
 Data Structure
Data Structure Networking
Networking RDBMS
RDBMS Operating System
Operating System Java
Java MS Excel
MS Excel iOS
iOS HTML
HTML CSS
CSS Android
Android Python
Python C Programming
C Programming C++
C++ C#
C# MongoDB
MongoDB MySQL
MySQL Javascript
Javascript PHP
PHP
- Selected Reading
- UPSC IAS Exams Notes
- Developer's Best Practices
- Questions and Answers
- Effective Resume Writing
- HR Interview Questions
- Computer Glossary
- Who is Who
Multiple Access with Collision Avoidance (MACA)
Multiple Access with Collision Avoidance (MACA) is a medium access control (MAC) layer protocol used in wireless networks, with a view to solve the hidden terminal problem. It also provides solution to the exposed terminal problem. The MAC layer protocol IEEE 802.11 RTS/CTS has been adopted from MACA.
Working Principle
The MACA protocol works with the condition that the stations are synchronized and frame sizes and data speed are the same. It involves transmission of two frames called RTS and CTS prior to data transmission. RTS stands for Request to Send and CTS stands for Clear to Send.
Let us consider that a transmitting station STA has data frame to send to a receiving station STB. The operation works as follows:
Station STA sends a RTS frame to the receiving station.
On receiving the RTS, station STB replies by sending a CTS frame.
On receipt of CTS frame, station STA begins transmitting its data frame.
After successful receipt of the data frame, station STB sends an ACK frame (acknowledgement frame).
The sequence is illustrated as follows:
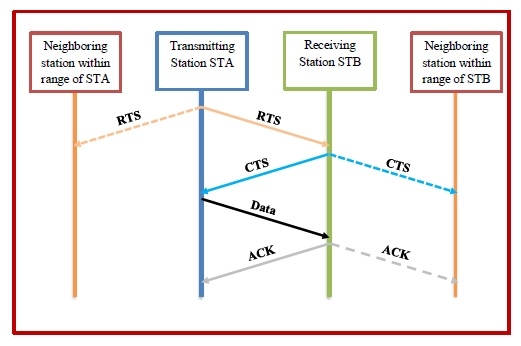
Any station than can hear RTS is close to the transmitting station and remains silent long enough for the CTS, or waits for a certain time period. If the RTS is not followed by a CTS, the maximum waiting time is the RTS propagation time.
Any station that can hear the CTS is close to the receiving station and remains silent during the data transmission. It attempts for transmission after hearing the ACK.
MACA is a non-persistent slotted protocol. This implies that if the medium is detected as busy, a station waits for a random time period after the beginning of a time slot and then it sends an RTS. This assures fair access to the medium.

