active Intrusion Attempts
- Final Analysis
- Report Preparation
Public Key Infrastructure
Public key infrastructure (PKI) is a set of tools that are used to generate and use public keys for encryption. As studied in earlier chapters, Encryption is a very important method to secure data that is transferred via networks. Nowadays, PKI finds applications in almost all web browsers, and it helps to secure public networks and traffic.

The main components of a Public Key Infrastructure are listed as follows −
- Public Key Certificate, commonly referred to as digital certificate
- Private Key tokens
- Certification Authority
- Registration Authority
- Certificate Management System
Endpoint Protection Platforms
An endpoint protection platform (EPP) is a software mechanism used on endpoint devices to protect them from malware and cyberattacks. This detects any malicious activity on the device and provides an in-detail analysis of the incident. It also suggests response strategies that guide the user to a better response to the cyberattack.
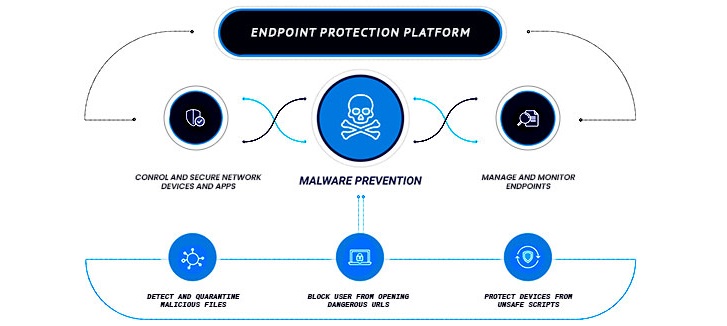
The EPP systems work using a step-by-step process listed in the following section −
- Real-Time Scanning
- Intrusion Prevention
- Data Loss Prevention (DLP)
- Application Management
- Patch Control
- Centralized Analysis
- Threat Detection
- Cloud Integration